NSE5_FCT-6.2 Online Practice Questions and Answers
An administrator deploys a FortiClient installation through the Microsoft AD group policy After installation is
complete all the custom configuration is missing.
What could have caused this problem?
A. The FortiClient exe file is included in the distribution package
B. The FortiClient MST file is missing from the distribution package
C. FortiClient does not have permission to access the distribution package.
D. The FortiClient package is not assigned to the group
Which statement about FortiClient comprehensive endpoint protection is true?
A. It helps to safeguard systems from email spam
B. It helps to safeguard systems from data loss.
C. It helps to safeguard systems from DDoS.
D. lt helps to safeguard systems from advanced security threats, such as malware.
Which two VPN types can a FortiClient endpoint user inmate from the Windows command prompt? (Choose two)
A. L2TP
B. PPTP
C. IPSec
D. SSL VPN
A FortiClient EMS administrator has enabled compliance rule for the sales department Which Fortmet device will enforce compliance with dynamic access control?
A. FortiClient EMS
B. FortiAnalyzer
C. FortiGate
D. FortiClient
What action does FortiClient anti-exploit detection take when it detects exploits?
A. Terminates the compromised application process
B. Patches the compromised application process
C. Blocks memory allocation to the compromised application process
D. Deletes the compromised application process
Which three features does FortiClient endpoint security include? (Choose three )
A. L2TP
B. Real-time protection
C. DLP
D. Vulnerability management
E. IPsec
What is the function of the quick scan option on FortiClient?
A. It performs a full system scan including all files, executable files, DLLs, and drivers for threats.
B. It scans executable files. DLLs, and drivers that are currently running, for threats.
C. It allows users to select a specific file folder on your local hard disk drive (HDD), to scan for threats
D. It scans programs and drivers that are currently running for threats
Refer to the exhibit.
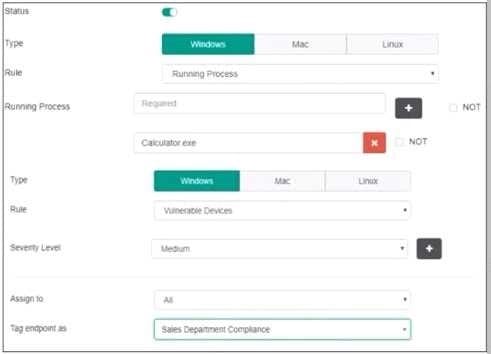
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two)
A. Integrate FortiSandbox for infected file analysis.
B. Enable the webfilter profile
C. Patch applications that have vulnerability rated as high or above.
D. Run Calculator application on the endpoint.
Refer to the exhibit.
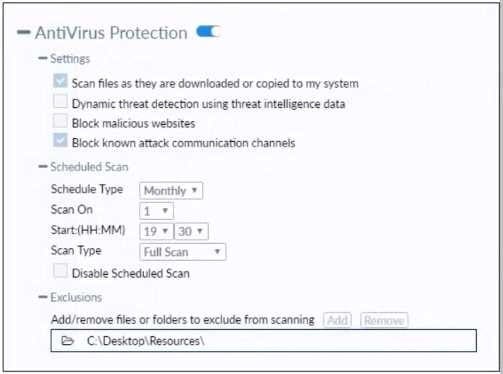
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
A. FortiClient quarantines infected files and reviews later, after scanning them.
B. FortiClient blocks and deletes infected files after scanning them.
C. FortiClient scans infected files when the user copies files to the Resources folder
D. FortiClient copies infected files to the Resources folder without scanning them.
Refer to the exhibit.
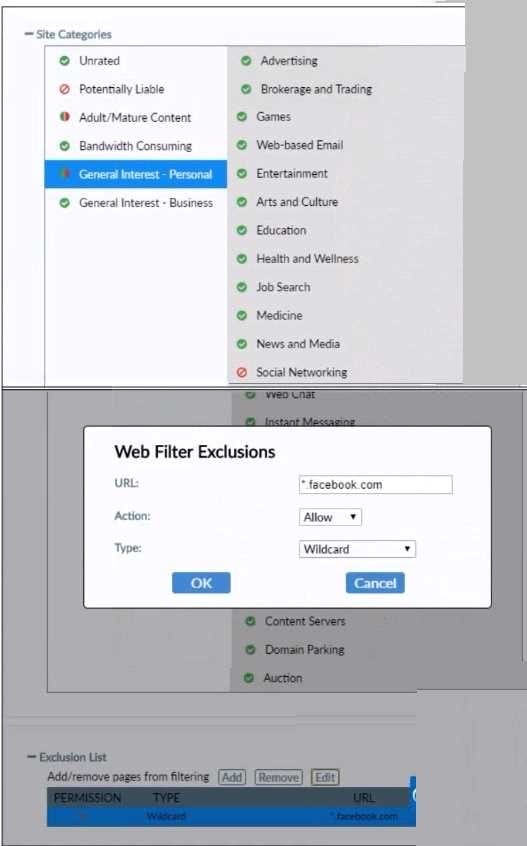
Based on the settings shown in the exhibit what action will FortiClient take when users try to access www facebook com?
A. FortiClient will allow access to Facebook.
B. FortiClient will block access to Facebook and its subdomains
C. FortiClient will prompt a warning message to warn the user before they can access the Facebook website
D. FortiClient will allow access to Facebook and log user's web access.

