XK0-004 Online Practice Questions and Answers
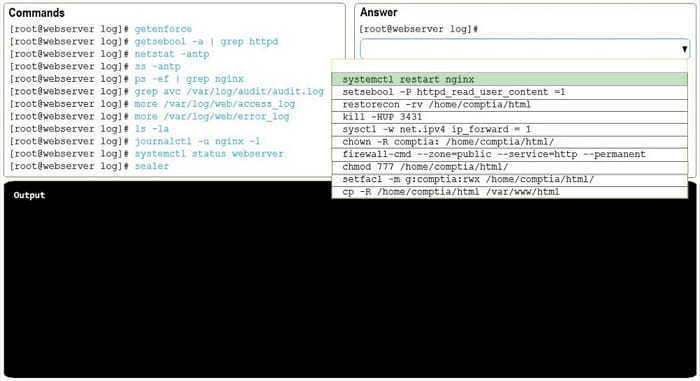
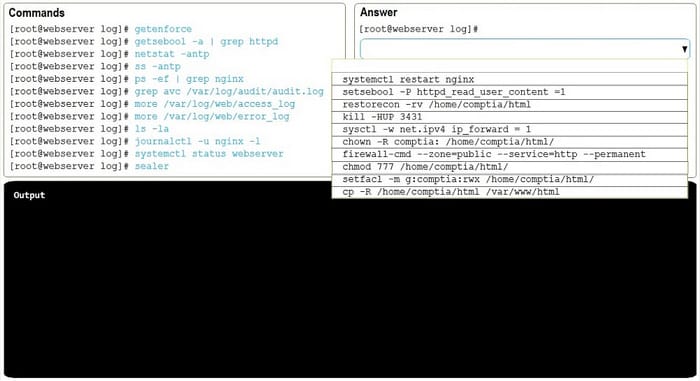
HOTSPOT
After installing a new web server, you are unable to browse to the default web page.
INSTRUCTIONS
Review all the command output and select the command needed to remediate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
An administrator is attempting to block SSH connections to 192.168.10.24 using the Linux firewall. After implementing a rule, a connection refused error is displayed when attempting to SSH to 192.168.10.24. Which of the following rules was MOST likely implemented?
A. iptables -A -p tcp -d 192.168.10.24 --dport 22 -j REJECT
B. iptables -A -p tcp -d 192.168.10.24 --dport 22 -j DROP
C. iptables -A -p tcp -d 192.168.10.24 --dport 22 -j FORWARD
D. iptables -A -p tcp -d 192.168.10.24 --dport 22 -j REFUSE
A Linux systems administrator needs to provision multiple web servers into separate regional datacenters. The systems architect has instructed the administrator to define the server infrastructure using a specific tool that consumes a text-based file.
Which of the following is the BEST reason to do this?
A. To document the infrastructure so it can be included in the system security plan
B. To ensure the administrator follows the planning phase of the systems development life cycle
C. To define the infrastructure so it can be provisioned consistently with minimal manual tasks
D. To validate user requirements have been met within each regional datacenter for compliance
A systems administrator has received reports of intermittent network connectivity to a particular website. Which of the following is the BEST command to use to characterize the location and type of failure over the course of several minutes?
A. mtr www.comptia.org
B. tracert www.comptia.org
C. ping www.comptia.org
D. netstat www.comptia.org
An operator finds a user is having issues with opening certain files.
Which of the following commands would allow the security administrator to list and check the SELinux context?
A. ls -D
B. ls -a
C. ls -Z
D. ls -1
A junior systems administrator is creating a cron job. The cron job requirements are as follows:
1.
Run the hello.sh script every hour (24 times in one day).
2.
Run it on Monday only.
Given this scenario, which of the following crontab options should be configured to meet these requirements?
A. 0 *** 1 hello.sh
B. 0 24 ** Monday hello.sh
C. 24 *** Monday hello.sh
D. 1 *** 0 hello.sh
A Linux administrator looks at the /etc/timezone file and determines the need to change the time zone from California to New York temporarily. Which of the following commands will accomplish this?
A. sed -f TZ=America/New_York
B. cat TZ=America/New_York
C. export TZ=America/New_York
D. printf TZ=America/New_York
A junior administrator is configuring local name lookups for fully qualified domain names in an isolated environment. The administrator is given a checklist and must accomplish the following tasks:
1.
Add localhost with loopback address.
2.
Add 192.168.192.12/24 to resolve to database01.comptia.org
Given this scenario, which of the following steps should the administrator perform to accomplish these tasks?
A. Open the /etc/nsswitch.conf file with a file editor and add the following lines:
127.0.0.1 localhost
192.168.192.12 database01.comptia.org
B. Open the /etc/dhcpd.conf file with a file editor and add the following lines:
127.0.0.1 localhost
192.168.192.12 database01.comptia.org
C. Open the /etc/hosts file with a file editor and add the following lines:
127.0.0.1 localhost
192.168.192.12 database01.comptia.org
D. Open the /etc/network file with a file editor and add the following lines:
127.0.0.1 localhost
192.168.192.12 database01.comptia.org
A Linux administrator receives a call from the network operations team that one of the database applications is down on a Linux server. The Linux server is configured with RAID 1 for redundancy, and the array /dev/md0 consists of two devices called /dev/sda1 and /dev/sdb1. After looking at the status of the RAID 1 array in the /proc/mdstat file, the administrator discovers the RAID 1 array is degraded and the disk /dev/sdb1 on which the database application was installed appears to have failed.
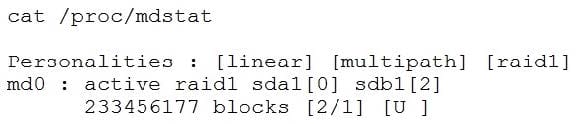
Which of the following steps should the administrator take to remove the device /dev/sdb1 from the RAID array md0? (Choose two.)
A. mdadm /dev/md0 --remove /dev/sdb1
B. mdadm /dev/sdb1 --fail /dev/md0
C. mdadm /dev/md0 --fail /dev/sdb1
D. mdadm /dev/sdb1 --remove /dev/md0
E. racadm --remove /dev/sdb1
F. racadm --fail /dev/sdb1
A Linux user uses a VPN to securely access the company's systems from a laptop.
Which of the following protocols are MOST likely used to secure the VPN connection? (Choose two.)
A. IPSec
B. HTTP
C. SFTP
D. VNC
E. SSL/TLS
F. SELinux