S10-210 Online Practice Questions and Answers
A customer has upgraded all switches in their redundant fabrics during a single maintenance window. Shortly after the upgrades are completed on the core switches, all servers lose access to all SAN attached storage.
What would have prevented this scenario?
A. High availability
B. Fault tolerance
C. Change or risk management
D. Clustered servers
You have a server which is booting from a SAN. After adding new SAN storage to a host, the host will not boot from the SAN.
What will resolve this problem?
A. LUN masking
B. Persistent binding
C. Trunking
D. Multiplex binding
A line of business (LOB) executive informs you that a new application requires 99.999% (five 9s) of uptime from both planned and unplanned outages before a service level objective (SLO) will be breached.
What is the amount of permissible downtown per week?
A. 20.16 minutes
B. .605 seconds
C. 5.04 minutes
D. 6.06 seconds
Click the Exhibit button.
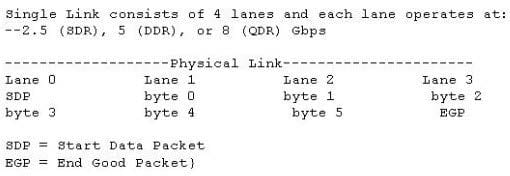
The physical interface shown in the exhibit is taken from which transport protocol?
A. Ethernet
B. FCP
C. FCoE
D. InfiniBand
A security audit reveals deficiencies in your company's FC zoning practices. Your manager asks you to make a recommendation to implement the most secure FC zoning possible. Your company is using switches from a single vendor.
What do you recommend?
A. All zones should use frame-based hardware enforcement using pWWN identification exclusively for all configurations.
B. All zones should use software-based enforcement using pWWN identification exclusively for all configurations.
C. All zones should use frame-based hardware enforcement using destination port identification exclusively for all configurations.
D. All zones should use software-based enforcement using destination port identification exclusively for all configurations.
After the storage administrator merged two multi-vendor FC SANs, an error indicates that two ports have become isolated causing a segmentation to exist in the fabric.
Which two events would cause this? (Choose two.)
A. Overlapping zones
B. Different port names
C. Unsupported routing protocols
D. Different link speeds
You have determined that the root cause of your problem is related to invalid characters being intermittently transmitted on your 4 Gb FC link.
What describes this condition?
A. Disparity error character
B. Link hardware cannot detect k28.3 characters
C. Link hardware cannot detect k28.5 characters
D. Character does not fit in allowed 8b/10b codes or special characters
Your organization operates in a regulated environment and contracts with a service provider to manage tape backup media for highly confidential, secure data.
Using SNIA Storage Security Best Practices, which two statements are correct? (Choose two.)
A. Tape backup media is stored in a secure, temperature controlled vault.
B. The service provider keeps unencrypted backup media locked during transport.
C. All removable media is encrypted and backup media locked during transport.
D. The customer manages the chain of custody.
You are installing an OLTP application on a new server. The I/O profile of the application consists of 100% random read operations of 8 kilobyte transfers. You need to determine which HBA to use in your application to accommodate 50,000 IOPS.
What is the minimum FC link speed that will satisfy the application's requirements?
A. 1 Gbps
B. 2 Gbps
C. 4 Gbps
D. 8 Gbps
Which type of storage replication is required, at a minimum, for a non-critical application?
A. Synchronous
B. Asynchronous
C. Semi-synchronous
D. Multi-synchronous

