NSE4_FGT-6.4 Online Practice Questions and Answers
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two)
A. Lookup is done on the first packet from the session originator
B. Lookup is done on the last packet sent from the responder
C. Lookup is done on every packet, regardless of direction
D. Lookup is done on the trust reply packet from the responder
An administrator has configured outgoing Interface any in a firewall policy. Which statement is true about the policy list view?
A. Policy lookup will be disabled.
B. By Sequence view will be disabled.
C. Search option will be disabled
D. Interface Pair view will be disabled.
Refer to the exhibit.
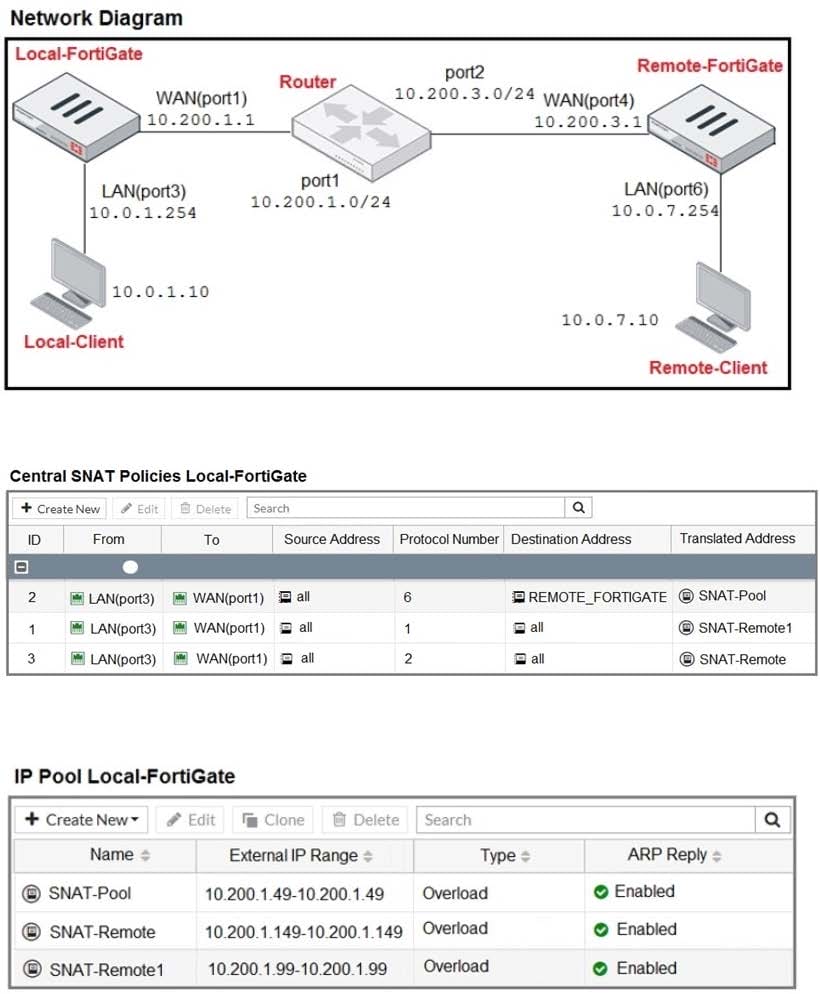
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP
address of Remote-FortiGate (10.200.3.1)?
A. 10.200.1.149
B. 10.200.1.1
C. 10.200.1.49
D. 10.200.1.99
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
A. Application control is not enabled
B. SSL/SSH Inspection profile is incorrect
C. Antivirus profile configuration is incorrect
D. Antivirus definitions are not up to date
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
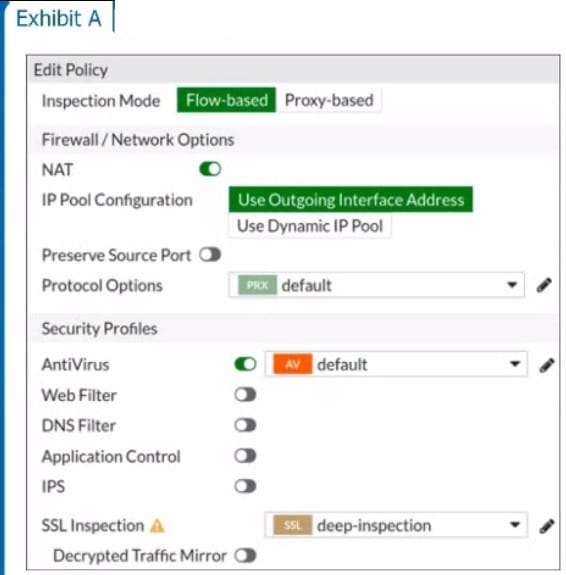
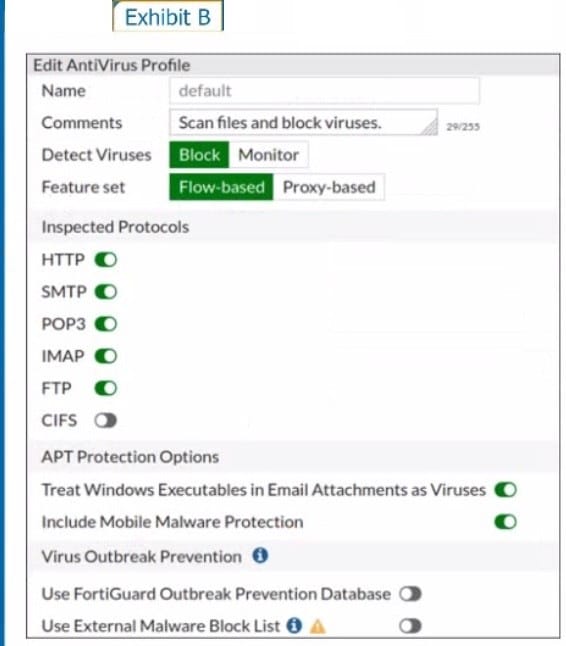
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
A. The firewall policy performs the full content inspection on the file.
B. The flow-based inspection is used, which resets the last packet to the user.
C. The volume of traffic being inspected is too high for this model of FortiGate.
D. The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
Refer to the exhibit.
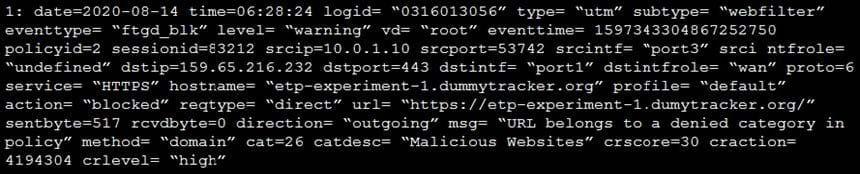
Based on the raw log, which two statements are correct? (Choose two.)
A. Traffic is blocked because Action is set to DENY in the firewall policy.
B. Traffic belongs to the root VDOM.
C. This is a security log.
D. Log severity is set to error on FortiGate.
Consider the topology:
Application on a Windows machine <--{SSL VPN}-->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
A. Set the maximum session TTL value for the TELNET service object.
B. Set the session TTL on the SSLVPN policy to maximum, so the idle session timeout will not happen after 90 minutes.
C. Create a new service object for TELNET and set the maximum session TTL.
D. Create a new firewall policy and place it above the existing SSLVPN policy for the SSL VPN traffic, and set the new TELNET service object in the policy.
Which of the following SD-WAN load 璪alancing method use interface weight value to distribute traffic? (Choose two.)
A. Source IP
B. Spillover
C. Volume
D. Session
Refer to the exhibit.
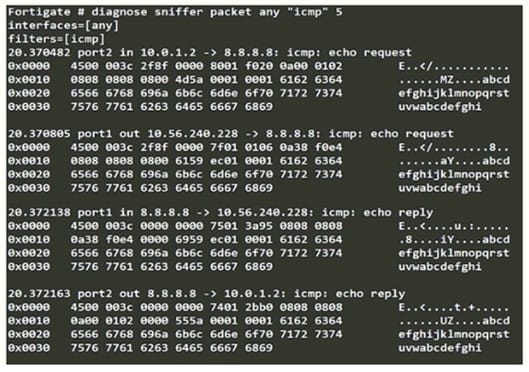
An administrator is running a sniffer command as shown in the exhibit.
Which three pieces of information are included in the sniffer output? (Choose three.)
A. Interface name
B. Ethernet header
C. IP header
D. Application header
E. Packet payload

