MS-500 Online Practice Questions and Answers
DRAG DROP
You have a Microsoft 365 tenant.
User attributes are synced from your company's human resources (HR) system to Azure Active Directory (Azure AD).
The company has four departments that each has its own Microsoft SharePoint Online site. Each site must be accessed only by the users from its respective department.
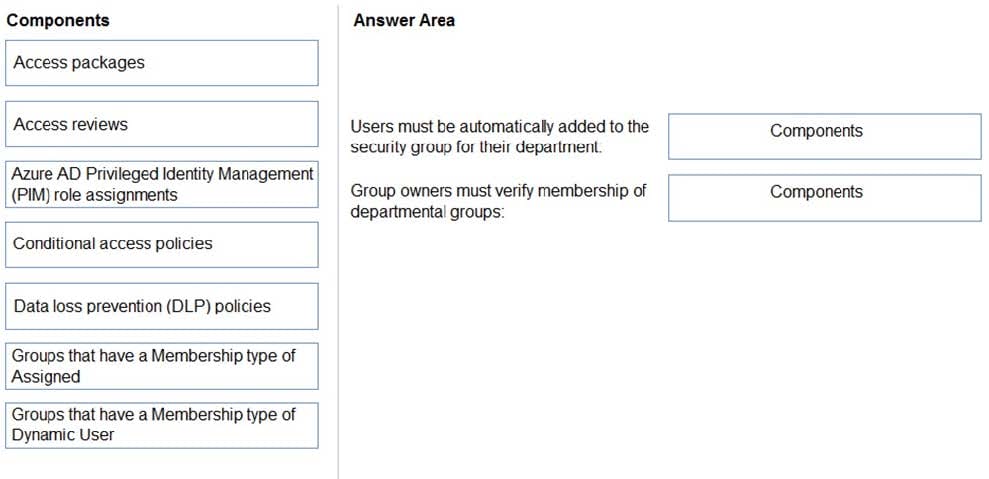
You are designing an access management solution that has the following requirements:
1.
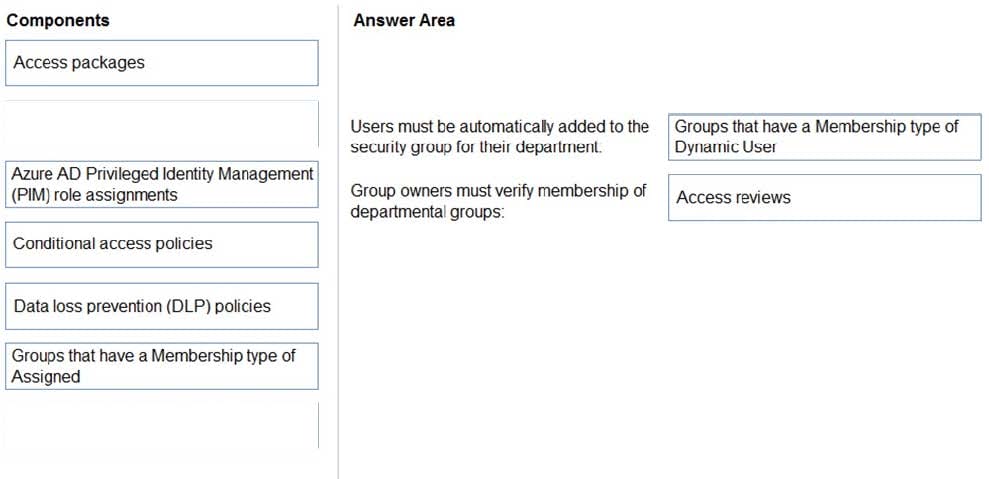
Users must be added automatically to the security group of their department.
2.
All security group owners must verify once quarterly that only the users in their department belong to their group.
Which components should you recommend to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may only be used once, more than once, or not at all. You may need to drag
the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
HOTSPOT
You have a Microsoft 365 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
You need to recommend an Azure AD Privileged Identity Management (PIM) solution that meets the following requirements:
1.
Administrators must be notified when the Security administrator role is activated.
2.
Users assigned the Security administrator role must be removed from the role automatically if they do not sign in for 30 days.
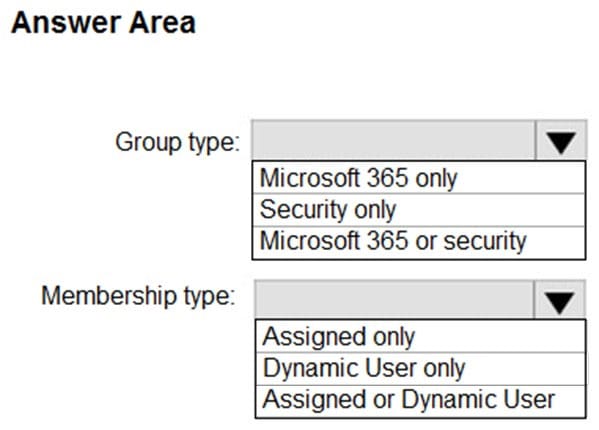
Which Azure AD PIM setting should you recommend configuring for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

HOTSPOT
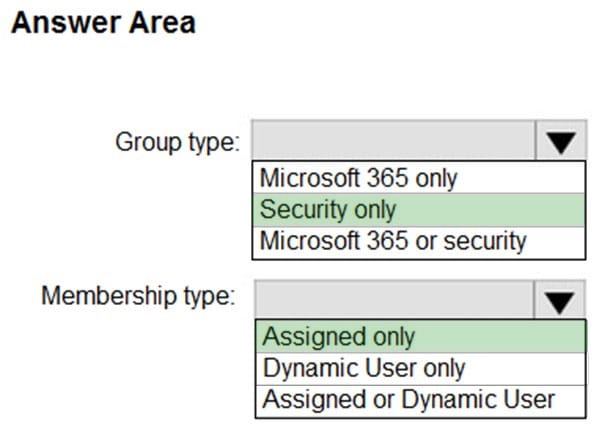
You have a Microsoft 365 E5 subscription.
You need to create a role-assignable group. The solution must ensure that you can nest the group.
How should you configure the group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
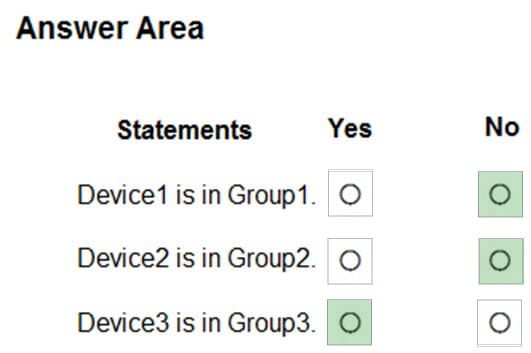
You create device groups in Microsoft Defender for Endpoint as shown in the following table.
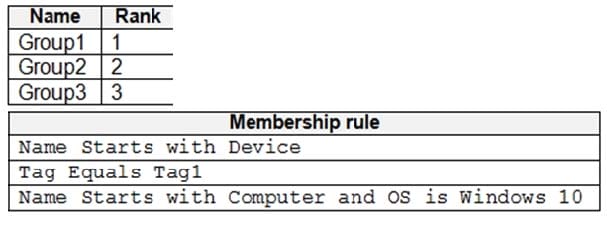
You onboard three devices to Microsoft Defender for Endpoint as shown in the following table.
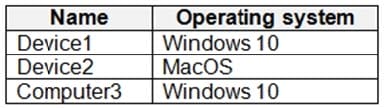
After the devices are onboarded, you perform the following actions:
1.
Add a tag named Tag1 to Device1.
2.
Rename Computer3 as Device3.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
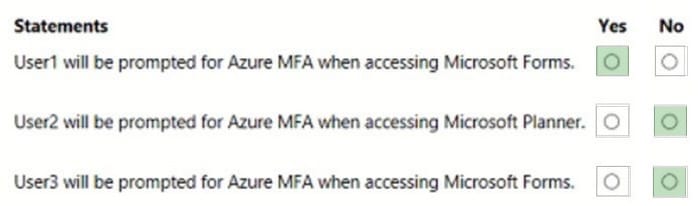
You have a Microsoft 365 subscription that contains three users named User1, User2, and User3.
You have the named locations shown in the following table.
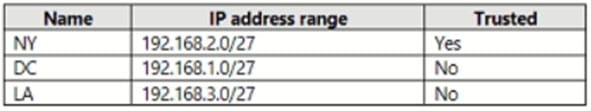
You configure an Azure Multi-Factor Authentication (MFA) trusted IP address range of 192.168.1.0/27. You have the Conditional Access policies shown in the following table.
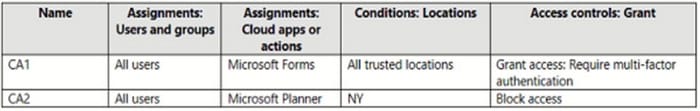
The users have the IP addresses shown in the following table.
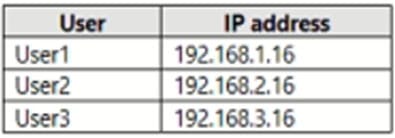
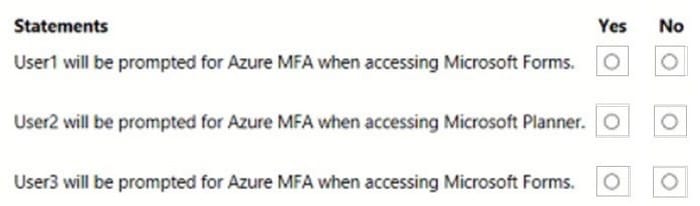
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
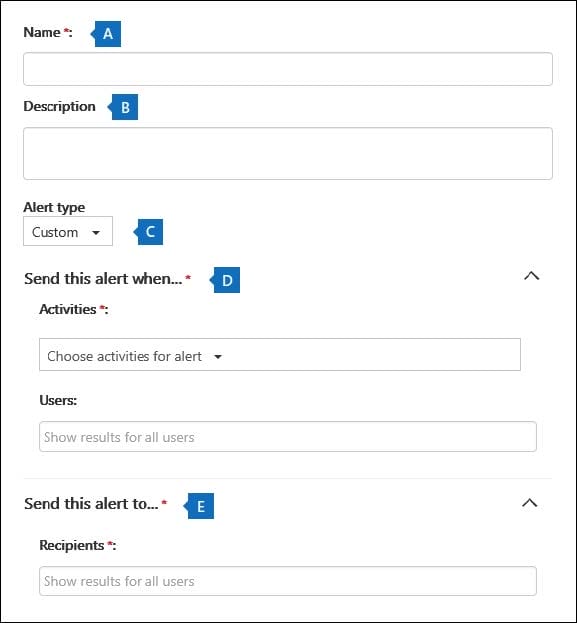
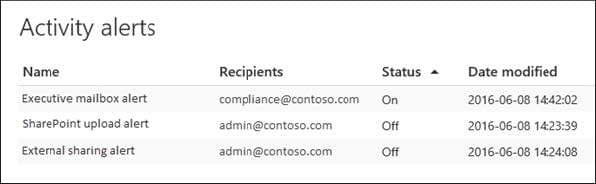
You need to ensure that [email protected] receives an alert when a user establishes a sync relationship to a document library from a computer that is a member of an Active Directory (AD) domain.
To complete this task, sign in to the Microsoft Office 365 admin center.
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector.
You need to assign built-in role-based access control (RBAC) roles to achieve the following tasks:
Create and run playbooks.
Manage incidents.
The solution must use the principle of least privilege.
Which two roles should you assign? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Automation Operator
B. Azure Sentinel responder
C. Automation Runbook Operator
D. Azure Sentinel contributor
E. Logic App contributor
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
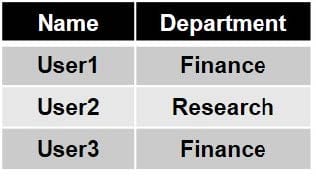
You need to prevent users in the finance department from sharing files with users in the research department. Which type of policy should you configure?
A. Conditional Access
B. insider risk management
C. information barrier
D. communication compliance
You configure several Microsoft Defender for Office 365 policies in a Microsoft 365 subscription.
You need to allow a user named User1 to view Microsoft Defender for Office 365 reports in the Threat management dashboard.
Which role provides User1 with the required role permissions?
A. Security reader
B. Compliance administrator
C. Information Protection administrator
D. Exchange administrator
You need to create Group2.
What are two possible ways to create the group?
A. an Office 365 group in the Microsoft 365 admin center
B. a mail-enabled security group in the Microsoft 365 admin center
C. a security group in the Microsoft 365 admin center
D. a distribution list in the Microsoft 365 admin center
E. a security group in the Azure AD admin center