PCCSA Online Practice Questions and Answers
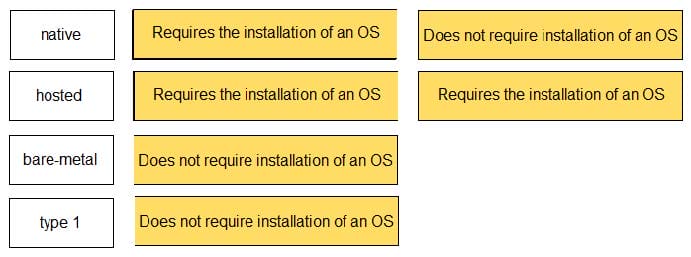
DRAG DROP
Match the task for server settings in group mapping with its order in the process.
Select and Place:
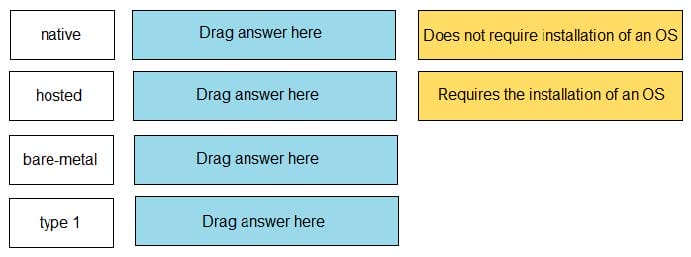
DRAG DROP
Match each cryptographic method with its description.
Select and Place:
Which option describes a characteristic of a distributed denial-of-service attack?
A. uses multiple types of malware to corrupt system services
B. uses a single remote host to delete data from multiple target servers
C. uses a single remote host to flood a target network with traffic
D. uses a botnet to flood traffic to a target network
What are two methods to securely transmit personally identifiable information? (Choose two.)
A. data checksumming
B. data fragmentation
C. data encryption
D. encrypted tunnels
Which protocol converts voice into a digital signal?
A. IVO
B. VoIP
C. SNMP
D. IGMP
Review the exhibit and identify the type of vulnerability or attack that is commonly used against this technology.

A. phishing
B. denial-of-service
C. code-injection
D. password cracking
Company policy allows employees to access the internet. While searching for office supplies on the internet, a corporate user mistypes a URL, connects to a malicious website, and unknowingly downloads malware.
Which action should have been taken to prevent the malware download but still allow user access to the internet?
A. deploy a firewall with content filtering capabilities on the corporate perimeter
B. allow only encrypted HTTPS access to the internet
C. configure digital certificates for all users to authenticate internet downloads
D. permit web connections only to TCP port 443
Which capability is required for a next-generation firewall to protect your network against malware threats?
A. can access/read Windows and Linux file systems
B. can scan all endpoint devices
C. can interpret file permissions
D. can perform SSL decryption
Which type of cloud computing service provides access to email and word processing applications running in a cloud infrastructure?
A. software as a service
B. computing as a service
C. platform as a service
D. infrastructure as a service
Assume that it is your responsibility to secure the software functioning at top five layers in the exhibit.
Which cloud service model type is represented?
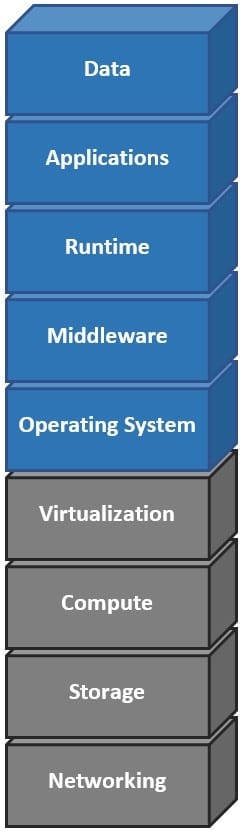
A. software as a service
B. platform as a service
C. infrastructure as a service
D. on-premises