NSE7_SDW-6.4 Online Practice Questions and Answers
What are the two minimum configuration requirements for an outgoing interface to be selected once the SD-WAN logical interface is enabled? (Choose two )
A. Specify outgoing interface routing cost.
B. Configure SD-WAN rules interface preference.
C. Select SD-WAN balancing strategy.
D. Specify incoming interfaces in SD-WAN rules.
Refer to exhibits.
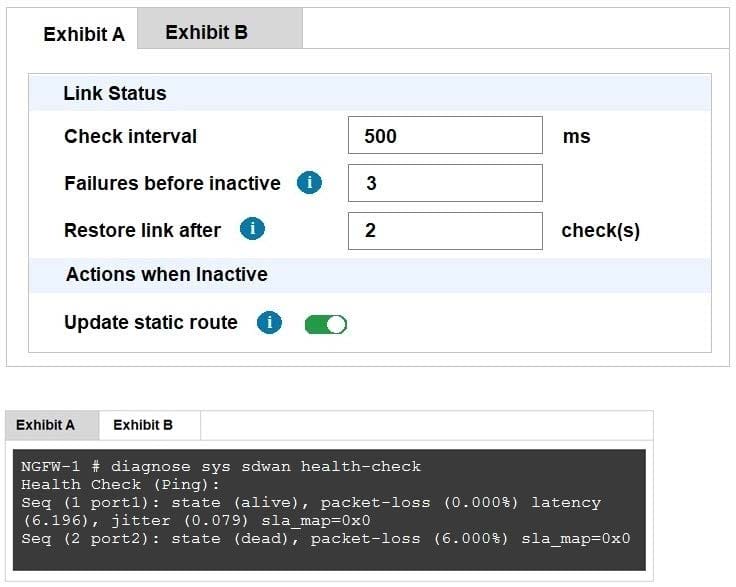
Exhibit A, which shows the SD-WAN performance SLA and exhibit B shows the health of the participating SD-WAN members.
Based on the exhibits, which statement is correct?
A. The dead member interface stays unavailable until an administrator manually brings the interface back.
B. Port2 needs to wait 500 milliseconds to change the status from alive to dead.
C. Static routes using port2 are active in the routing table.
D. FortiGate has not received three consecutive requests from the SLA server configured for port2.
Refer to the exhibit.
Multiple IPsec VPNs are formed between two hub-and-spokes groups, and site-to-site between Hub 1 and Hub 2 The administrator configured ADVPN on the dual regions topology
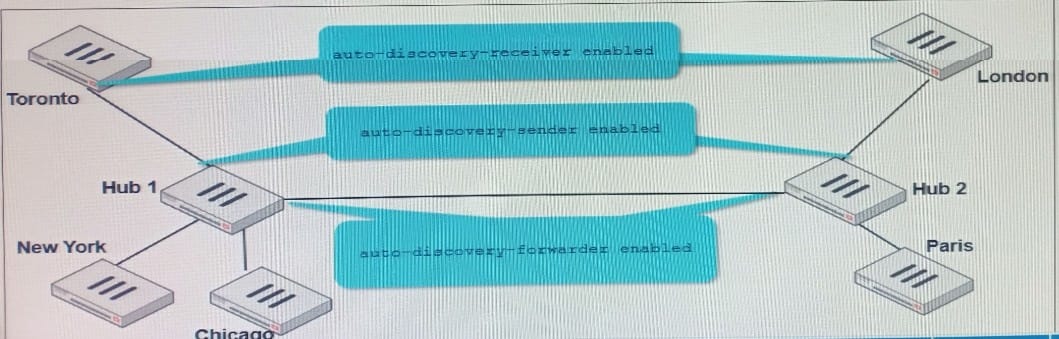
Which two statements are correct if a user in Toronto sends traffic to London? (Choose two )
A. Toronto needs to establish a site-to-site tunnel with Hub 2 to bypass Hub 1.
B. The first packets from Toronto to London are routed through Hub 1 then to Hub 2.
C. London generates an IKE information message that contains the Toronto public IP address.
D. Traffic from Toronto to London triggers the dynamic negotiation of a direct site-to-site VPN.
Refer to the exhibit.
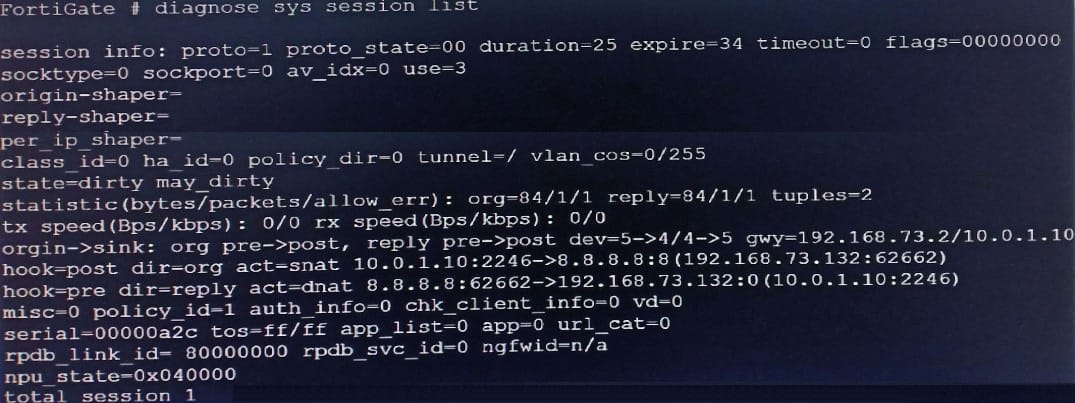
Based on the exhibit, which statement about FortiGate re-evaluating traffic is true?
A. The type of traffic defined and allowed on firewall policy ID 1 is UDP.
B. FortiGate has terminated the session after a change on policy ID 1.
C. Changes have been made on firewall policy ID 1 on FortiGate.
D. Firewall policy ID 1 has source NAT disabled.
Which components make up the secure SD-WAN solution?
A. Application, antivirus, and URL, and SSL inspection
B. Datacenter, branch offices, and public cloud
C. FortiGate, FortiManager, FortiAnalyzer, and FortiDeploy
D. Telephone, ISDN, and telecom network.
What are two reasons why it is effective to implement the internet service database (ISDB) in an SD-WAN rule? (Choose two )
A. The ISDB is dynamically updated and reduces administrative overhead.
B. The ISDB applies rules to traffic from specific sources, based on application type.
C. The ISDB requires application control to maintain signatures and perform load-balancing.
D. The ISDB contains the IP addresses and port ranges of well-known destinations.
Which action FortiGate performs on traffic that is subject to a per-IP traffic shaper of 10 Mbps?
A. FortiGate shares 10 Mbps of bandwidth equally among all source IP addresses.
B. FortiGate applies traffic shaping to the original traffic direction only.
C. FortiGate limits each source IP address to a maximum bandwidth of 10 Mbps.
D. FortiGate guarantees a minimum of 10 Mbps of bandwidth to each source IP address.
Which diagnostic command can you use to show the SD-WAN rules interface information and state?
A. diagnose sys virtual-wan-link neighbor.
B. diagnose sys virtual--wan--link route-tag-list
C. diagnose sys virtual--wan--link member.
D. diagnose sys virtual-wan-link service
Which diagnostic command you can use to show interface-specific SLA logs for the last 10 minutes?
A. diagnose sys virtual-wan-link health-check
B. diagnose sys virtual-wan-link log
C. diagnose sys virtual-wan-link sla-log
D. diagnose sys virtual-wan-link intf-sla-log
Refer to exhibits.
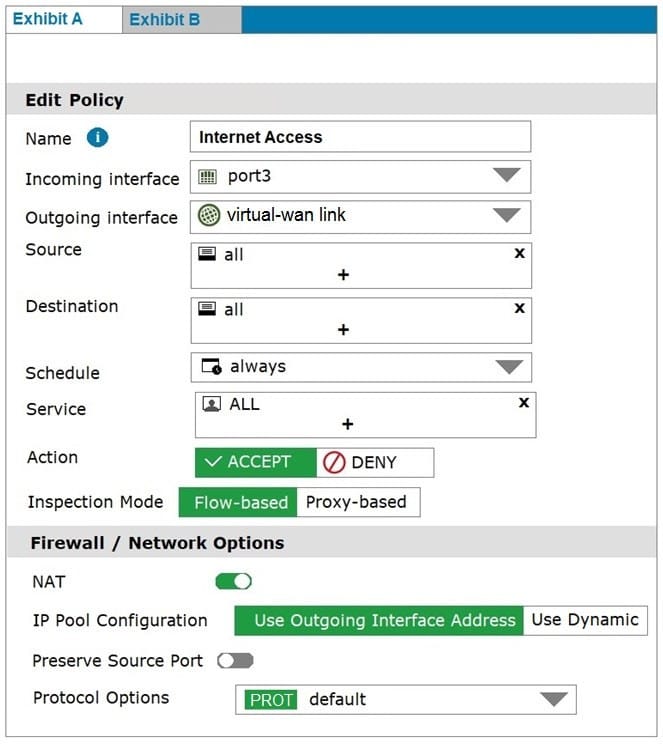
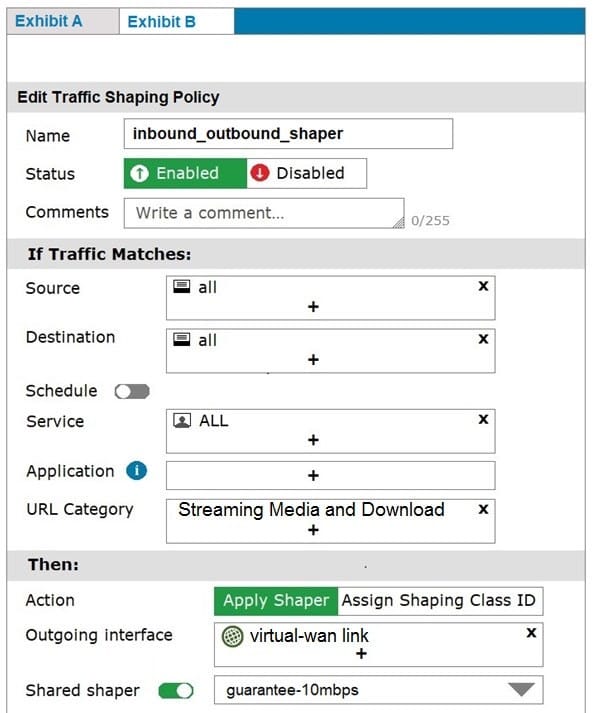
Exhibit A shows the firewall policy and exhibit B shows the traffic shaping policy.
The traffic shaping policy is being applied to all outbound traffic; however, inbound traffic is not being evaluated by the shaping policy.
Based on the exhibits, what configuration change must be made in which policy so that traffic shaping can be applied to inbound traffic?
A. Create a new firewall policy, and the select the SD-WAN zone as Incoming Interface.
B. In the traffic shaping policy, select Assign Shaping Class ID as Action.
C. In the firewall policy, select Proxy-based as Inspection Mode.
D. In the traffic shaping policy, enable Reverse shaper, and then select the traffic shaper to use.

