NSE4_FGT-6.2 Online Practice Questions and Answers
View the exhibit.
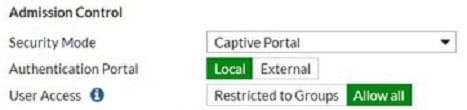
Which users and user groups are allowed access to the network through captive portal?
A. Users and groups defined in the firewall policy.
B. Only individual users ?not groups ?defined in the captive portal configuration
C. Groups defined in the captive portal configuration
D. All users
An employee connects to the https://example.com on the Internet using a web browser. The web server's certificate was signed by a private internal CA. The FortiGate that is inspecting this traffic is configured for full SSL inspection.
This exhibit shows the configuration settings for the SSL/SSH inspection profile that is applied to the policy that is invoked in this instance. All other settings are set to defaults. No certificates have been imported into FortiGate. View the exhibit and answer the question that follows.
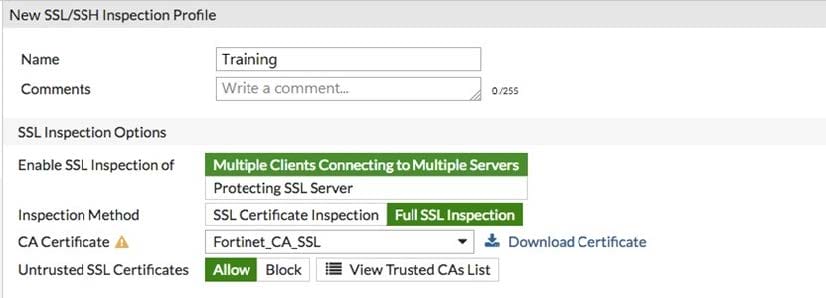
Which certificate is presented to the employee's web browser?
A. The web server's certificate.
B. The user's personal certificate signed by a private internal CA.
C. A certificate signed by Fortinet_CA_SSL.
D. A certificate signed by Fortinet_CA_Untrusted.
Examine this FortiGate configuration: How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
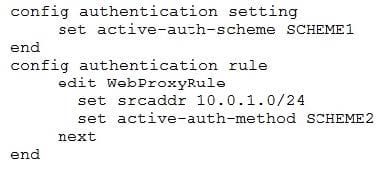
A. It always authorizes the traffic without requiring authentication.
B. It drops the traffic.
C. It authenticates the traffic using the authentication scheme SCHEME2.
D. It authenticates the traffic using the authentication scheme SCHEME1.
When override is enabled, which of the following shows the process and selection criteria that are used to elect the primary FortiGate in an HA cluster?
A. Connected monitored ports > HA uptime > priority > serial number
B. Priority > Connected monitored ports > HA uptime > serial number
C. Connected monitored ports > priority > HA uptime > serial number
D. HA uptime > priority > Connected monitored ports > serial number
An administrator has configured a route-based IPsec VPN between two FortiGate devices. Which statement about this IPsec VPN configuration is true?
A. A phase 2 configuration is not required.
B. This VPN cannot be used as part of a hub-and-spoke topology.
C. A virtual IPsec interface is automatically created after the phase 1 configuration is completed.
D. The IPsec firewall policies must be placed at the top of the list.
If traffic matches a DLP filter with the action set to Quarantine IP Address, what action does FortiGate take?
A. It notifies the administrator by sending an email.
B. It provides a DLP block replacement page with a link to download the file.
C. It blocks all future traffic for that IP address for a configured interval.
D. It archives the data for that IP address.
By default, when logging to disk, when does FortiGate delete logs?
A. 30 days
B. 1 year
C. Never
D. 7 days
Examine this output from a debug flow: Which statements about the output are correct? (Choose two.)
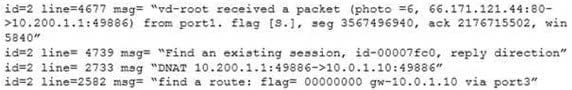
A. FortiGate received a TCP SYN/ACK packet.
B. The source IP address of the packet was translated to 10.0.1.10.
C. FortiGate routed the packet through port 3.
D. The packet was allowed by the firewall policy with the ID 00007fc0.
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
Examine the two static routes shown in the exhibit, then answer the following question.
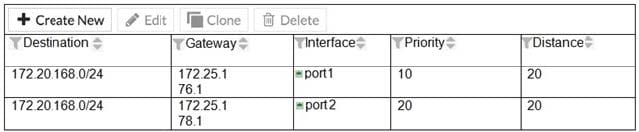
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
A. FortiGate will load balance all traffic across both routes.
B. FortiGate will use the port1 route as the primary candidate.
C. FortiGate will route twice as much traffic to the port2 route
D. FortiGate will only actuate the port1 route in the routing table

