NSE5_FAZ-7.0 Online Practice Questions and Answers
Refer to the exhibits.
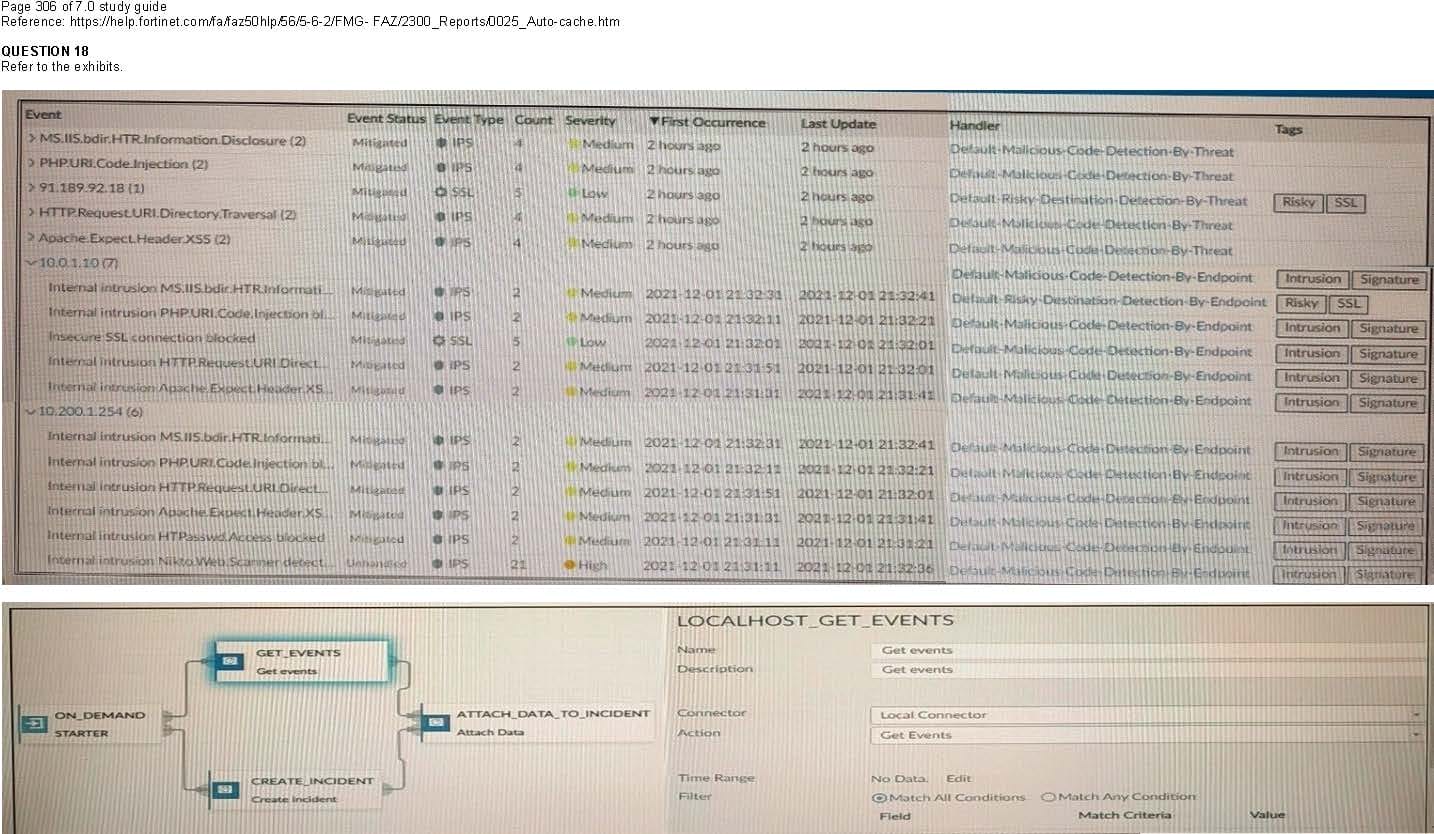
Page 306 of 7.0 study guide Reference: https://help.fortinet.com/fa/faz50hlp/56/5-6-2/FMG- FAZ/2300_Reports/0025_Auto-cache.htm
How many events will be added to the incident created after running this playbook?
A. Ten events will be added.
B. No events will be added.
C. Five events will be added.
D. Thirteen events will be added.
What statements are true regarding disk log quota? (Choose two)
A. The FortiAnalyzer stops logging once the disk log quota is met.
B. The FortiAnalyzer automatically sets the disk log quota based on the device.
C. The FortiAnalyzer can overwrite the oldest logs or stop logging once the disk log quota is met.
D. The FortiAnalyzer disk log quota is configurable, but has a minimum o 100mb a maximum based on the reserved system space.
Logs are being deleted from one of the ADOMs earlier than the configured setting for archiving in the data policy. What is the most likely problem?
A. CPU resources are too high
B. Logs in that ADOM are being forwarded, in real-time, to another FortiAnalyzer device
C. The total disk space is insufficient and you need to add other disk
D. The ADOM disk quota is set too low, based on log rates
After you have moved a registered logging device out of one ADOM and into a new ADOM, what is the purpose of running the following CLI command? execute sql-local rebuild-adom
A. To reset the disk quota enforcement to default
B. To remove the analytics logs of the device from the old database
C. To migrate the archive logs to the new ADOM
D. To populate the new ADOM with analytical logs for the moved device, so you can run reports
How can you configure FortiAnalyzer to permit administrator logins from only specific locations?
A. Use static routes
B. Use administrative profiles
C. Use trusted hosts
D. Use secure protocols
An administrator has configured the following settings:
config system fortiview settings set resolve-ip enable end
What is the significance of executing this command?
A. Use this command only if the source IP addresses are not resolved on FortiGate.
B. It resolves the source and destination IP addresses to a hostname in FortiView on FortiAnalyzer.
C. You must configure local DNS servers on FortiGate for this command to resolve IP addresses on Forti Analyzer.
D. It resolves the destination IP address to a hostname in FortiView on FortiAnalyzer.
What is the purpose of a predefined template on the FortiAnalyzer?
A. It can be edited and modified as required
B. It specifies the report layout which contains predefined texts, charts, and macros
C. It specifies report settings which contains time period, device selection, and schedule
D. It contains predefined data to generate mock reports
What statements are true regarding FortiAnalyzer 's treatment of high availability (HA) dusters? (Choose two)
A. FortiAnalyzer distinguishes different devices by their serial number.
B. FortiAnalyzer receives logs from d devices in a duster.
C. FortiAnalyzer receives bgs only from the primary device in the cluster.
D. FortiAnalyzer only needs to know (he serial number of the primary device in the cluster-it automaticaly discovers the other devices.
Which two elements are contained in a system backup created on FortiAnalyzer? (Choose two.)
A. System information
B. Logs from registered devices
C. Report information
D. Database snapshot
You crested a playbook on FortiAnalyzer that uses a FortiOS connector
When configuring the FortiGate side, which type of trigger must be used so that the actions in an automation stitch are available in the FortiOS connector?
A. FortiAnalyzer Event Handler
B. Incoming webhook
C. FortiOS Event Log
D. Fabric Connector event

