SC-100 Online Practice Questions and Answers
HOTSPOT
Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation.
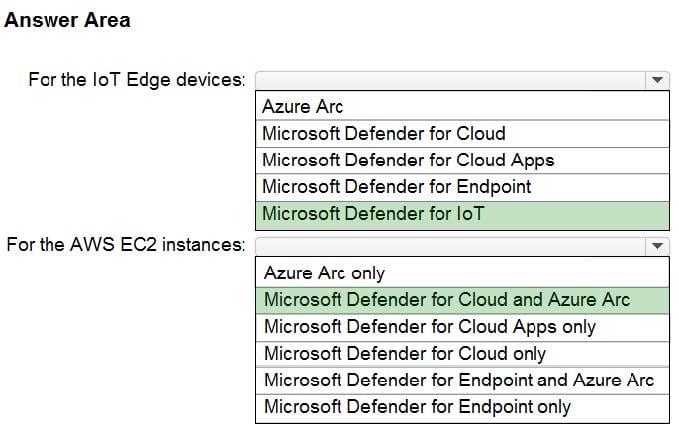
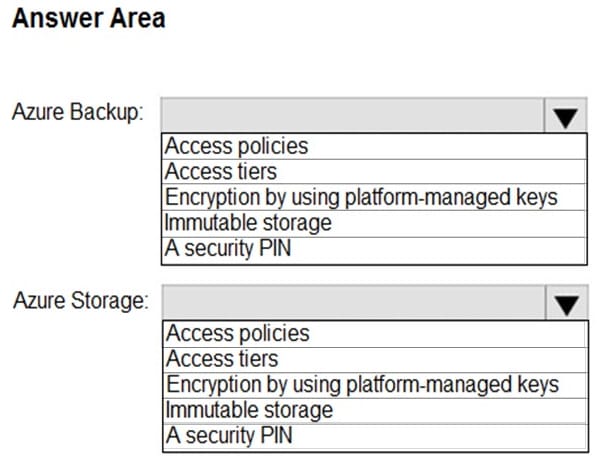
You need to recommend a security posture management solution for the following components:
1.
Azure IoT Edge devices
2.
AWS EC2 instances
Which services should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

HOTSPOT
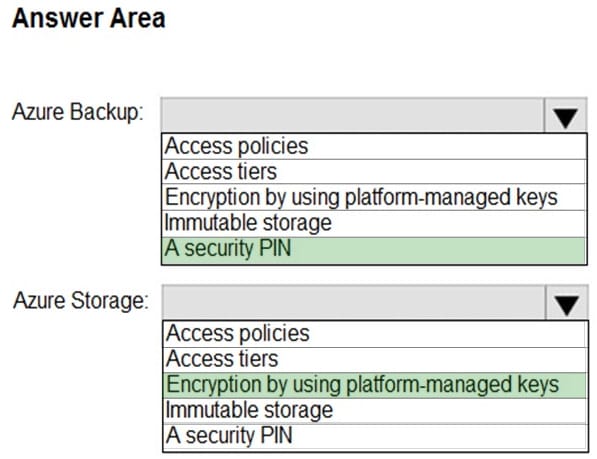
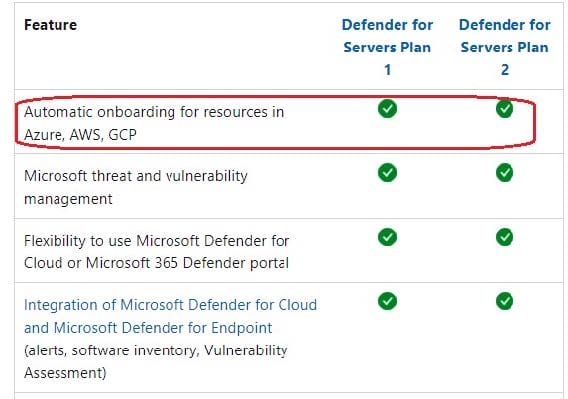
Your company wants to optimize using Azure to protect its resources from ransomware.
You need to recommend which capabilities of Azure Backup and Azure Storage provide the strongest protection against ransomware attacks. The solution must follow Microsoft Security Best Practices.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
DRAG DROP
Your company has Microsoft 365 E5 licenses and Azure subscriptions.
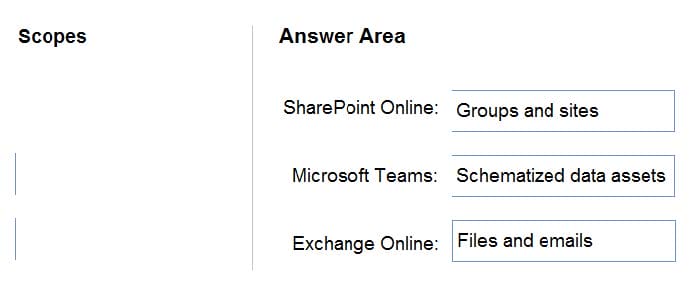
The company plans to automatically label sensitive data stored in the following locations:
1.
Microsoft SharePoint Online
2.
Microsoft Exchange Online
3.
Microsoft Teams You need to recommend a strategy to identify and protect sensitive data. Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may only be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:

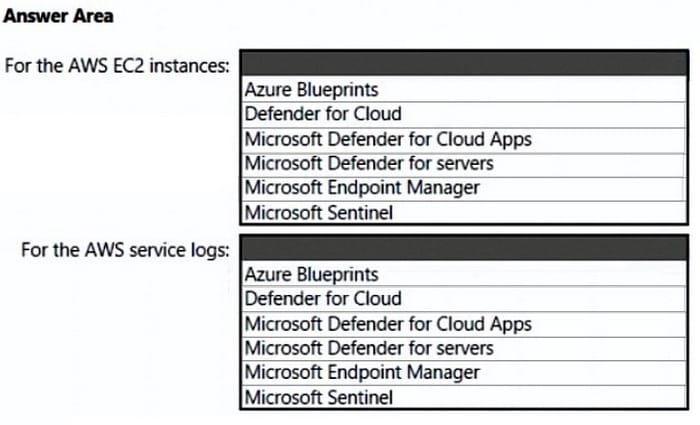
HOTSPOT
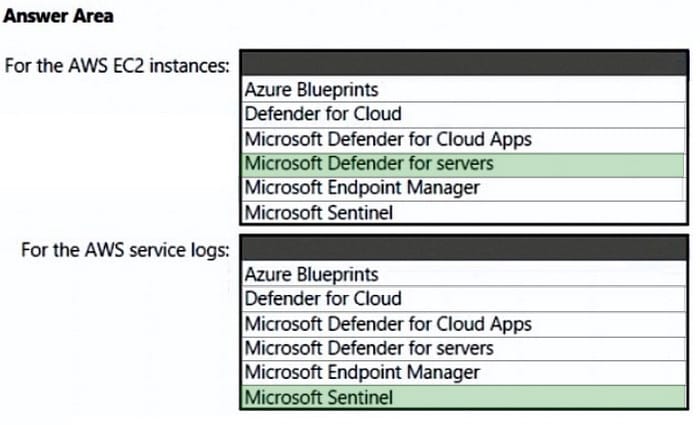
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service.
You are migrating the on- premises infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
A. Azure AD B2C
B. Azure Active Directory Domain Services (Azure AD DS)
C. Azure AD
D. Active Directory Domain Services (AD DS)
Your company has devices that run either Windows 10, Windows 11, or Windows Server.
You are in the process of improving the security posture of the devices.
You plan to use security baselines from the Microsoft Security Compliance Toolkit.
What should you recommend using to compare the baselines to the current device configurations?
A. Microsoft Intune
B. Local Group Policy Object (LGPO)
C. Windows Autopilot
D. Policy Analyzer
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are designing the encryption standards for data at rest for an Azure resource.
You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses customer-managed keys (CMKs).
Does this meet the goal?
A. Yes
B. No
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each NOTE: Each correct selection is worth one point.
A. Azure Firewall
B. Azure Web Application Firewall (WAF)
C. Microsoft Defender for Cloud alerts
D. Azure Active Directory (Azure AD Privileged Identity Management (PIM)
E. Microsoft Sentinel
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator
authorizes the application.
Which security control should you recommend?
A. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
B. Azure AD Conditional Access App Control policies
C. adaptive application controls in Defender for Cloud
D. app protection policies in Microsoft Endpoint Manager
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled.
The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019.
You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator
authorizes the application.
Which security control should you recommend?
A. app registrations in Azure AD
B. application control policies in Microsoft Defender for Endpoint
C. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
D. Azure AD Conditional Access App Control policies