NSE7_ATP-2.5 Online Practice Questions and Answers
Which samples can FortiClient submit to FortiSandbox for analysis? (Choose two.)
A. Downloads from emails
B. URLs from web requests
C. Command and control traffic D. Files from removable storage
Examine the System Information widget shown in the exhibit, then answer the following question:
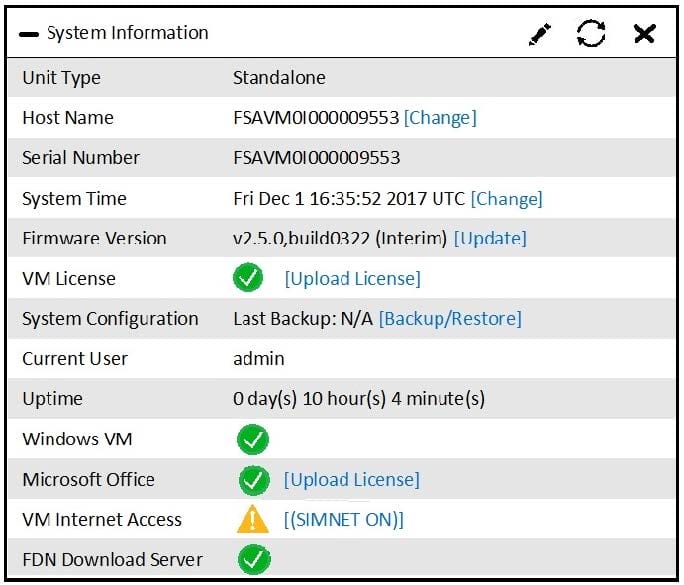
Which of the following inspections will FortiSandbox perform on samples submitted for sandboxing? (Choose two.)
A. URL rating on FQDN seen in DNS requests
B. IP reputation check on callback connections
C. Antivirus inspection on downloaded files
D. URL rating on HTTP GET requests
Which advanced threat protection integration solution should you use to protect against out-of-band attack vectors, such as USB drives, used during the delivery stage of the kill chain?
A. FortiGate and FortiSandbox
B. FortiMail and FortiSandbox
C. FortiWeb and FortiSandbox
D. FortiClient and FortiSandbox
Which FortiSandbox interfaces can you use for sniffer mode? (Choose two.)
A. port2
B. port3
C. port1
D. port4
Which threats can FortiSandbox inspect when it is deployed in sniffer mode? (Choose three.)
A. Spam emails
B. Known malware
C. Encrypted files
D. Malicious URLs
E. Botnet connections
Which FortiSandbox diagnostic command should you use to diagnose Internet connectivity issues on port3?
A. ping
B. tcpdump
C. test-network
D. traceroute
What advantage does sandboxing provide over traditional virus detection methods?
A. Heuristics detection that can detect new variants of existing viruses.
B. Pattern-based detection that can catch multiple variants of a virus.
C. Full code execution in an isolated and protected environment.
D. Code emulation as packets are handled in real-time.
Examine the virtual Simulator section of the scan job report shown in the exhibit, then answer the following question:

Based on the behavior observed by the virtual simulator, which of the following statements is the most likely scenario?
A. The file contained a malicious image file.
B. The file contained malicious JavaScript.
C. The file contained a malicious macro.
D. The file contained a malicious URL.
Examine the following topology shown in the exhibit, then answer the following question: Which of the following configuration tasks are applicable to secure Webserver from known threats? (Choose two.)
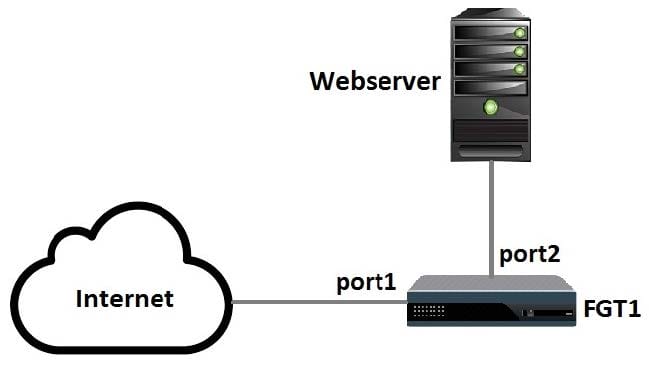
A. Apply an SSL inspection profile configured for protecting SSL server.
B. Apply an antivirus profile to the port1 -> port2 firewall policy.
C. Apply an SSL inspection profile configured for full SSL inspection.
D. Apply a web filter profile to the port1 -> port2 firewall policy.
Which of the following are FortiWeb's roles when integrated with FortiSandbox? (Choose two.)
A. Share threat information
B. Prevent outbreaks
C. Generate a verdict
D. Block known threats

