NSE7_PBC-6.4 Online Practice Questions and Answers
When configuring the FortiCASB policy, which three configuration options are available? (Choose three.)
A. Intrusion prevention policies
B. Threat protection policies
C. Data loss prevention policies
D. Compliance policies
E. Antivirus policies
You are deploying Amazon Web Services (AWS) GuardDuty to monitor malicious or unauthorized behaviors related to AWS resources. You will also use the Fortinet aws-lambda-guardduty script to translate feeds from AWS GuardDuty findings into a list of malicious IP addresses. FortiGate can then consume this list as an external threat feed.
Which Amazon AWS services must you subscribe to in order to use this feature?
A. GuardDuty, CloudWatch, S3, Inspector, WAF, and Shield.
B. GuardDuty, CloudWatch, S3, and DynamoDB.
C. Inspector, Shield, GuardDuty, S3, and DynamoDB.
D. WAF, Shield, GuardDuty, S3, and DynamoDB.
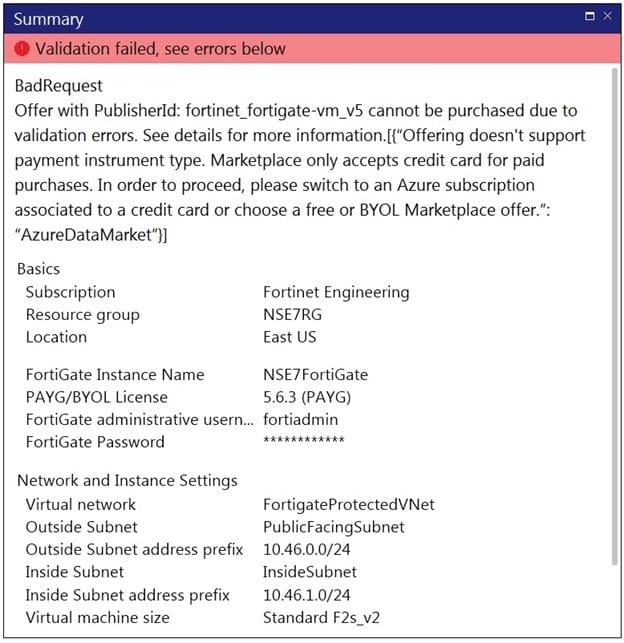
Refer to the exhibit. You are deploying a FortiGate-VM in Microsoft Azure using the PAYG/On-demand licensing model. After you configure the FortiGate-VM, the validation process fails, displaying the error shown in the exhibit.
What caused the validation process to fail?
A. You selected the incorrect resource group.
B. You selected the Bring Your Own License (BYOL) licensing mode.
C. You selected the PAYG/On-demand licensing model, but did not select correct virtual machine size.
D. You selected the PAYG/On-demand licensing model, but did not associate a valid Azure subscription.
An Amazon Web Services (AWS) auto-scale FortiGate cluster has just experienced a scale-down event, terminating a FortiGate in availability zone C.
What action will the worker node automatically perform to restore access to the black-holed subnet?
A. The worker node applies a route table from a non-black-holed subnet to the black-holed subnet.
B. The worker node moves the virtual IP of the terminated FortiGate to a running FortiGate on the worker node's private subnet interface.
C. The worker node modifies the route table applied to the black-holed subnet changing its default route to point to a running FortiGate on the worker node's private subnet interface.
D. The worker node migrates the subnet to a different availability zone.
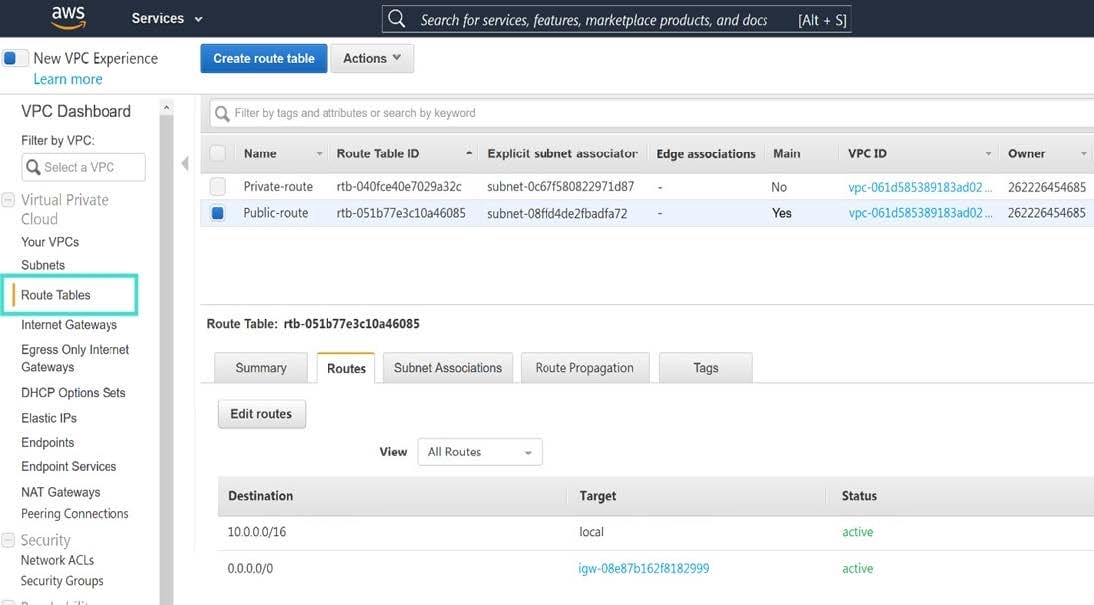
Which two statements about the Amazon Cloud Services (AWS) network access control lists (ACLs) are true? (Choose two.)
A. Network ACLs are stateless, and inbound and outbound rules are used for traffic filtering.
B. Network ACLs are stateful, and inbound and outbound rules are used for traffic filtering.
C. Network ACLs must be manually applied to virtual network interfaces.
D. Network ACLs support allow rules and deny rules.
Which two statements about Microsoft Azure network security groups are true? (Choose two.)
A. Network security groups can be applied to subnets and virtual network interfaces.
B. Network security groups can be applied to subnets only.
C. Network security groups are stateless inbound and outbound rules used for traffic filtering.
D. Network security groups are a stateful inbound and outbound rules used for traffic filtering.
A company deployed a FortiGate-VM with an on-demand license using Amazon Web Services (AWS) Market Place Cloud Formation template. After deployment, the administrator cannot remember the default admin password.
What is the default admin password for the FortiGate-VM instance?
A. The admin password cannot be recovered and the customer needs to deploy the FortiGate-VM again.
B.
C. admin
D. The instance-ID value
Your company deploys FortiGate VM devices in high availability (HA) (active-active) mode with Microsoft Azure load balancers using the Microsoft Azure ARM template. Your senior administrator instructs you to connect to one of the FortiGate devices and configure the necessary firewall rules. However, you are not sure now to obtain the correct public IP address of the deployed FortiGate VM and identify the access ports.
How do you obtain the public IP address of the FortiGate VM and identify the correct ports to access the device?
A. In the configured load balancer, access the inbound NAT rules section.
B. In the configured load balancer, access the backend pools section.
C. In the configured load balancer, access the inbound and outbound NAT rules section.
D. In the configured load balancer, access the health probes section.
Which statement about FortiSandbox in Amazon Web Services (AWS) is true?
A. In AWS, virtual machines (VMs) that inspect files do not have to be reset after inspecting a file.
B. FortiSandbox in AWS uses Windows virtual machines (VMs) to inspect files.
C. In AWS, virtual machines (VMs) that inspect files are constantly up and running.
D. FortiSandbox in AWS can have a maximum of eight virtual machines (VMs) that inspect files.
Customer XYZ has an ExpressRoute connection from Microsoft Azure to a data center. They want to secure communication over ExpressRoute, and to install an in-line FortiGate to perform intrusion prevention system (IPS) and antivirus scanning.
Which three methods can the customer use to ensure that all traffic from the data center is sent through A. Install FortiGate in Azure and build a VPN tunnel to the data center over ExpressRoute
B. Configure a user-defined route table
C. Enable the redirect option in ExpressRoute to send data center traffic to a user-defined route table
D. Configure the gateway subnet as the subnet in the user-defined route table
E. Define a default route where the next hop IP is the FortiGate WAN interface