VAULT-ASSOCIATE Online Practice Questions and Answers
What is the Vault CLI command to query information about the token the client is currently using?
A. vault lookup token
B. vault token lookup
C. vault lookup self
D. vault self-lookup
Examine the command below. Output has been trimmed.
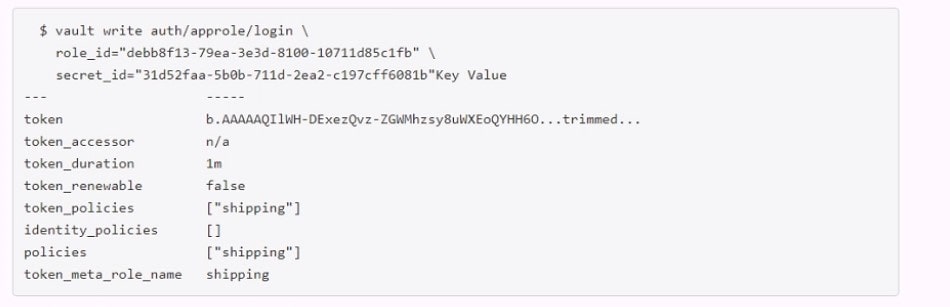
Which of the following statements describe the command and its output?
A. Missing a default token policy
B. Generated token's TTL is 60 hours
C. Generated token is an orphan token which can be renewed indefinitely
D. Configures the AppRole auth method with user specified role ID and secret ID
An organization wants to authenticate an AWS EC2 virtual machine with Vault to access a dynamic database secret. The only authentication method which they can use in this case is AWS.
A. True
B. False
When looking at Vault token details, which key helps you find the paths the token is able to access?
A. Meta
B. Path
C. Policies
D. Accessor
The following three policies exist in Vault. What do these policies allow an organization to do?
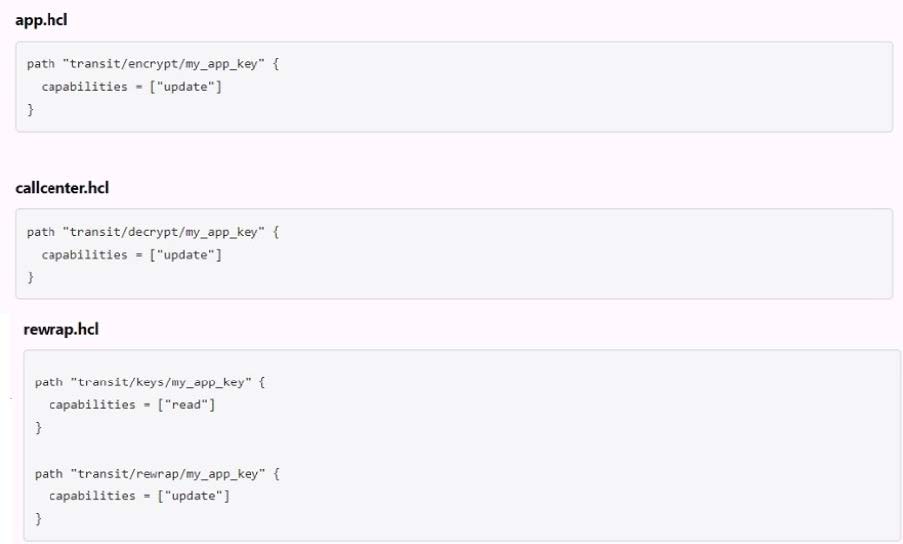
A. Separates permissions allowed on actions associated with the transit secret engine
B. Nothing, as the minimum permissions to perform useful tasks are not present
C. Encrypt, decrypt, and rewrap data using the transit engine all in one policy
D. Create a transit encryption key for encrypting, decrypting, and rewrapping encrypted data
Vault supports which type of configuration for source limited token?
A. Cloud-bound tokens
B. Domain-bound tokens
C. CIDR-bound tokens
D. Certificate-bound tokens
Which of the following vault lease operations uses a lease_id as an argument? Choose two correct answers.
A. renew
B. revoke -prefix
C. create
D. describe
E. revoke
What are orphan tokens?
A. Orphan tokens are tokens with a use limit so you can set the number of uses when you create them
B. Orphan tokens are not children of their parent; therefore, orphan tokens do not expire when their parent does
C. Orphan tokens are tokens with no policies attached
D. Orphan tokens do not expire when their own max TTL is reached
When using Integrated Storage, which of the following should you do to recover from possible data loss?
A. Failover to a standby node
B. Use snapshot
C. Use audit logs
D. Use server logs
When an auth method is disabled all users authenticated via that method lose access.
A. True
B. False

