SC-200 Online Practice Questions and Answers
You need to implement the Azure Information Protection requirements. What should you configure first?
A. Device health and compliance reports settings in Microsoft Defender Security Center
B. scanner clusters in Azure Information Protection from the Azure portal
C. content scan jobs in Azure Information Protection from the Azure portal
D. Advanced features from Settings in Microsoft Defender Security Center
You are investigating a potential attack that deploys a new ransomware strain.
You plan to perform automated actions on a group of highly valuable machines that contain sensitive information.
You have three custom device groups.
You need to be able to temporarily group the machines to perform actions on the devices.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Add a tag to the device group.
B. Add the device users to the admin role.
C. Add a tag to the machines.
D. Create a new device group that has a rank of 1.
E. Create a new admin role.
F. Create a new device group that has a rank of 4.
You have an Azure Sentinel deployment in the East US Azure region.
You create a Log Analytics workspace named LogsWest in the West US Azure region.
You need to ensure that you can use scheduled analytics rules in the existing Azure Sentinel deployment to generate alerts based on queries to LogsWest.
What should you do first?
A. Deploy Azure Data Catalog to the West US Azure region.
B. Modify the workspace settings of the existing Azure Sentinel deployment.
C. Add Azure Sentinel to a workspace.
D. Create a data connector in Azure Sentinel.
You have a Microsoft 365 subscription that uses Microsoft 365 Defender.
A remediation action for an automated investigation quarantines a file across multiple devices.
You need to mark the file as safe and remove the file from quarantine on the devices.
What should you use in the Microsoft 365 Defender portal?
A. From Threat tracker, review the queries.
B. From the History tab in the Action center, revert the actions.
C. From the investigation page, review the AIR processes.
D. From Quarantine from the Review page, modify the rules.
You have an Azure subscription that uses Microsoft Defender for Cloud and contains 100 virtual machines that run Windows Server.
You need to configure Defender for Cloud to collect event data from the virtual machines. The solution must minimize administrative effort and costs.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. From the workspace created by Defender for Cloud, set the data collection level to Common.
B. From the Microsoft Endpoint Manager admin center, enable automatic enrollment.
C. From the Azure portal, create an Azure Event Grid subscription.
D. From the workspace created by Defender for Cloud, set the data collection level to All Events.
E. From Defender for Cloud in the Azure portal, enable automatic provisioning for the virtual machines.
You have 500 on-premises devices.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365.
You onboard 100 devices to Microsoft Defender 365.
You need to identify any unmanaged on-premises devices. The solution must ensure that only specific onboarded devices perform the discovery.
What should you do first?
A. Create a device group.
B. Create an exclusion.
C. Set Discovery mode to Basic.
D. Create a tag.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that uses Microsoft Defender XDR.
From the Microsoft Defender portal, you perform an audit search and export the results as a file named File1.csv that contains 10,000 rows.
You use Microsoft Excel to perform Get and Transform Data operations to parse the AuditData column from File1.csv. The operations fail to generate columns for specific JSON properties.
You need to ensure that Excel generates columns for the specific JSON properties in the audit search results.
Solution: From Defender, you modify the search criteria of the audit search to increase the number of returned records, and then you export the results. From Excel, you perform the Get and Transform Data operations by using the new export.
Does this meet the requirement?
A. Yes
B. No
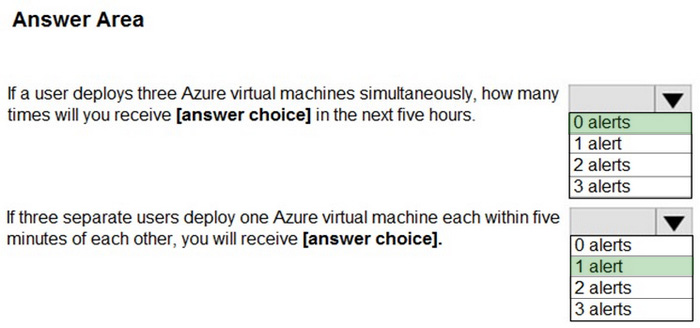
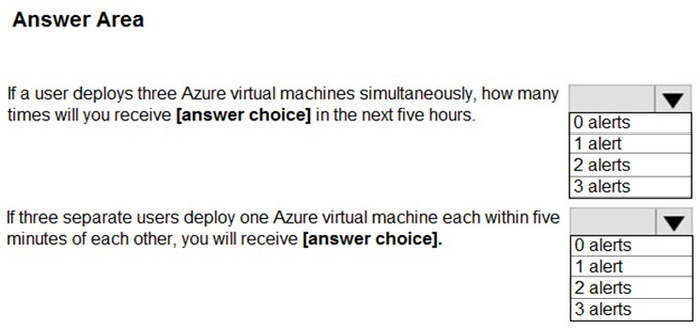
HOTSPOT
You use Azure Sentinel to monitor irregular Azure activity.
You create custom analytics rules to detect threats as shown in the following exhibit.
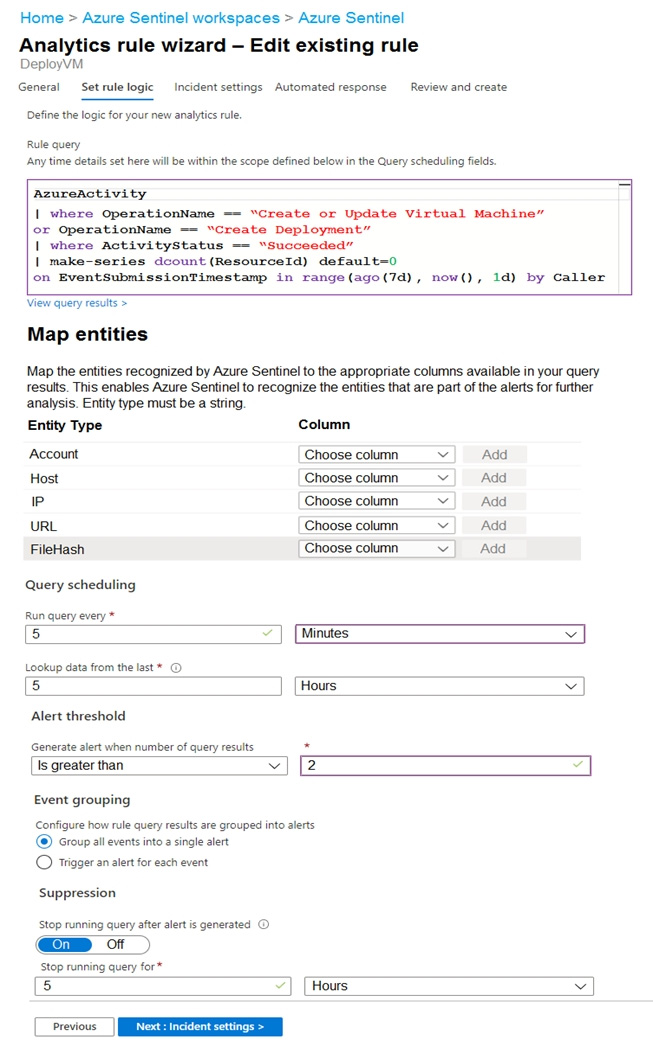
You do NOT define any incident settings as part of the rule definition.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
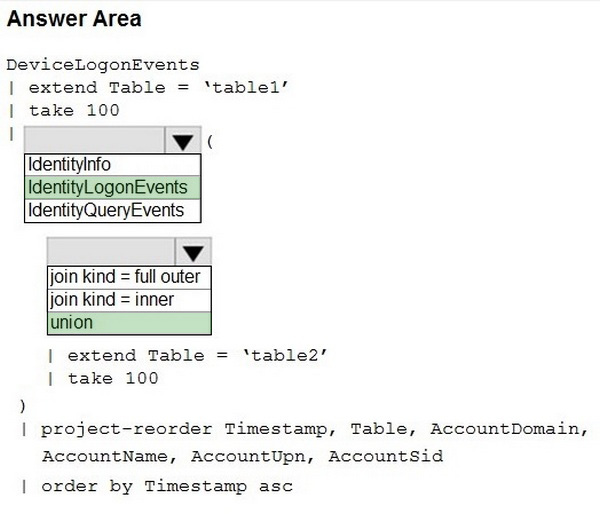
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365.
Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD.
You need to identify the 100 most recent sign-in attempts recorded on devices and AD DS domain controllers.
How should you complete the KQL query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
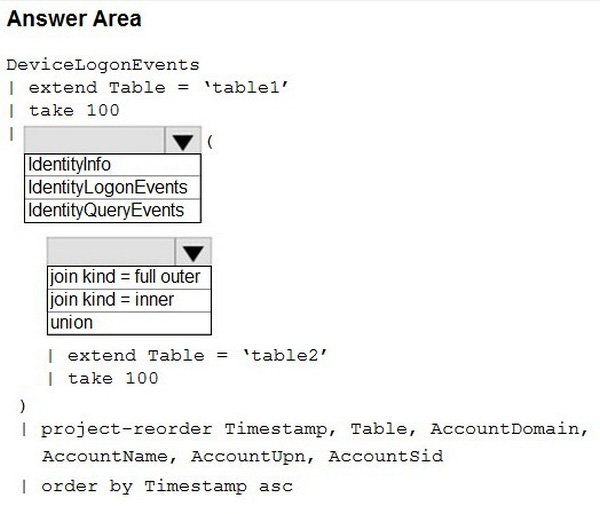
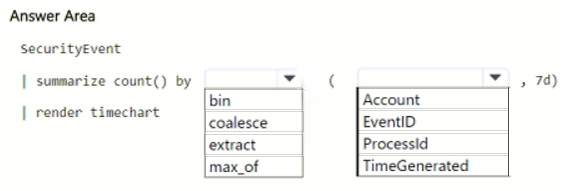
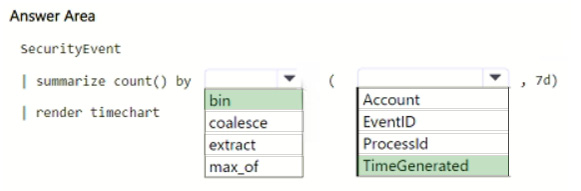
HOTSPOT
You have a Microsoft Sentinel workspace that contains a custom workbook.
You need to query for a summary of security events. The solution must meet the following requirements:
1.
Identify the number of security events ingested during the past week.
2.
Display the count of events by day in a chart.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: