NSE6_FML-6.0 Online Practice Questions and Answers
Examine the FortiMail session profile and protected domain configuration shown in the exhibit; then answer the question below.
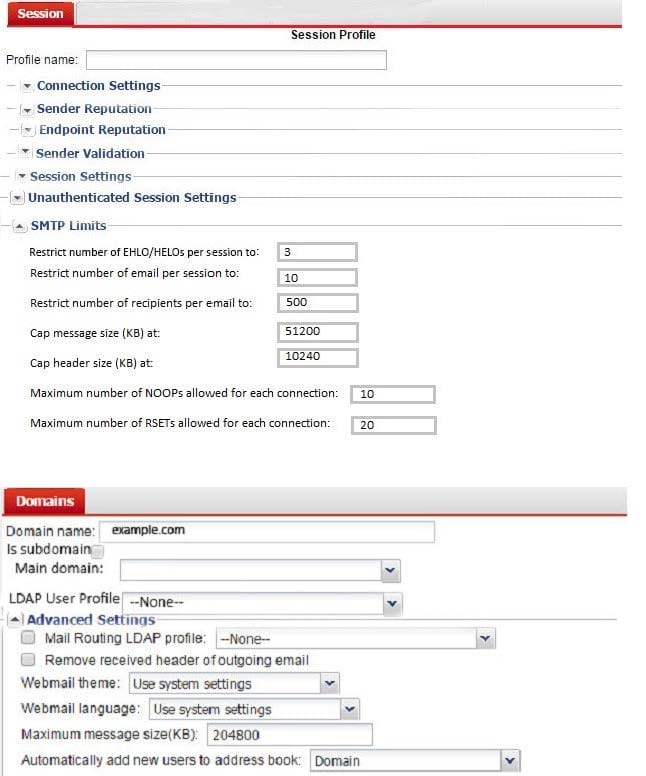
Which size limit will FortiMail apply to outbound email?
A. 204800
B. 51200 C. 1024
D. 10240
FortiMail is configured with the protected domain "example.com". Identify which of the following envelope addresses will require an access receive rule to relay for unauthenticated senders? (Choose two.)
A. MAIL FROM: [email protected] RCPT TO: [email protected]
B. MAIL FROM: [email protected] RCPT TO: [email protected]
C. MAIL FROM: [email protected] RCPT TO: [email protected]
D. MAIL FROM: [email protected] RCPT TO: [email protected]
Examine the nslookup output shown in the exhibit; then answer the question below.
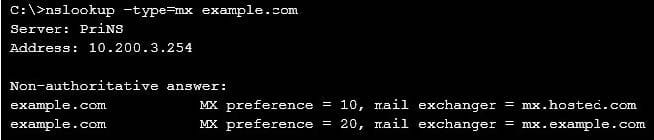
Identify which of the following statements is true regarding the example.com domain's MTAs. (Choose two.)
A. External MTAs will send email to mx.example.com only if mx.hosted.com is unreachable
B. The primary MTA for the example.com domain is mx.hosted.com
C. The PriNS server should receive all email for the example.com domain
D. The higher preference value is used to load balance more email to the mx.example.com MTA
What are the configuration steps to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
A. Enable DKIM signing for outgoing messages in a matching session profile
B. Publish the public key as a TXT record in a public DNS server
C. Enable DKIM check in a matching session profile
D. Enable DKIM check in a matching antispam profile
E. Generate a public/private key pair in the protected domain configuration
Which of the following statements are true regarding FortiMail's behavior when using the built-in MTA to process email in transparent mode? (Choose two.)
A. FortiMail can queue undeliverable messages and generate DSNs
B. If you disable the built-in MTA, FortiMail will use its transparent proxies to deliver email
C. FortiMail ignores the destination set by the sender and uses its own MX record lookup to deliver email
D. MUAs need to be configured to connect to the built-in MTA to send email
Examine the FortiMail IBE service configuration shown in the exhibit; then answer the question below.
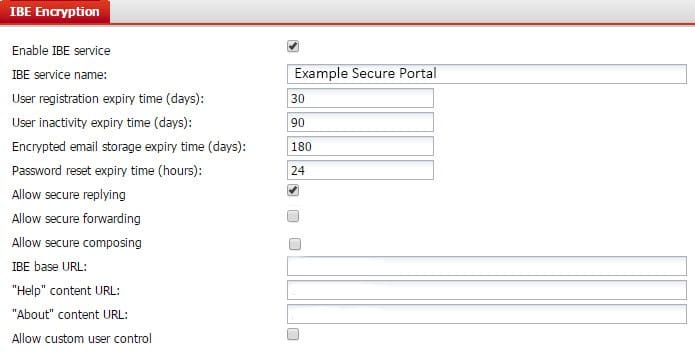
Which of the following statements describes the User inactivity expiry time of 90 days?
A. First time IBE users must register to access their email within 90 days of receiving the notification email message
B. After initial registration, IBE users can access the secure portal without authenticating again for 90 days
C. Registered IBE users have 90 days from the time they receive a notification email message to access their IBE email
D. IBE user accounts will expire after 90 days of inactivity, and must register again to access new IBE email message
Examine the exhibit; then answer the question below.
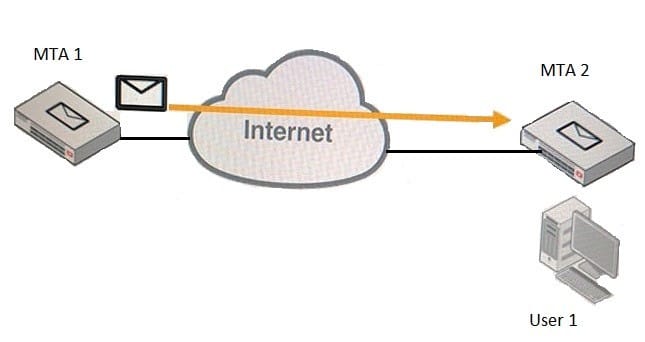
MTA 1 is delivering an email intended for User 1 to MTA 2. Which of the following statements about protocol usage between the devices are true? (Choose two.)
A. MTA 2 will use IMAP to receive the email message from MTA 1
B. MTA 1 will use SMTP to deliver the email message to MTA 2
C. User 1 will use IMAP to download the email message from MTA 2
D. MTA 1 will use POP3 to deliver the email message to User 1 directly
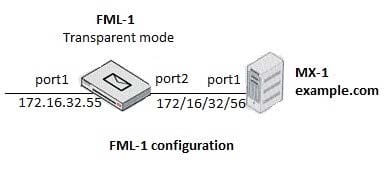
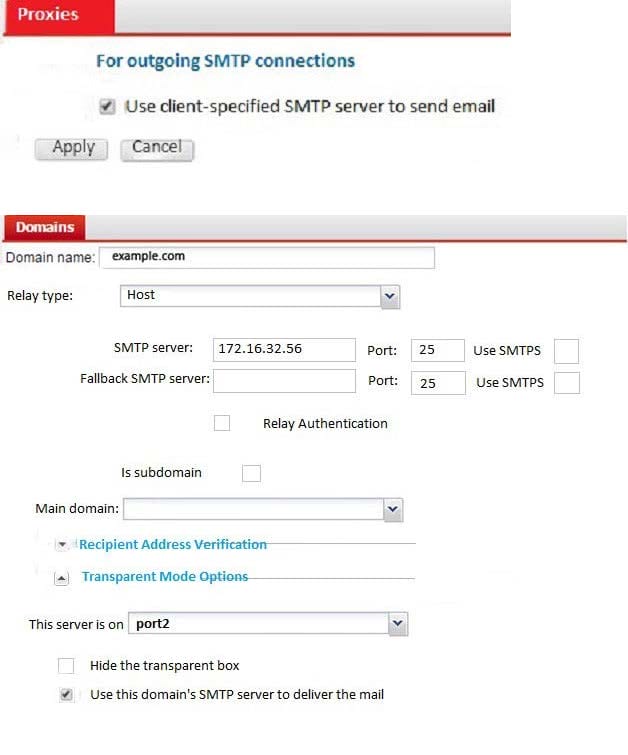
Which of the following statements are true regarding the transparent mode FortiMail's email routing for the example.com domain? (Choose two.)
A. FML-1 will use the built-in MTA for outgoing sessions
B. FML-1 will use the transparent proxy for incoming sessions
C. If incoming email are undeliverable, FML-1 can queue them to retry again later
D. If outgoing email messages are undeliverable, FML-1 can queue them to retry later
Which of the following antispam techniques queries FortiGuard for rating information? (Choose two.)
A. URI filter
B. IP reputation
C. SURBL
D. DNSBL
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas. Which FortiMail feature specific to server mode can be used to accomplish this?
A. Resource profiles
B. Address book management options
C. Access profiles
D. Domain-level service settings

