NSE8_811 Online Practice Questions and Answers
You want to access the JSON API on FortiManager to retrieve information on an object. In this scenario, which two methods will satisfy the requirement? (Choose two.)
A. Download the WSDL file from FortiManager administration GUI.
B. Make a call with the curl utility on your workstation.
C. Make a call with the SoapUI API tool on your workstation.
D. Make a call with the Web browser on your workstation.
Refer to the exhibit.
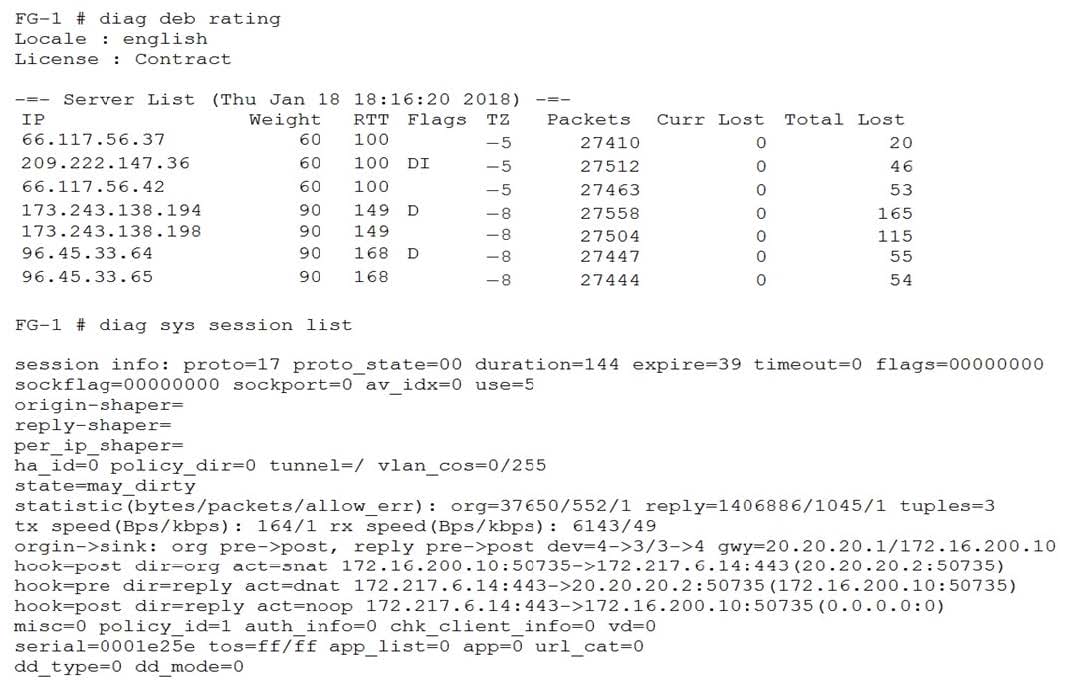
You configured AV and Web filtering for your outgoing Internet connections. You later notice that not all Web sessions are being inspected and you start troubleshooting the problem.
Referring to the exhibit, what can be causing this problem?
A. The Web session is using QUIC which is not inspected by the FortiGate.
B. There are problems with the connection to the Web filter servers, therefore the Web session cannot be categorized.
C. The SSL inspection options are not set to deep inspection.
D. Web filtering is not licensed; therefore, no inspection occurs.
You cannot ping the FortiGate default gateway 10.10.10.1 from the FortiGate CLI. The FortiGate interface facing the default gateway is wan1 and its IP address is 10.10.10.254/24. During the initial troubleshooting tests, you confirm that you can ping other IP addresses in the 10.10.10.0/24 subnet from the FortiGate CLI without packets lost.
Which two CLI commands will help you to troubleshoot this problem? (Choose two.)
A. diagnose debug flow filter saddr 10.10.10.1 diagnose debug flow trace start 10
B. diagnose hardware deviceinfo nic wan1
C. diagnose ip arp list
D. diag sniffer packet wan1 'arp and host 10.10.10.1'
An organization has one central site and three remote sites. A FortiSIEM has been installed on the central site and now all devices across the remote sites must be centrally monitored by the FortiSIEM at the central site.
Which action will reduce the WAN usage by the monitoring system?
A. Enable SD-WAN FEC (Forward Error Correction) on the FortiGate at the remote site.
B. Install both Supervisor and Collector on each remote site.
C. Install local Collectors on each remote site.
D. Disable real-time log upload on the remote sites.
Refer to the exhibit.
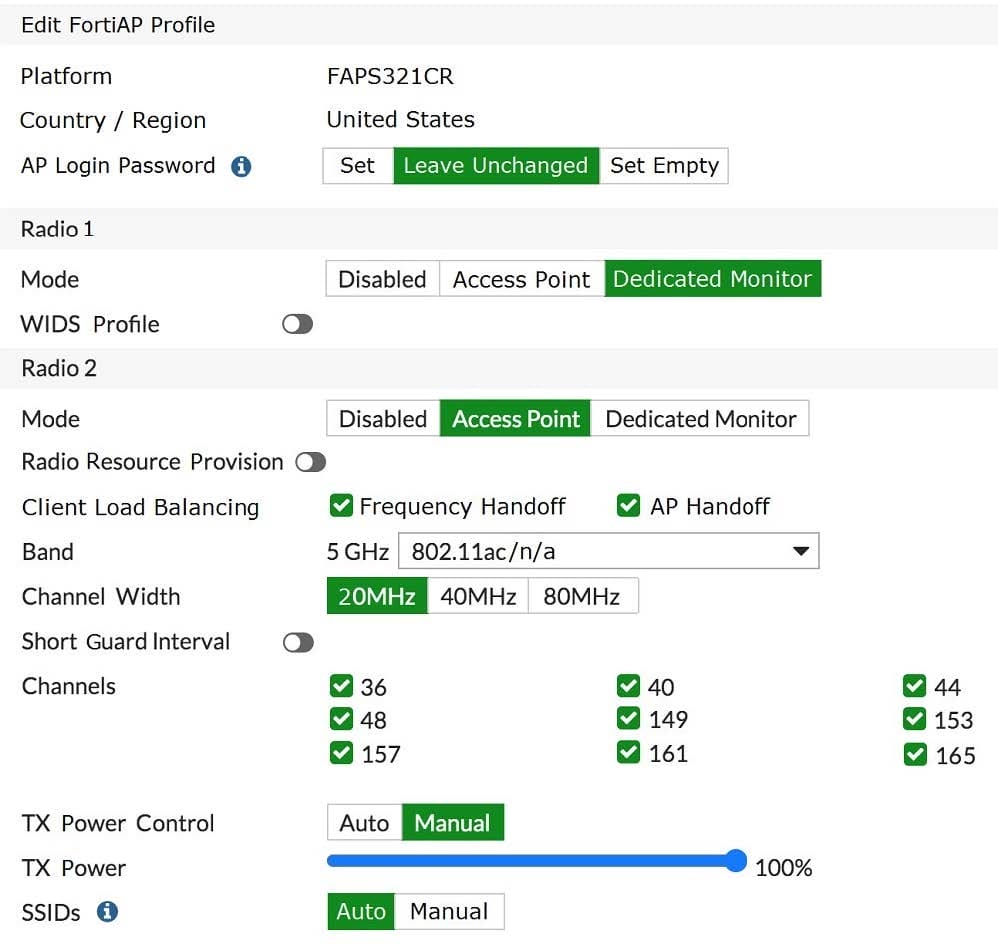
The FortiAP profile used by the FortiGate managed AP is shown in the exhibit. Which two statements in this scenario are correct? (Choose two.)
A. Interference will be prevented between FortiAP devices using this profile.
B. This profile will map specific SSIDs available to the FortiAP devices.
C. All FortiAP devices using this profile will have Radio 1 monitor wireless clients.
D. All FortiAP devices using this profile will have Radio 1 scan rogue access points.
Refer to the exhibit.
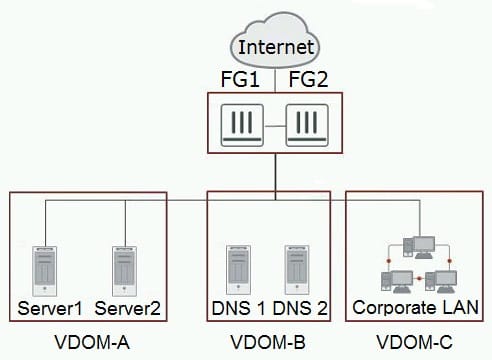
You need to apply the security features listed below to the network shown in the exhibit.
High grade DDoS protection Web security and load balancing for Server 1 and Server 2 Solution must be PCI DSS compliant Enhanced security to DNS 1 and DNS 2
What are three solutions for this scenario? (Choose three.)
A. FortiDDoS between FG1 and FG2 and the Internet
B. FortiADC for VDOM-A
C. FortiWeb for VDOM-A
D. FortiADC for VDOM-B
E. FortiDDoS between FG1 and FG2 and VDOMs
A FortiGate with the default configuration shown below is deployed between two IP telephones. FortiGate receives the INVITE request shown in the exhibit from Phone A (internal) to Phone B (external).
NVITE sip:[email protected] SIP/2.0 Via: SIP/2.0/UDP 10.31.101.20:5060 From: PhoneA
Which two statements are correct after the FortiGate receives the packet? (Choose two.)
A. NAT takes place only in the SIP application layer.
B. A pinhole will be opened to accept traffic sent to the FortiGate WAN IP address.
C. NAT takes place at both the network and SIP application layers.
D. A pinhole is not required to accept traffic sent to the FortiGate WAN IP address.
Refer to the exhibit.
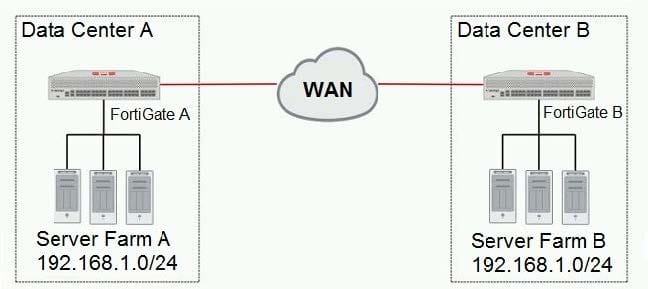
A company has two data centers (DC) connected using a Layer 3 network. Servers in farm A need to connect to servers in farm B as though they were all in the same Layer 2 segment.
Referring to the exhibit, what is configured on the FortiGate devices on each DC to allow this connectivity?
A. Create an IPsec tunnel with VXLAN encapsulation.
B. Create an IPsec tunnel with VLAN encapsulation.
C. Create an IPsec tunnel with transport-mode encapsulation.
D. Create an IPsec tunnel with tunnel-mode encapsulation.
You configured a firewall policy with only a Web filter profile for accessing the Internet. Access to websites belonging to the "Information Technology" category are blocked and to the "Business" category are allowed. SSL deep inspection is not enabled on this policy.
A user wants to access the website https://www.it-acme.com which presents a certificate with CN=www.acme.com. The it-acme.com domain is categorized as "Information Technology" and the acme.com domain is categorized as "Business".
Which statement regarding this scenario is correct?
A. The FortiGate is able to read the URL within HTTPS sessions when using SSL certificate inspection so the website will be blocked by the "Information Technology".
B. The website will be blocked by category "Information Technology" as the SNI takes precedence over the certificate name.
C. The website will be allowed by category "Business" as the certificate name takes precedence over the URL.
D. Only with SSL deep inspection enabled will the FortiGate be able to categorized this website.
Refer to the exhibit.
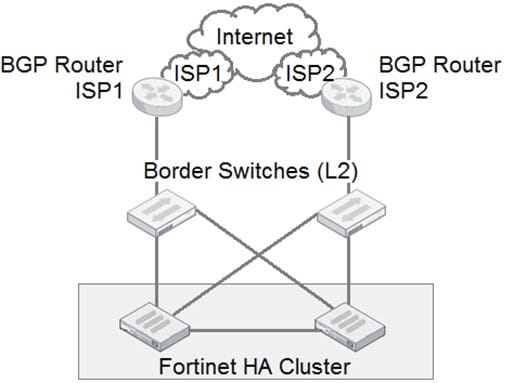
An organization has a FortiGate cluster that is connected to two independent ISPs. You must configure the FortiGate failover for a single ISP failure to occur without disruption.
Referring to the exhibit, which two FortiGate BGP features are enabled to accomplish this task? (Choose two.)
A. EBGP multipath
B. Graceful restart
C. Synchronization
D. BFD

