NSE5_FCT-7.0 Online Practice Questions and Answers
Refer to the exhibit.
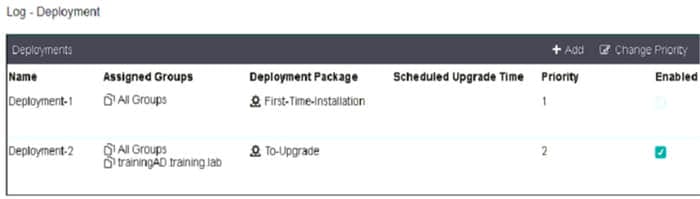
Which shows FortiClient EMS deployment profiles.
When an administrator creates a deployment profile on FortiClient EMS, which statement about the deployment profile is true?
A. Deployment-1 will install FortiClient on new AD group endpoints
B. Deployment-2 will install FortiClient on both the AD group and workgroup
C. Deployment-2 will upgrade FortiClient on both the AD group and workgroup
D. Deployment-1 will upgrade FortiClient only on the workgroup
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
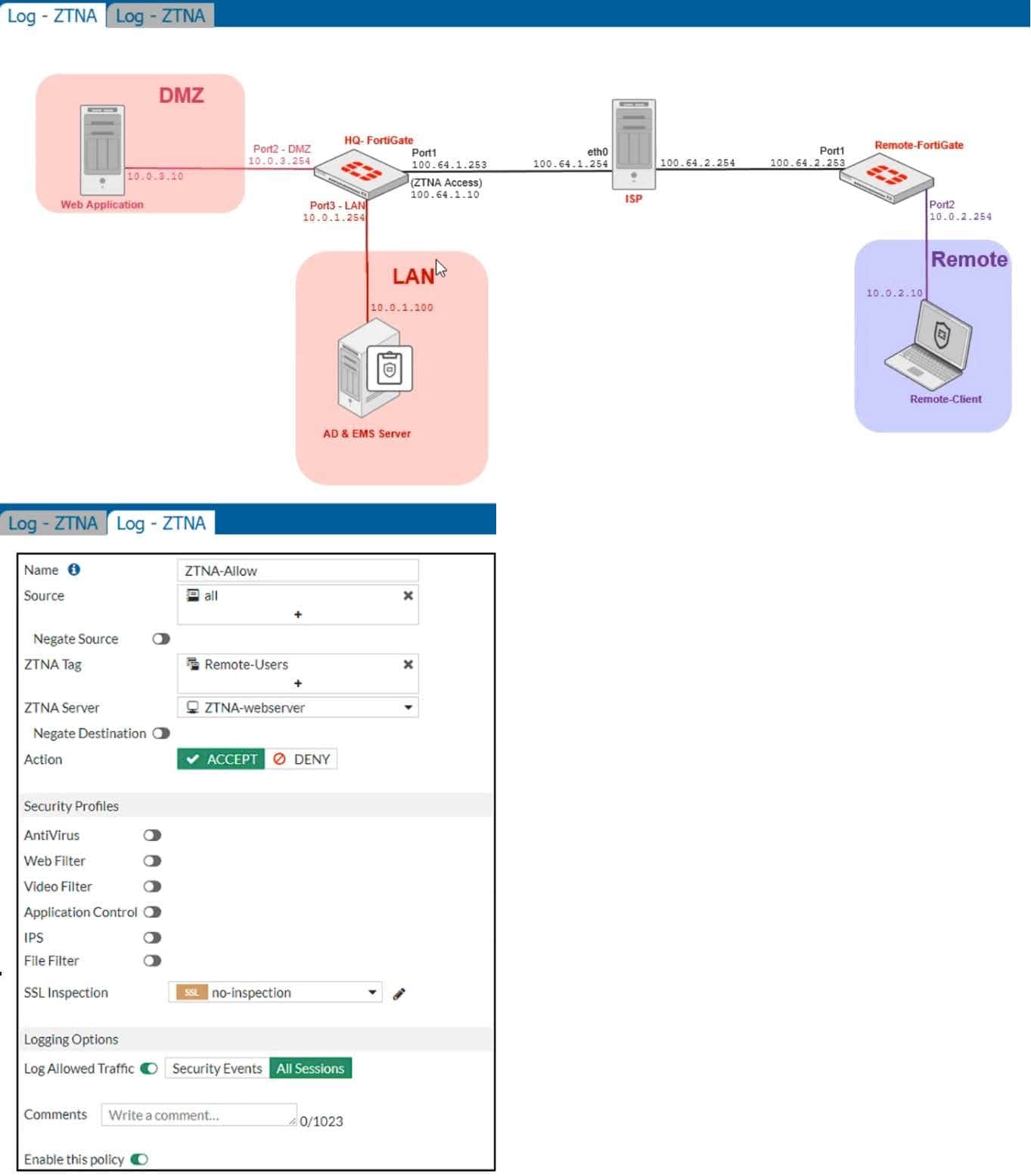
A. Remote-Client failed the client certificate authentication.
B. Remote-Client provided an empty client certificate to connect to the ZTNA access proxy.
C. Remote-Client has not initiated a connection to the ZTNA access proxy.
D. Remote-Client provided an invalid certificate to connect to the ZTNA access proxy.
Refer to the exhibit.
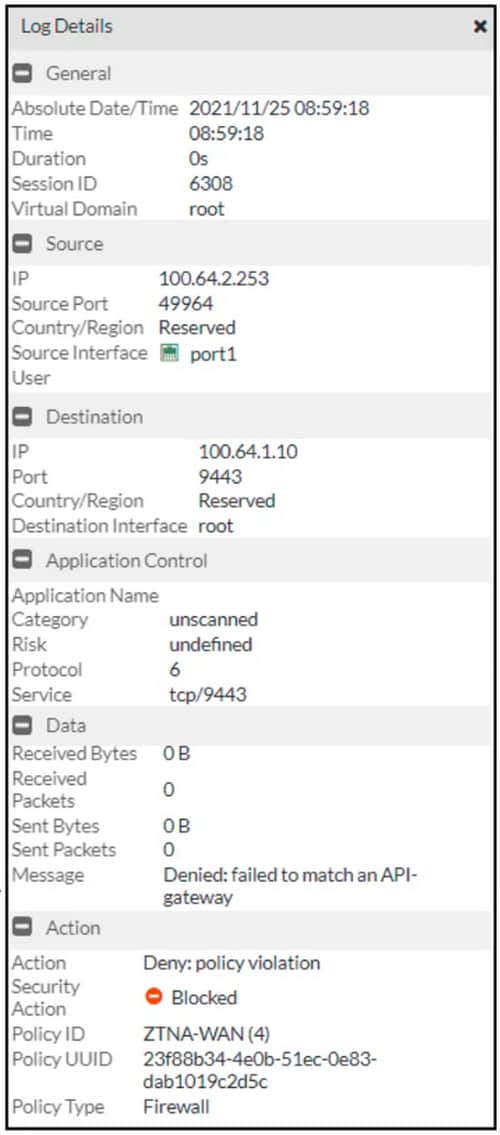
Which shows the output of the ZTNA traffic log on FortiGate. What can you conclude from the log message?
A. The remote user connection does not match the explicit proxy policy.
B. The remote user connection does not match the ZTNA server configuration.
C. The remote user connection does not match the ZTNA rule configuration.
D. The remote user connection does not match the ZTNA firewall policy
Which three types of antivirus scans are available on FortiClient? (Choose three )
A. Proxy scan
B. Full scan
C. Custom scan
D. Flow scan
E. Quick scan
Which two VPN types can a FortiClient endpoint user inmate from the Windows command prompt? (Choose two)
A. L2TP
B. PPTP
C. IPSec
D. SSL VPN
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.

Which two statements about the rule set are true? (Choose two.)
A. The endpoint must satisfy that only Windows 10 is running.
B. The endpoint must satisfy that only AV software is installed and running.
C. The endpoint must satisfy that antivirus is installed and running and Windows 10 is running.
D. The endpoint must satisfy that only Windows Server 2012 R2 is running.
Refer to the exhibit.
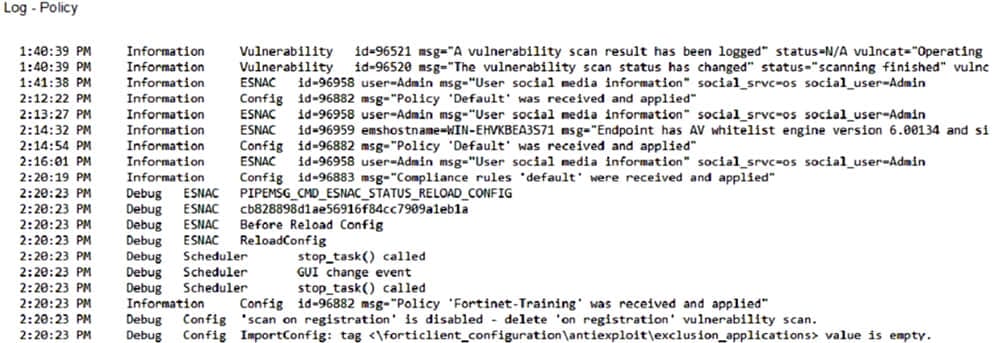
Based on the FortiClient logs shown in the exhibit which endpoint profile policy is currently applied to the FortiClient endpoint from the EMS server?
A. Default
B. Compliance rules default
C. Fortinet- Training
D. Default configuration policy
Refer to the exhibits.
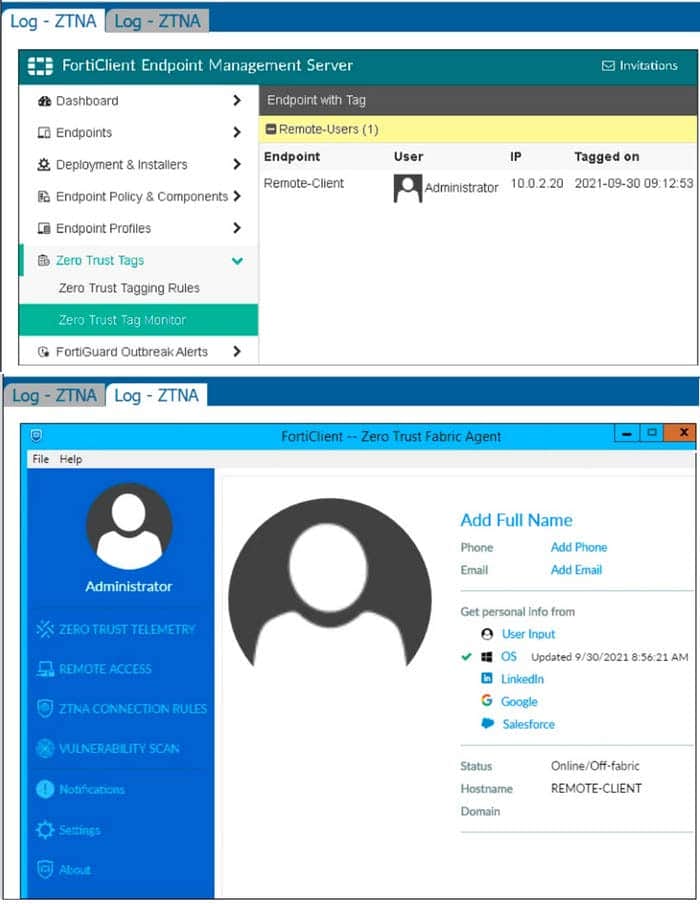
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
A. Update tagging rule logic to enable tag visibility
B. Change the FortiClient system settings to enable tag visibility
C. Change the endpoint control setting to enable tag visibility
D. Change the user identity settings to enable tag visibility
An administrator is required to maintain a software inventory on the endpoints. without showing the feature on the FortiClient dashboard What must the administrator do to achieve this requirement?
A. The administrator must use default endpoint profile
B. The administrator must not select the vulnerability scan feature in the deployment package.
C. The administrator must select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
D. The administrator must click the hide icon on the vulnerability scan tab
Refer to the exhibit.
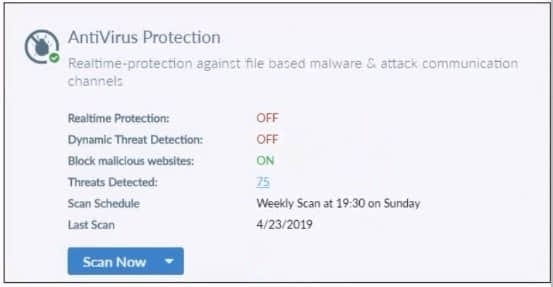
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
A. Blocks the infected files as it is downloading
B. Quarantines the infected files and logs all access attempts
C. Sends the infected file to FortiGuard for analysis
D. Allows the infected file to download without scan

