NSE6_FAC-6.1 Online Practice Questions and Answers
Which two types of digital certificates can you create in Fortiauthenticator? (Choose two)
A. Usercertificate
B. Organization validation certificate
C. Third-party root certificate
D. Local service certificate
Which FSSO discovery method transparently detects logged off users without having to rely on external features such as WMI polling?
A. Windows AD polling
B. FortiClient SSO Mobility Agent
C. Radius Accounting
D. DC Polling
You are a FortiAuthenticator administrator for a large organization. Users who are configured to use FortiToken 200 for two-factor authentication can no longer authenticate. You have verified that only the users with two-factor authentication are experiencing the issue.
What can couse this issue?
A. On of the FortiAuthenticator devices in the active-active cluster has failed
B. FortiAuthenticator has lose contact with the FortiToken Cloud servers
C. FortiToken 200 licence has expired
D. Time drift between FortiAuthenticator and hardware tokens
Which three of the following can be used as SSO sources? (Choose three)
A. FortiClient SSO Mobility Agent
B. SSH Sessions
C. FortiAuthenticator in SAML SP role
D. Fortigate
E. RADIUS accounting
How can a SAML metada file be used?
A. To defined a list of trusted user names
B. To import the required IDP configuration
C. To correlate the IDP address to its hostname
D. To resolve the IDP realm for authentication
Which interface services must be enabled for the SCEP client to connect to Authenticator?
A. OCSP
B. REST API
C. SSH
D. HTTP/HTTPS
A device or useridentity cannot be established transparently, such as with non-domain BYOD devices, and allow users to create their own credentialis.
In this case, which user idendity discovery method can Fortiauthenticator use?
A. Syslog messaging or SAML IDP
B. Kerberos-base authentication
C. Radius accounting
D. Portal authentication
Which option correctly describes an SP-initiated SSO SAML packet flow for a host without a SAML assertion?
A. Service provider contacts idendity provider, idendity provider validates principal for service provider, service provider establishes communication with principal
B. Principal contacts idendity provider and is redirected to serviceprovider, principal establishes connection with service provider, service provider validates authentication with identify provider
C. Principal contacts service provider, service provider redirects principal to idendity provider, after succesfull authentication identify provider redirects principal to service provider
D. Principal contacts idendity provider and authenticates, identity provider relays principal to service provider after valid authentication
Refer to the exhibit.
Examine the screenshot shown in the exhibit.
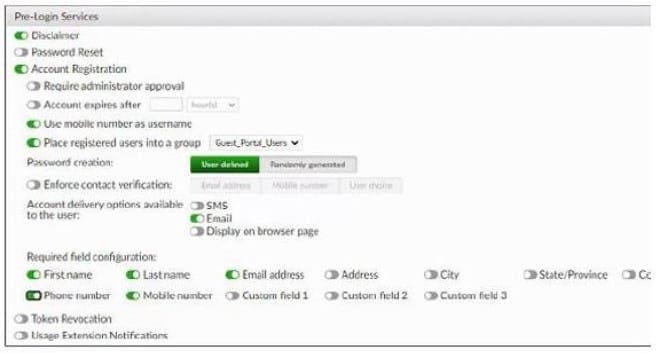
Which two statements regarding the configuration are true? (Choose two)
A. All guest accounts created using the account registration feature will be placed under the Guest_Portal_Users group
B. All accounts registered through the guest portal must be validated through email
C. Guest users must fill in all the fields on the registration form
D. Guest user account will expire after eight hours
Which statement about the guest portal policies is true?
A. Guest portal policies apply only to authentication requests coming from unknown RADIUS clients
B. Guest portal policies can be used only for BYODs
C. Conditions in the policy apply only to guest wireless users
D. All conditions in the policy must match before a user is presented with the guest portal

