NSE7_SDW-7.0 Online Practice Questions and Answers
In the default SD-WAN minimum configuration, which two statements are correct when traffic matches the default implicit SD-WAN rule? (Choose two )
A. Traffic has matched none of the FortiGate policy routes.
B. Matched traffic failed RPF and was caught by the rule.
C. The FIB lookup resolved interface was the SD-WAN interface.
D. An absolute SD-WAN rule was defined and matched traffic.
Refer to the exhibit.

Based on the exhibit, which two actions does FortiGate perform on sessions after a firewall policy change? (Choose two.)
A. FortiGate flushes all sessions.
B. FortiGate terminates the old sessions.
C. FortiGate does not change existing sessions.
D. FortiGate evaluates new sessions.
Refer to the exhibits. Exhibit A Exhibit B
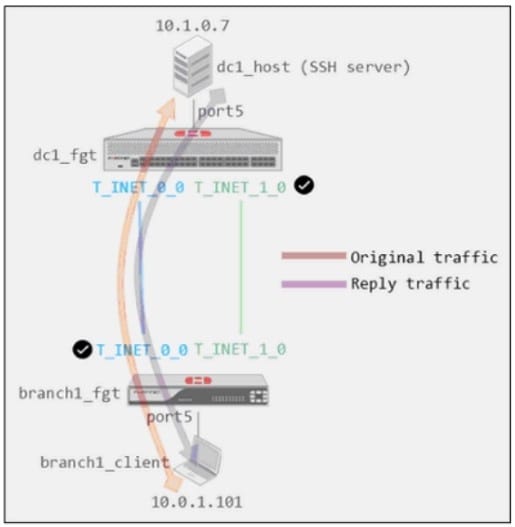

Exhibit A shows a site-to-site topology between two FortiGate devices: branch1_fgt and dc1_fgt. Exhibit B shows the system global and system settings configuration on dc1_fgt.
When branch1_client establishes a connection to dc1_host, the administrator observes that, on dc1_fgt, the reply traffic is routed over T_INET_0_0, even though T_INET_1_0 is the preferredmember in the matching SD-WAN rule.
Based on the information shown in the exhibits, what configuration change must be made on dc1_fgt so dc1_fgt routes the reply traffic over T_INET_1_0?
A. Enable auxiliary-session under config system settings.
B. Disable tp-session-without-syn under config system settings.
C. Enable snat-route-change under config system global.
D. Disable allow-subnet-overlap under config system settings.
Refer to the exhibit.
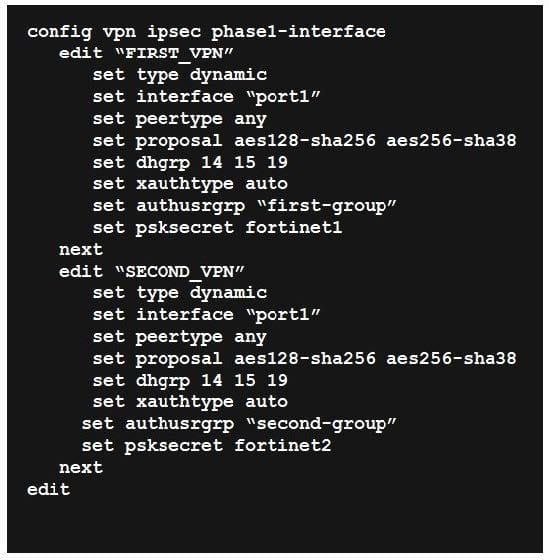
FortiGate has multiple dial-up VPN interfaces incoming on port1 that match only FIRST_VPN.
Which two configuration changes must be made to both IPsec VPN interfaces to allow incoming connections to match all possible IPsec dial-up interfaces? (Choose two.)
A. Specify a unique peer ID for each dial-up VPN interface.
B. Use different proposals are used between the interfaces.
C. Configure the IKE mode to be aggressive mode.
D. Use unique Diffie Hellman groups on each VPN interface.
Refer to the exhibit.

Which two conclusions for traffic that matches the traffic shaper are true? (Choose two.)
A. The traffic shaper drops packets if the bandwidth is less than 2500 KBps.
B. The measured bandwidth is less than 100 KBps.
C. The traffic shaper drops packets if the bandwidth exceeds 6250 KBps.
D. The traffic shaper limits the bandwidth of each source IP to a maximum of 6250 KBps.
Refer to Exhibit:
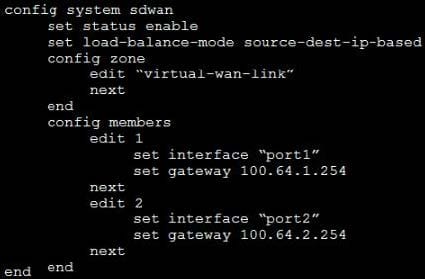
Based on the exhibit, which algorithm does SD-WAN use to distribute traffic that does not match any of the SD-WAN rules, among the member interfaces?
A. All traffic from a source IP to a destination IP Is sent to the same interface.
B. All traffic from a source IP Is sent to the most used Interface.
C. All traffic from a source IP to a destination IP is sent to the least used interface.
D. All traffic from a source IP is sent to the same interfaces.
Refer to exhibits
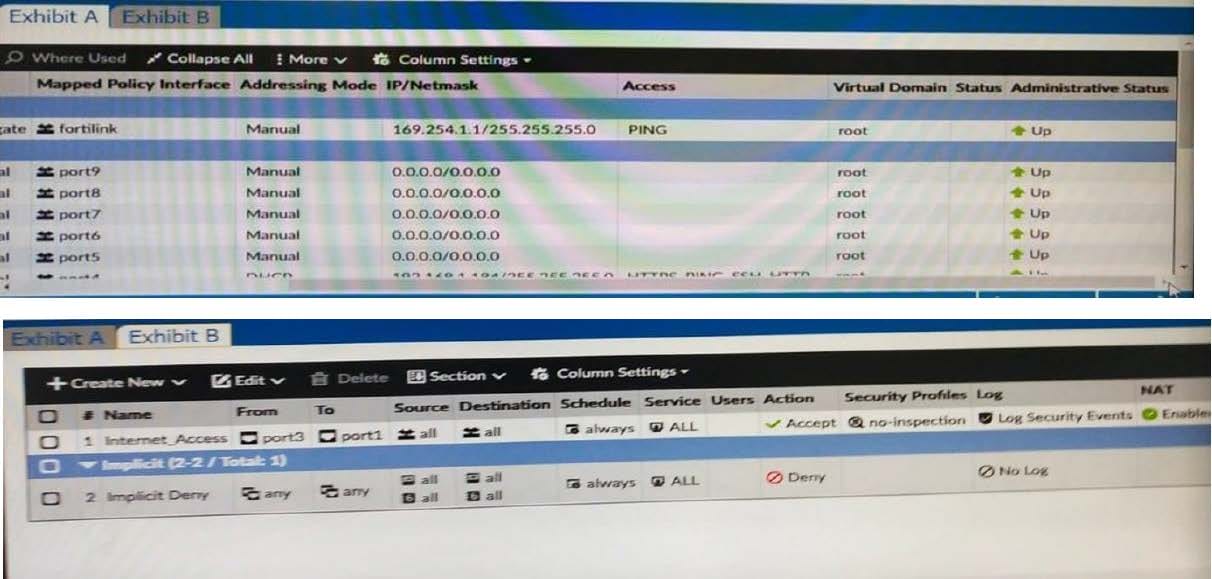
Exhibit A shows the system interface with the static routes and exhibit B shows the firewall policies on the managed FortiGate
Based on the FortiGate configuration shown in the exhibits, what are two issues you might encounter when creating an SD-WAN interface on port1 and port2? {Choose two )
A. Member interfaces that are administratively down
B. Member interface that have IP address of 0.0.0.0/0.0.0.0
C. Member interfaces that are physical interfaces as well as VLAN aggregate, and iPsec interfaces
D. Member interfaces that are referenced by any other configuration element
What are two reasons why it is effective to implement the internet service database (ISDB) in an SD-WAN rule? (Choose two )
A. The ISDB is dynamically updated and reduces administrative overhead.
B. The ISDB applies rules to traffic from specific sources, based on application type.
C. The ISDB requires application control to maintain signatures and perform load-balancing.
D. The ISDB contains the IP addresses and port ranges of well-known destinations.
Refer to the exhibit.
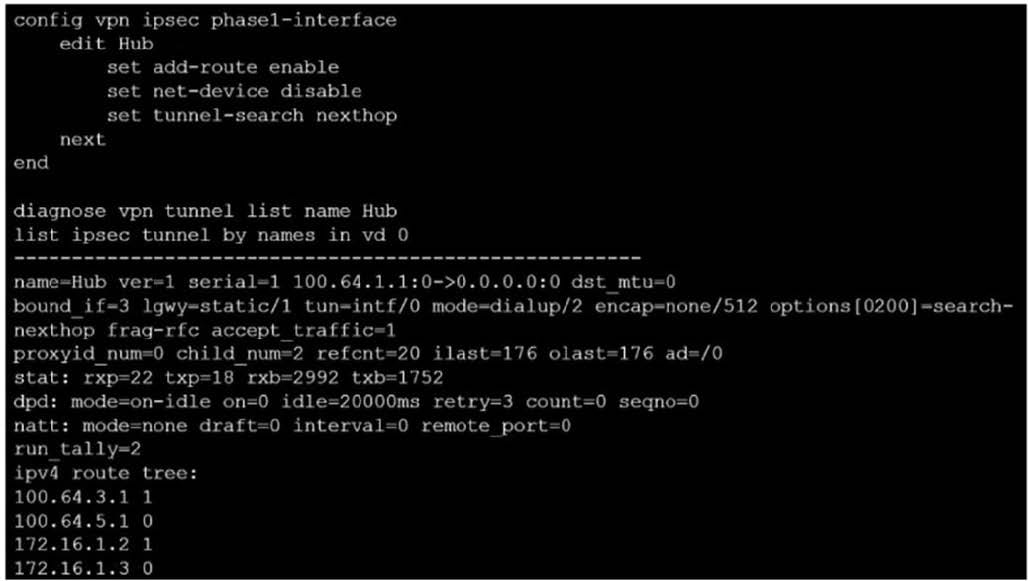
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
A. FortiGate creates separate virtual interfaces for each dial-up client.
B. FortiGate creates a single IPsec virtual interface that is shared by all clients.
C. FortiGate maps the remote gateway 100.64.3.1 to tunnel index interface 1.
D. FortiGate does not install IPsec static routes for remote protected networks in the routing table.
Refer to exhibits.
Exhibit A.
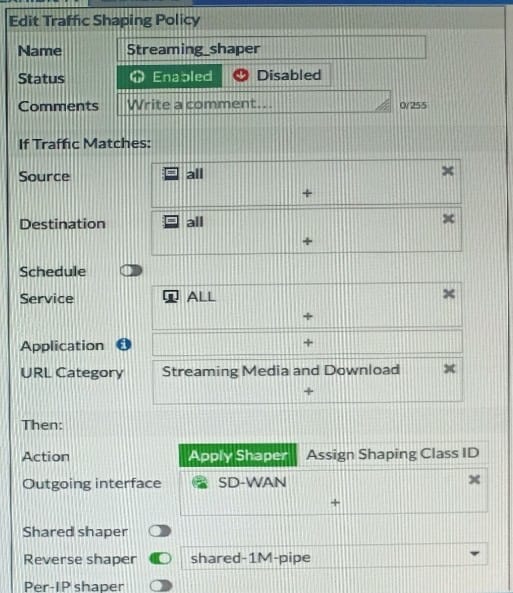
Exhibit B.
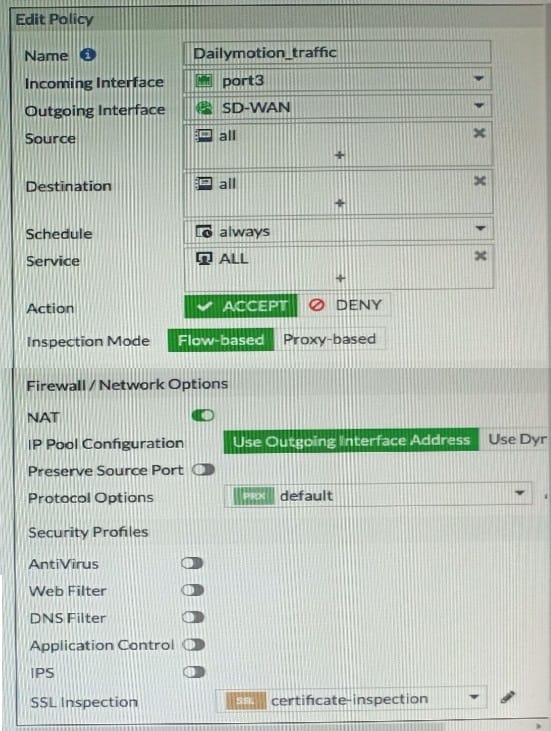
Exhibit A shows the traffic shaping policy and exhibit B show: the firewall policy
FortiGate is not performing traffic shaping as expected basi on the policies shown in the exhibits.
To correct this traffic shaping issue on FortiGate, what configuration change must be made on which policy?
A. The shaper mode must be applied per-IP shaper on the traffic shaping policy
B. The application control profile must be enabled on the firewall policy.
C. The web filter profile must be enabled on the firewall policy
D. The URL category must be specified on the traffic shaping policy

