SC-100 Exam Questions & Answers
Vendor: Microsoft
Certifications: Microsoft Certifications
Exam Code: SC-100
Exam Name: Microsoft Cybersecurity Architect
Updated:
Q&As: 251 ( View Details)
Note: Product instant download. Please sign in and click My account to download your product.
The SC-100 Questions & Answers covers all the knowledge points of the real exam. We update our product frequently so our customer can always have the latest version of the brain dumps. We provide our customers with the excellent 7x24 hours customer service. We have the most professional expert team to back up our grate quality products. If you still cannot make your decision on purchasing our product, please try our free demo.

Download Free Microsoft SC-100 Demo
Experience
Pass4itsure.com exam material in PDF version.
Simply submit your e-mail address below to get
started with our PDF real exam demo of your
Microsoft SC-100 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Microsoft SC-100 Last Month Results
Free SC-100 Exam Questions in PDF Format
SC-100 Online Practice Questions and Answers
HOTSPOT
You need to recommend a security methodology for a DevOps development process based on the Microsoft Cloud Adoption Framework for Azure.
During which stage of a continuous integration and continuous deployment (CI/CD) DevOps process should each security-related task be performed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
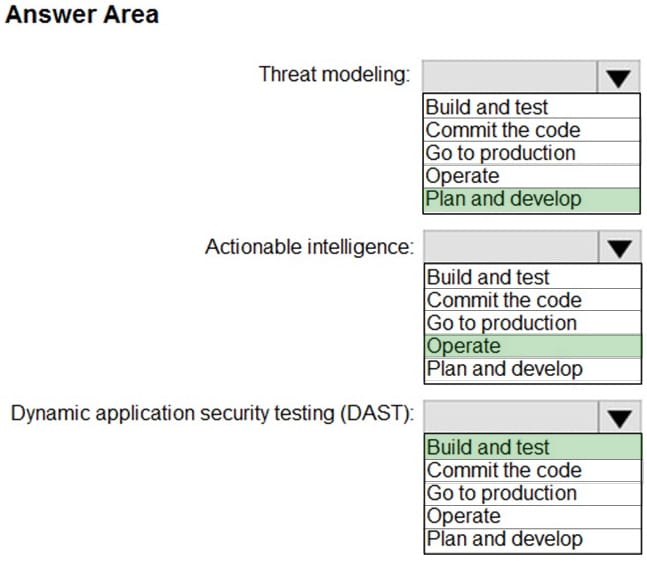

Plan and develop
Box 1: Plan and develop
Typically, modern development follows an agile development methodology. Scrum is one implementation of agile methodology that has every sprint start with a planning activity. Introducing security into this part of the development process should focus on:
*
Threat modeling to view the application through the lens of a potential attacker
*
IDE security plug-ins and pre-commit hooks for lightweight static analysis checking within an integrated development environment (IDE).
*
Peer reviews and secure coding standards to identify effective security coding standards, peer review processes, and pre-commit hooks. It's not mandatory to add all these steps. But each step helps reveal security issues early, when they're much cheaper and easier to fix.
Box 2: Operate
Go to production and operate
When the solution goes to production, it's vital to continue overseeing and managing the security state. At this stage in the process, it's time to focus on the cloud infrastructure and overall application.
Configuration and infrastructure scanning
Penetration testing
Actionable intelligence
The tools and techniques in this guidance offer a holistic security model for organizations who want to move at pace and experiment with new technologies that aim to drive innovation. A key element of DevSecOps is data-driven, event-driven
processes. These processes help teams identify, evaluate, and respond to potential risks. Many organizations choose to integrate alerts and usage data into their IT service management (ITSM) platform. The team can then bring the same
structured workflow to security events that they use for other incidents and requests.
Box 3: Build and test
Build and test
Many organizations use build and release pipelines to automate and standardize the processes for building and deploying code. Release pipelines let development teams make iterative changes to sections of code quickly and at scale. The
teams won't need to spend large amounts of time redeploying or upgrading existing environments.
Using release pipelines also lets teams promote code from development environments, through testing environments, and ultimately into production. As part of automation, development teams should include security tools that run scripted,
automated tests when deploying code into testing environments. The tests should include unit testing on application features to check for vulnerabilities or public endpoints. Testing ensures intentional access.
Dynamic application security testing (DAST)
In a classical waterfall development model, security was typically introduced at the last step, right before going to production. One of the most popular security approaches is penetration testing or pen testing. Penetration testing lets a team
look at the application from a black-box security perspective, as in, closest to an attacker mindset.
Reference:
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/secure/devsecops-controls
https://learn.microsoft.com/en-us/security/benchmark/azure/mcsb-devops-security
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
A. Apply read-only locks on the storage accounts.
B. Set the AllowSharcdKeyAccess property to false.
C. Set the AllowBlobPublicAcccss property to false.
D. Configure automated key rotation.
Correct Answer: A
A read-only lock on a storage account prevents users from listing the account keys. A POST request handles the Azure Storage List Keys operation to protect access to the account keys. The account keys provide complete access to data in
the storage account.
Incorrect:
Not A:
If any clients are currently accessing data in your storage account with Shared Key, then Microsoft recommends that you migrate those clients to Azure AD before disallowing Shared Key access to the storage account.
However, in this scenario we cannot migrate to Azure AD due to the legacy applications.
Note: Shared Key
A shared key is a very long string. You can simply access Azure storage by using this long string. It's almost like a password. Actually, it's worse: this is a master password. It gives you all sorts of rights on the Azure storage account. You can
imagine why this isn't my favorite mechanism of accessing Azure storage. What happens when this key is compromised? You don't get an alert. Perhaps you can set up monitoring to see misuse of your Azure storage account. But it's still less
than an ideal situation. Alerts will tell you of damage after it has already occurred.
Not C: Data breaches caused by cloud misconfiguration have been seen for the past few years. One of the most common misconfigurations is granting public access to cloud storage service. Such a data is often unprotected, making them to
be accessed without any authentication method. Microsoft recently introduced a new protection feature to help avoid public access on storage account. The feature introduces a new property named allowBlobPublicAccess.
Not D: Key rotation would improve security.
Automated key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency.
You can use rotation policy to configure rotation for each individual key. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
This feature enables end-to-end zero-touch rotation for encryption at rest for Azure services with customer-managed key (CMK) stored in Azure Key Vault.
Reference: https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
https://docs.microsoft.com/en-us/azure/storage/common/shared-key-authorization-prevent
https://docs.microsoft.com/en-us/azure/key-vault/keys/how-to-configure-key-rotation
Your company has a Microsoft 365 E5 subscription.
The company wants to identify and classify data in Microsoft Teams, SharePoint Online, and Exchange Online.
You need to recommend a solution to identify documents that contain sensitive information.
What should you include in the recommendation?
A. data classification content explorer
B. data loss prevention (DLP)
C. eDiscovery
D. Information Governance
Correct Answer: B
Data loss prevention (DLP)
With DLP policies, you can identify, monitor, and automatically protect sensitive information across Office 365. Data loss prevention policies can use sensitivity labels and sensitive information types to identify sensitive information.
Note: Microsoft 365 includes many sensitive information types that are ready for you to use in DLP policies and for automatic classification with sensitivity and retention labels.
Incorrect:
Not A: Content explorer shows a current snapshot of the items that have a sensitivity label, a retention label or have been classified as a sensitive information type in your organization.
Reference: https://docs.microsoft.com/en-us/security/compass/information-protection-and-storage-capabilities https://docs.microsoft.com/en-us/microsoft-365/compliance/data-classification-content-explorer
Add Comments
What Our Customers Are Saying
saini
Australiai really love this dumps, update quickly and content completely. it is enough for my exam. Recommend.
Tom
United StatesRecommend this dumps to you strongly, really useful and convenient.
Anna
JapanPassed exam today with 989/1000. All questions were from this dumps. It's 100% valid. Special thanks to my friend Lily.
Zard
Jordanthis file is so much valid, i passed the exam successfully. thanks for my friend introduce this dumps to me.
Kim
CambodiaI appreciated this dumps not only because it helped me pass the exam, but also because I learned much knowledge and skills. Thanks very much.
zewpy
BrazilI used it,I passed. I found same questions..but it's not the same orderl, be careful.
Bain
South KoreaVery good dumps. If you want to pass your exam, you can try it and I think you can pass your exam as long as you take full use of this dumps. Good luck to you.
zmaster2
SpainI knew this dumps by accident. One month ago, I searched on the Internet and found this material. At first, I didn't dare to pay much attention on this material and also brought many other material. But when i used all the materials I brought , I found that there are many new questions and the answers are or accurate in this material.Gradually,I payed more attention on this material and at last I only used this material. Today I have cleared that I passed the exam with high score. So I recommend this material strongly.
Talon
United StatesStill valid!! 97%
shok
AustraliaYes this valid. Passed today 982/1000. Same questions.
Related ExamsRelated Certifications
-
- 62-193 Technology Literacy for Educators
- 70-243 Administering and Deploying System Center 2012 Configuration...
- 70-355 Universal Windows Platform – App Data, Services, and Codin...
- 77-420 Excel 2013
- 77-427 Excel 2013 Expert Part One
- 77-725 Word 2016 Core Document Creation, Collaboration and Communic...
-
- Fundamentals
- Microsoft Certified: Azure Administrator Associate
- Role-based
- Microsoft Certified: Azure Fundamentals
- Microsoft Certified: Azure Security Engineer Associate
- Microsoft 365 Certified: Modern Desktop Administrator Associate
- Microsoft 365 Certified: Enterprise Administrator Expert
- Microsoft Certified: Power Platform Functional Consultant Associate
QAS
+ What type of exam materials available on Pass4itsure.com ?
All the products and all the demos on Pass4itsure.com are in PDF version which designed exactly according to the real exam questions and answers. We have free demos for almost all of our products and you can try our demos before buying.
+ Does your study material work?
All the latest Q&As are created directly correspond to the real questions and answers by professionals and ensured by experts to guarantee the accuracy. If you understand the knowledge points provided in our Q&As, you can pass the exam easily.
+ How often do you release your products updates?
All the products are updated frequently but not on a fixed date. Our professional team pays a great attention to the exam updates and they always upgrade the content accordingly.
+ Are the update free?
The free update offer is only valid for one year after you've purchased the products. If you still want to update your questions after one year, login your account in our site, and you can get the new one with 50% discounts.
+ When I can download the products and how to download it?
After your order has been confirmed, you will be able to download the product instantly. You need to log in your account-click My Account-click the Invoice or Detail, then you will go to the download page. Click the download button to download the product.If it shows "Exam updating. Please download it later." It means there are latest updates for your exam and our expert team is revising the exam. We will send you it via email or you may download it later.
+ When does my product validation period expire?
You can enjoy one year free update after your purchase.
+ How to extend my expired product?
Product validation period cannot be extended. But you can renew your product. Please login your account and click the 'Renew' button next to each expired product in your User Center. Renewal of expired product is 50% of the original price and you can use it for another one year.
+ What operating systems and necessary tools are needed to use your product?
For Lab user, Adobe Reader and AVI player are required.
+ What unzipping software do you recommend?
Set WinZip as your primary decompress tools which you can download at http://www.winzip.com.
+ How do I pay for my order?
We currently only accepts payments with PayPal (www.paypal.com).
+ If I can’t login my account or forgot my password, what should I do?
You may contact us to report the case and we will help you to reset your password.
+ What do you do with my personal information?
We respect your privacy and, therefore, we do not sell or rent the personal information you provide to us to any third party you do not wish us to do so. Upon your request, we will not share your personal information with any unaffiliated third party. One of our highest priorities is to ensure your privacy and peace of mind by employing some of the most advanced online security in the industry. Every step of the way, we provide you with the state-of-the-art encryption of all data transmitted between your computer and our secure site.
+ It seems that I was charged differently from my bill?
We use the US dollar as the currency in most of our transaction and if you paid in other currency such as Pound, Euro or any other, they will be converted using our real –time currency exchange, so there may be different of your bill.
+ Are there any extra fees I need to pay?
We do not charge any extra fee. But you may be charged the transaction fee by your bank. You can contact your bank to make sure. We do not take any extra money from our customers.
+ Do you have any coupons?
We offer some discounts to our customers. There is no limit to some special discount. You can check regularly of our site to get the coupons.
Why Choose Pass4itsure.com
-
Do you maintain 100% Guarantee on Pass4itsure.com products?
Yes. Our PDF of SC-100 exam is designed to ensure everything which you need to pass your exam successfully. At Pass4itsure.com, we have a completely customer oriented policy. We invite the rich experience and expert knowledge of professionals from the IT certification industry to guarantee the PDF details precisely and logically. Our customers' time is a precious concern for us. This requires us to provide you the products that can be utilized most efficiently.
-
Do you offer free after-sale services?
Yes. We provide 7/24 customer help and information on a wide range of issues. Our service is professional and confidential and your issues will be replied within 12 hous. Feel free to send us any questions and we always try our best to keeping our Customers Satisfied.
-
Do you provide free updates?
Yes, once there are some changes on SC-100 exam, we will update the study materials timely to make sure that our customer can download the latest edition. The updates are provided free for 120 days.
-
What if I don't pass the exam? How do I claim Refund?
Any Pass4itsure.com user who fails the corresponding exam has 30 days from the date of purchase of Exam on Pass4itsure.com for a full refund. We can accept and arrange a full refund requests only if your score report or any relevant filed be confirmed.

Home | Contact Us | About Us | FAQ | Guarantee & Policy | Privacy & Policy | Terms & Conditions | How to buy
Copyright © 2025 pass4itsure.com. All Rights Reserved


 Printable PDF
Printable PDF