SOA-C02 Online Practice Questions and Answers
A SysOps administrator noticed that the cache hit ratio for an Amazon CloudFront distribution is less than 10%.
Which collection of configuration changes will increase the cache hit ratio for the distribution? (Select TWO.)
A. Ensure that only required cookies, query strings, and headers are forwarded in the Cache Behavior Settings.
B. Change the Viewer Protocol Policy to use HTTPS only.
C. Configure the distribution to use presigned cookies and URLs to restrict access to the distribution.
D. Enable automatic compression of objects in the Cache Behavior Settings.
E. Increase the CloudFront time to live (TTL) settings in the Cache Behavior Settings.
A SysOps administrator must create a solution that immediately notifies software developers if an AWS Lambda function experiences an error.
Which solution will meet this requirement?
A. Create an Amazon Simple Notification Service (Amazon SNS) topic with an email subscription for each developer. Create an Amazon CloudWatch alarm by using the Errors metric and the Lambda function name as a dimension. Configure the alarm to send a notification to the SNS topic when the alarm state reaches ALARM.
B. Create an Amazon Simple Notification Service (Amazon SNS) topic with a mobile subscription for each developer. Create an Amazon EventBridge (Amazon CloudWatch Events) alarm by using LambdaError as the event pattern and the SNS topic name as a resource. Configure the alarm to send a notification to the SNS topic when the alarm state reaches ALARM.
C. Verify each developer email address in Amazon Simple Email Service (Amazon SES). Create an Amazon CloudWatch rule by using the LambdaError metric and developer email addresses as dimensions. Configure the rule to send an email through Amazon SES when the rule state reaches ALARM.
D. Verify each developer mobile phone in Amazon Simple Email Service {Amazon SES). Create an Amazon EventBridge (Amazon CloudWatch Events) rule by using Errors as the event pattern and the Lambda function name as a resource. Configure the rule to send a push notification through Amazon SES when the rule state reaches ALARM.
A company must ensure that any objects uploaded to an S3 bucket are encrypted. Which of the following actions will meet this requirement? (Choose two.)
A. Implement AWS Shield to protect against unencrypted objects stored in S3 buckets.
B. Implement Object access control list (ACL) to deny unencrypted objects from being uploaded to the S3 bucket.
C. Implement Amazon S3 default encryption to make sure that any object being uploaded is encrypted before it is stored.
D. Implement Amazon Inspector to inspect objects uploaded to the S3 bucket to make sure that they are encrypted.
E. Implement S3 bucket policies to deny unencrypted objects from being uploaded to the buckets.
A company hosts a database on an Amazon RDS Multi-AZ DB instance. The database is not encrypted. The company's new security policy requires all AWS resources to be encrypted at rest and in transit.
What should a SysOps administrator do to encrypt the database?
A. Configure encryption on the existing DB instance.
B. Take a snapshot of the DB instance. Encrypt the snapshot. Restore the snapshot to the same DB instance.
C. Encrypt the standby replica in a secondary Availability Zone. Promote the standby replica to the primary DB instance.
D. Take a snapshot of the DB instance. Copy and encrypt the snapshot. Create a new DB instance by restoring the encrypted copy.
A company needs to upload gigabytes of files every day. The company need to achieve higher throughput and upload speeds to Amazon S3.
Which action should a SysOps administrator take to meet this requirement?
A. Create an Amazon CloudFront distribution with the GET HTTP method allowed and the S3 bucket as an origin.
B. Create an Amazon ElastiCache duster and enable caching for the S3 bucket
C. Set up AWS Global Accelerator and configure it with the S3 bucket
D. Enable S3 Transfer Acceleration and use the acceleration endpoint when uploading files
A company runs an application that hosts critical data for several clients. The company uses AWS CloudTrail to track user activities on various AWS resources. To meet new security requirements, the company needs to protect the CloudTrail
log files from being modified, deleted, or forged.
Which solution will meet these requirement?
A. Enable CloudTrail log file integrity validation.
B. Use Amazon S3 MFA Delete on the S3 bucket where the CloudTrail log files are stored.
C. Use Amazon S3 Versioning to keep all versions of the CloudTrail log files.
D. Use AWS Key Management Service (AWS KMS) security keys to secure the CloudTrail log files.
A company has an AWS Lambda function in Account A. The Lambda function needs to read the objects in an Amazon S3 bucket in Account B. A SysOps administrator must create corresponding IAM roles in both accounts. Which solution will meet these requirements?
A. In Account A, create a Lambda execution role to assume the role in Account B. In Account B. create a role that the function can assume to gain access to the S3 bucket.
B. In Account A, create a Lambda execution role that provides access to the S3 bucket. In Account B, create a role that the function can assume.
C. In Account A, create a role that the function can assume. In Account B, create a Lambda execution role that provides access to the S3 bucket.
D. In Account A. create a role that the function can assume to gain access to the S3 bucket. In Account B, create a Lambda execution role to assume the role in Account A.
A company recently deployed MySQL on an Amazon EC2 instance with a default boot volume. The company intends to restore a 1.75 TB database. A SysOps administrator needs to provision the correct Amazon Elastic Block Store (Amazon EBS) volume. The database will require read performance of up to 10,000 IOPS and is not expected to grow in size.
Which solution will provide the required performance at the LOWEST cost?
A. Deploy a 2 TB Cold HDD (sc1) volume.
B. Deploy a 2 TB Throughput Optimized HDD (st1) volume.
C. Deploy a 2 TB General Purpose SSD (gp3) volume. Set the IOPS to 10,000.
D. Deploy a 2 TB Provisioned IOPS SSD (io2) volume. Set the IOPS to 10,000.
A company creates a new Amazon FSx for Windows File Server file system. To help manage costs, the company configures the storage capacity for the file system with minimal room for growth.
The company creates an Amazon Simple Notification Service (Amazon SNS) topic in the same AWS account whore the file system resides. The company subscribes a SysOps administrator's email address to the SNS topic. The SysOps administrator needs to receive email notification when the file system has less than 100 GB of space available.
Which combination of steps should the SysOps administrator take to meet this requirement? (Choose two.)
A. Create an Amazon EventBridge rule for when the FreeStorageCapacity metric is less than or equal to 100,000,000,000 bytes (100 GB).
B. Create an Amazon CloudWatch alarm for when the FreeStorageCapacity metric is less than or equal to 100,000,000,000 bytes (100 GB).
C. Create an AWS Lambda function that will run when the Amazon CloudWatch alarm enters ALARM state. Configure the Lambda function to publish to the SNS topic.
D. Configure the Amazon EventBridge rule's alarm action to publish to the SNS topic when the rule enters ALARM state.
E. Configure the Amazon CloudWatch alarm action to publish to the SNS topic when the alarm enters ALARM state.
AnyCompany has acquired Example Corp and is attempting to consolidate the business systems of both companies. AnyCompany's IT department needs to integrate with Example Corp's IT ticketing system.
A SysOps administrator must implement a solution that uses Amazon CloudWatch alarms for Amazon EC2 instances in AnyCompany's account to create new tickets in Example Corp's ticketing system. The ticketing system provides an HTTPS endpoint for the creation of new tickets. The ticketing system accepts messages in the following JSON format:
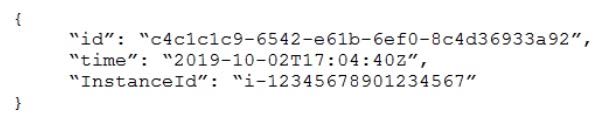
Which approach to creating tickets from the CloudWatch alarms will meet these requirements with the LEAST development time?
A. Create an Amazon EventBridge rule that filters appropriate events and specifies EventBridge API destinations as a target. Configure EventBridge API destinations to send events to the HTTPS endpoint. In the EventBridge rule, create an
input transformer to convert the source to a compatible output for the ticketing system.
B. Create an Amazon EventBridge rule that filters appropriate events and specifies an Amazon Kinesis data stream as the target. Create an AWS Lambda function to receive events from the Kinesis data stream. Configure the Lambda function to start an AWS Glue job to transform the data and forward the output to the HTTPS endpoint.
C. Create an Amazon EventBridge rule that filters appropriate events and specifies Amazon Simple Notification Service (Amazon SNS) as a target. Configure Amazon SNS to transform the events and send the events to the HTTPS endpoint.
D. Create an Amazon EventBridge rule that filters appropriate events and specifies an AWS Step Functions state machine as a target. Create an AWS Lambda function and an AWS Glue job in Step Functions to transform the events and send the events to the HTTPS endpoint.

