NSE6_FML-6.2 Online Practice Questions and Answers
An administrator sees that an excessive amount of storage space on a FortiMail device is being used up by quarantine accounts for invalid users. The FortiMail is operating in transparent mode.
Which two FortiMail features can the administrator configure to tackle this issue? (Choose two.)
A. Automatic removal of quarantine accounts
B. Recipient address verification
C. Bounce address tag verification
D. Sender address rate control
What three configuration steps are required to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
A. Generate a public/private key pair in the protected domain configuration
B. Enable DKIM check in a matching session profile
C. Enable DKIM check in a matching antispam profile
D. Publish the public key as a TXT record in a public DNS server
E. Enable DKIM signing for outgoing messages in a matching session profile
Refer to the exhibit.

Which two statements about the MTAs of the domain example.com are true? (Choose two.)
A. The external MTAs will send email to mx.example.com only if mx.hosted.com is unreachable
B. The PriNS server should receive all email for the example.com domain
C. The primary MTA for the example.com domain is mx.hosted.com
D. The higher preference value is used to load balance more email to the mx.example.com MTA
Refer to the exhibit.
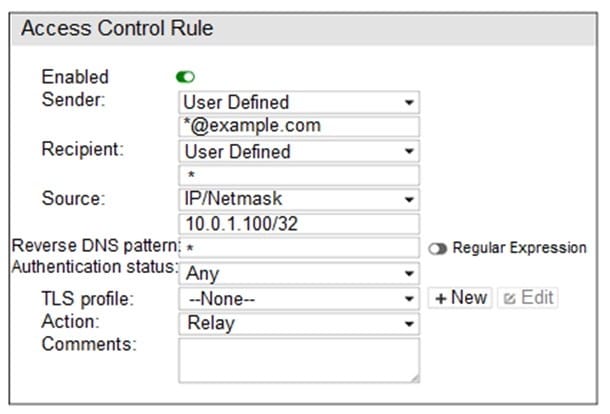
Which two statements about the access receive rule are true? (Choose two.)
A. Email matching this rule will be relayed
B. Email must originate from an example.com email address to match this rule
C. Senders must be authenticated to match this rule
D. Email from any host in the 10.0.1.0/24 subnet can match this rule
Refer to the exhibit.
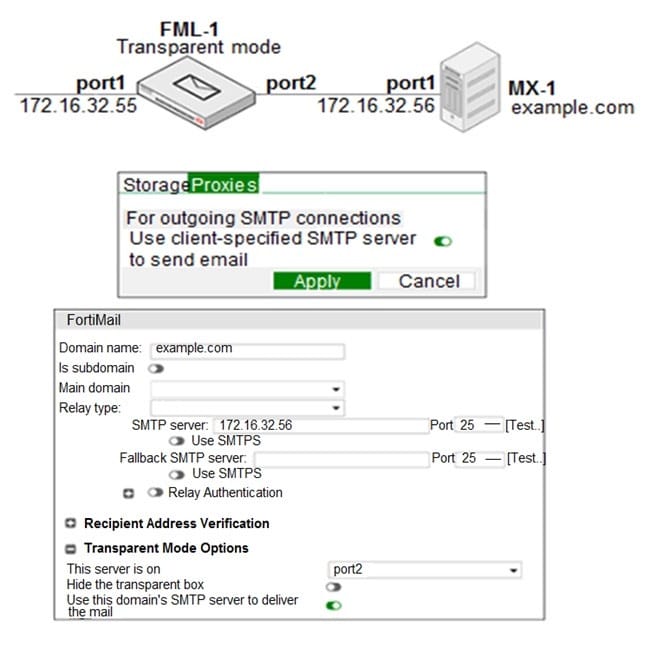
Which two statements about how the transparent mode FortiMail device routes email for the example.com domain are true? (Choose two.)
A. If incoming email messages are undeliverable, FML-1 can queue them to retry later
B. If outgoing email messages are undeliverable, FM-1 can queue them to retry later
C. FML-1 will use the built-in MTA for outgoing sessions
D. FML-1 will use the transparent proxy for incoming sessions
Refer to the exhibit.
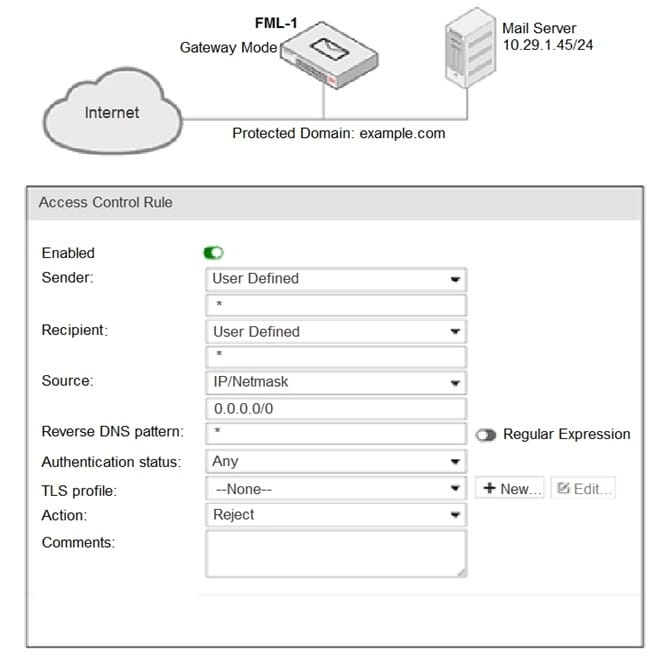
It is recommended that you configure which three access receive settings to allow outbound email from the example.com domain on FML-1? (Choose three.)
A. The Sender pattern should be set to *@example.com
B. The Action should be set to Relay
C. The Recipient pattern should be set to 10.29.1.45/24
D. The Enable check box should be cleared
E. The Sender IP/netmask should be set to 10.29.1.45/32
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to the protected domain for undeliverable email messages. After searching the logs, the administrator identifies that the DSNs were not generated as a result of any outbound email sent from the protected domain.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
A. Spam outbreak protection
B. Bounce address tag validation
C. Spoofed header detection
D. FortiGuard IP Reputation
Which two CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
A. execute formatmaildisk
B. execute formatmaildisk_backup
C. execute formatlogdisk
D. execute partitionlogdisk 40
Which FortiMail option removes embedded code components in Microsoft Word, while maintaining the original file format?
A. Behavior analysis
B. Impersonation analysis
C. Content disarm and reconstruction
D. Header analysis
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas.
Which FortiMail feature specific to server mode can be used to accomplish this?
A. Resource profiles
B. Domain-level service settings
C. Access profiles
D. Address book management options

