NSE6_FNC-8.5 Online Practice Questions and Answers
How should you configure MAC notification traps on a supported switch?
A. Configure them only on ports set as 802.1q trunks
B. Configure them on all ports except uplink ports
C. Configure them on all ports on the switch
D. Configure them only after you configure linkup and linkdown traps
Which connecting endpoints are evaluated against all enabled device profiling rules?
A. Known trusted devices each time they change location
B. Rogues devices, each time they connect
C. Rogues devices, only when they connect for the first time
D. All hosts, each time they connect
Which two of the following are required for endpoint compliance monitors? (Choose two.)
A. Logged on user
B. Security rule
C. Persistent agent
D. Custom scan
During the on-boarding process through the captive portal, why would a host that successfully registered remain stuck in the Registration VLAN? (Choose two.)
A. The wrong agent is installed.
B. Bridging is enabled on the host.
C. There is another unregistered host on the same port.
D. The ports default VLAN is the same as the Registration VLAN.
Which agent is used only as part of a login script?
A. Persistent
B. Passive
C. Mobile
D. Dissolvable
When you create a user or host profile; which three criteria can you use? (Choose three.)
A. An applied access policy
B. Administrative group membership
C. Location
D. Host or user group memberships
E. Host or user attributes
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
A. Both enforcement groups cannot contain the same port.
B. Only at-risk hosts would be impacted.
C. Only rogue hosts would be impacted.
D. Both types of enforcement would be applied.
What causes a host's state to change to "at risk"?
A. The host has been administratively disabled.
B. The logged on user is not found in the Active Directory.
C. The host has failed an endpoint compliance policy or admin scan.
D. The host is not in the Registered Hosts group.
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
A. The host is provisioned based on the network access policy.
B. The host is provisioned based on the default access defined by the point of connection.
C. The host is isolated.
D. The host is administratively disabled.
Refer to the exhibit.
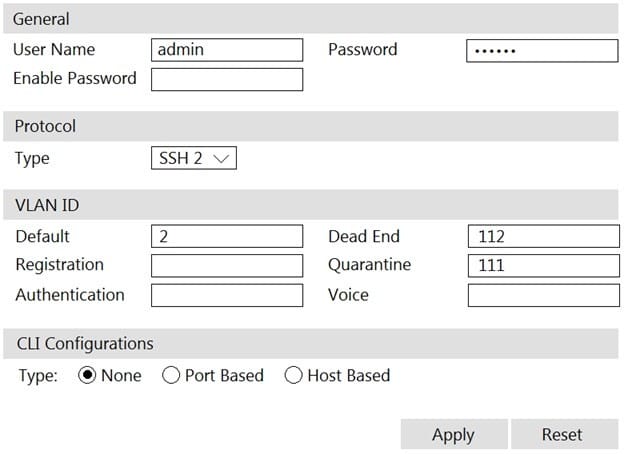
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what will occur?
A. No VLAN change is performed.
B. The host is disabled.
C. The host is moved to VLAN 111.
D. The host is moved to a default isolation VLAN.

