NSE5_EDR-5.0 Online Practice Questions and Answers
Refer to the exhibit.

Based on the event shown in the exhibit, which two statements about the event are true? (Choose two.)
A. The NGAV policy has blocked TestApplication exe
B. TestApplication exe is sophisticated malware
C. The user was able to launch TestApplication exe
D. FCS classified the event as malicious
A company requires a global communication policy for a FortiEDR multi-tenant environment.
How can the administrator achieve this?
A. An administrator creates a new communication control policy and shares it with other organizations
B. A local administrator creates new a communication control policy and shares it with other organizations
C. A local administrator creates a new communication control policy and assigns it globally to all organizations
D. An administrator creates a new communication control policy for each organization
Exhibit.
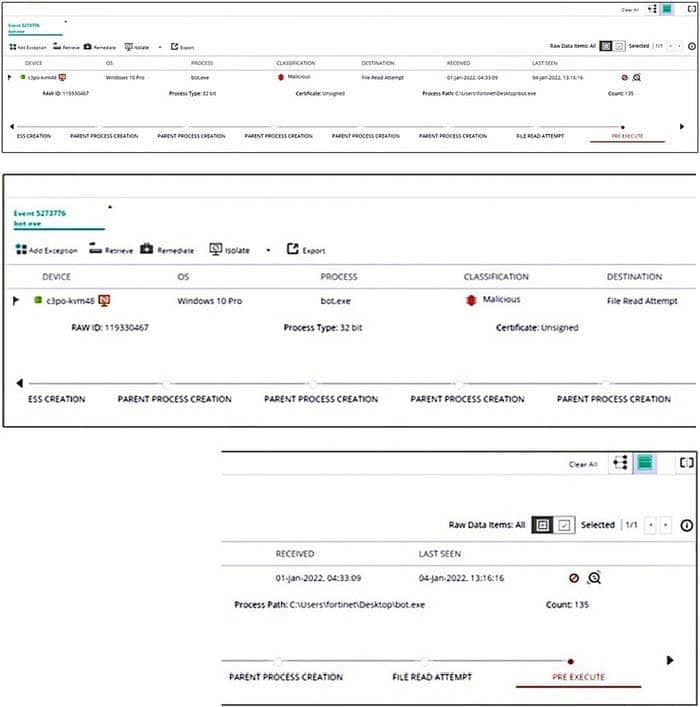
Based on the forensics data shown in the exhibit, which two statements are true? (Choose two.)
A. An exception has been created for this event
B. The forensics data is displayed m the stacks view
C. The device has been isolated
D. The exfiltration prevention policy has blocked this event
Refer to the exhibit.
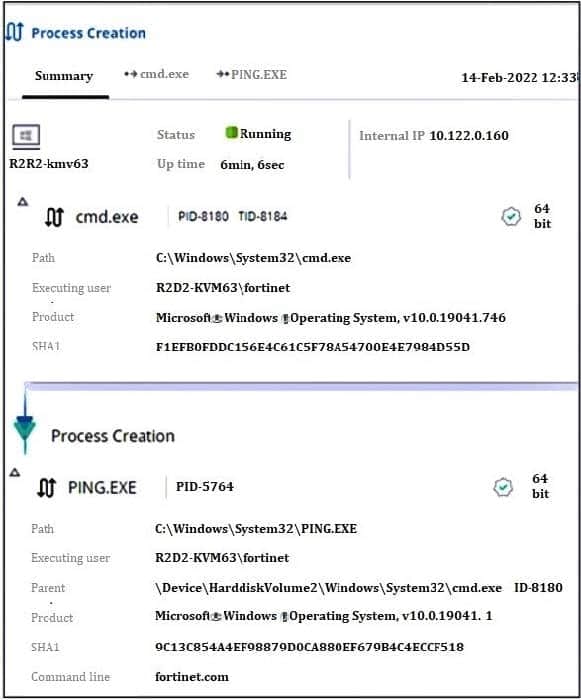
Based on the threat hunting event details shown in the exhibit, which two statements about the event are true? (Choose two.)
A. The PING EXE process was blocked
B. The user fortinet has executed a ping command
C. The activity event is associated with the file action
D. There are no MITRE details available for this event
An administrator finds a third party free software on a user's computer mat does not appear in me application list in the communication control console
Which two statements are true about this situation? (Choose two)
A. The application is allowed in all communication control policies
B. The application is ignored as the reputation score is acceptable by the security policy
C. The application has not made any connection attempts
D. The application is blocked by the security policies
Which FortiEDR component must have JumpBox functionality to connect with FortiAnalyzer?
A. Collector
B. Core
C. Central manager
D. Aggregator
Which three steps does FortiXDR perform to find and prevent cyberattacks? (Choose three.)
A. Extended analysis
B. Extended detection
C. Extended discovery
D. Extended investigation
E. Extended response
When installing a FortiEDR collector, why is a `Registration Password' for collectors needed?
A. To restrict installation and uninstallation of collectors
B. To verify Fortinet support request
C. To restrict access to the management console
D. To verify new group assignment
Refer to the exhibit.
The exhibit shows an event viewer.
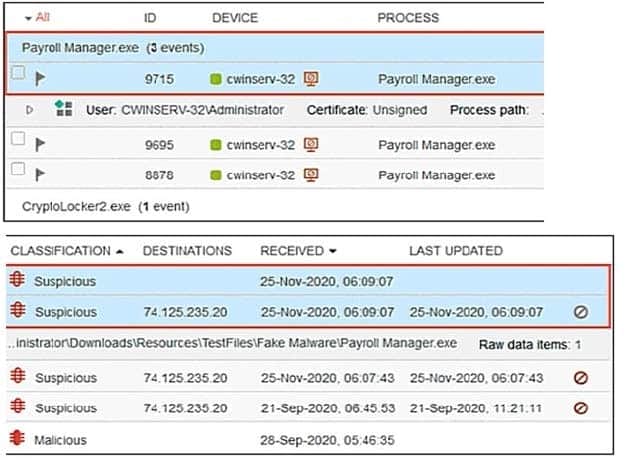
What is true about the Payroll Manager.exe event?
A. An event has not been handled by a console admin
B. An event has been deleted
C. A rule assigned action is set to block but the policy is in simulation mode
D. An event has been handled by the communication control policy
Which statement is true about the flow analyzer view in forensics?
A. It displays a graphic flow diagram.
B. Two events can be compared side-by-side.
C. It shows details about processes and sub processes.
D. The stack memory of a specific device can be retrieved

