NSE4-5.4 Online Practice Questions and Answers
When performing a log search on a FortiAnalyzer, it is generally recommended to use the Quick Search option. What is a valid reason for using the Full Search option, instead?
A. The search items you are looking for are not contained in indexed log fields.
B. A quick search only searches data received within the last 24 hours.
C. You want the search to include the FortiAnalyzer's local logs.
D. You want the search to include content archive data as well.
Which of the following statements best describe the main requirements for a traffic session to be offload eligible to an NP6 processor? (Choose three.)
A. Session packets do NOT have an 802.1Q VLAN tag.
B. It is NOT multicast traffic.
C. It does NOT require proxy-based inspection.
D. Layer 4 protocol must be UDP, TCP, SCTP or ICMP.
E. It does NOT require flow-based inspection.
Review the CLI configuration below for an IPS sensor and identify the correct statements regarding this configuration from the choices below. (Select all that apply.)
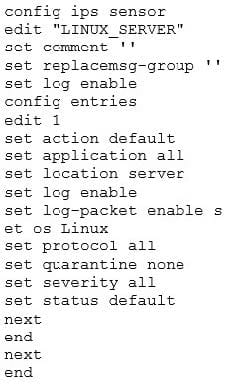
A. The sensor will log all server attacks for all operating systems.
B. The sensor will include a PCAP file with a trace of the matching packets in the log message of any matched signature.
C. The sensor will match all traffic from the address object `LINUX_SERVER'.
D. The sensor will reset all connections that match these signatures.
E. The sensor only filters which IPS signatures to apply to the selected firewall policy.
What are required to be the same for two FortiGate units to form an HA cluster? (Choose two)
A. Firmware.
B. Model.
C. Hostname.
D. System time zone.
Which of the following statements are true about PKI users created in a FortiGate device? (Choose two.)
A. Can be used for token-based authentication
B. Can be used for two-factor authentication
C. Are used for certificate-based authentication
D. Cannot be members of user groups
Under the System Information widget on the dashboard, which of the following actions are available for the system configuration? (Select all that apply.)
A. Backup
B. Restore
C. Revisions
D. Export
Two-factor authentication is supported using the following methods? (Select all that apply.)
A. FortiToken
B. Email
C. SMS phone message
D. Code books
An issue could potentially occur when clicking Connect to start tunnel mode SSL VPN. The tunnel will start up for a few seconds, then shut down. Which of the following statements best describes how to resolve this issue?
A. This user does not have permission to enable tunnel mode. Make sure that the tunnel mode widget has been added to that user's web portal.
B. This FortiGate unit may have multiple Internet connections. To avoid this problem, use the appropriate CLI command to bind the SSL VPN connection to the original incoming interface.
C. Check the SSL adaptor on the host machine. If necessary, uninstall and reinstall the adaptor from the tunnel mode portal.
D. Make sure that only Internet Explorer is used. All other browsers are unsupported.
Which of the following regular expression patterns make the terms "confidential data" case insensitive?
A. [confidential data]
B. /confidential data/i
C. i/confidential data/ D. "confidential data"
How is the FortiGate password recovery process?
A. Interrupt boot sequence, modify the boot registry and reboot. After changing the password, reset the boot registry.
B. Log in through the console port using the "maintainer" account within several seconds of physically power cycling the FortiGate.
C. Hold down the CTRL + Esc (Escape) keys during reboot, then reset the admin password.
D. Interrupt the boot sequence and restore a configuration file for which the password has been modified.

