JPR-934 Online Practice Questions and Answers
The company consists of an Active Directory domain called ABC.com. All servers on the corporate network run Windows Server.
The network contains a server that runs Internet Authentication Service (IAS) called ABC-SR01. ABC-SR01also runs the Routing and Remote Access service to provide VPN access to the network for external users. During routine monitoring
you discover that an external unauthorized user is trying to access the network through ABC-SR01.
How would you set up ABC-SR01 to log the IP addresses of the remote computers when they attempt to connect to the network using the VPN connection?
A. Log the details of the access attempts by the VPN users by using IAS to configure the Authentication requests option enabled in the Remote Access Logging.
B. Log the details of the access attempts by the VPN users by configuring the Routing and Remote Access service to log all IPSec connections.
C. Log the details of the access attempts by the VPN users by enabling auditing of TCP/IP.sys.
D. Log the details of the access attempts by the VPN users by enabling auditing of all Account Logon events on a domain controller.
You administer your company's Web site, which contains executable programs. You want to provide the highest level of trust to Internet users who download your programs, and you want to ensure that users' browsers will allow them to
download the programs. Your company's network includes an enterprise root Certification Authority (CA) and an issuing enterprise subordinate CA.
Which of the following actions should you take?
A. Request a Code Signing certificate from your company's enterprise subordinate CA.
B. Request a Code Signing certificate from a commercial CA.
C. Request a User Signature Only certificate from your company's enterprise subordinate CA.
D. Request a User Signature Only certificate from a commercial CA.
You are the backup administrator for your company. You are responsible for ensuring that all data on ten files servers are protected against data loss. Normal business hours from 8 A.M. to 5 P.M., Monday through Friday, are observed.
Network access is prohibited outside normal business hours.
A member server named File1 contains shared folder accessed by users in the sales department. The disk structure of File1 is shown in the following exhibit:
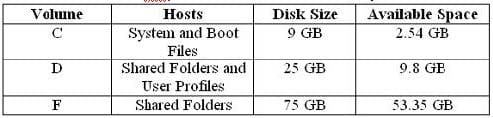
You have scheduled a daily backup of File1 as shown in the exhibit. (Click the Exhibit(s) button.) Users in the Sales department frequently leave documents open on their desktops when they leave work. These users occasionally request that
you restore a previous version of a file from backup. However, some of these files are not included in recent backup sets. You must modify the backup procedures for File1 so that all files, including open documents, will be included in the daily
backup. You also want to provide users with the ability to restore their files.
What should you do? (Choose all that apply. Each correct answer presents part of the solution.)
A. Move all shared user data folders from drive D to drive F.
B. Move all shared folders user data from drive F to drive D.
C. Enable Shadow Copies of Shared Folders on drive F.
D. Enable Volume shadow copy for the scheduled backup job.
E. Select the Disable volume shadow copy option for the scheduled backup job.
F. Install the Previous Versions Client software on all Sales department computers.
G. Create a new daily backup job by using the same settings, but clear the Disable volume shadow copy option.
You are proposing the purchase of a new e-mail server for your corporate network. You have specified a new server from a major OEM manufacturer that is configured with a powerful quad-processor configuration, hot-swappable hard drives, and redundant power supplies and network adapters, with a three-year onsite warranty. Due to a budget crunch, the chairperson of the budget committee has suggested that the company can make do with a less powerful workgroup server from a local computer store. This server has only a single processor and no redundancy features, and a one-year onsite warranty. What reasons can you provide the budget committee members that might convince them to authorize the purchase of the server that you specified, even though it has a higher price tag?
A. A more powerful server will provide better performance and scalability as the company's needs grow over time.
B. Redundant hardware components will increase the server's availability to service the needs of the company's users and customers.
C. The extended warranty on the more powerful server will increase support costs over time, since you’re paying to cover the machine under warranty for three times as long.
D. Windows Server requires at least a dual-processor configuration.
You have an IAS server running Windows Server. It supports a group of RRAS servers used to manage VPN connections for clients. You are configuring the authentication methods for the IAS server and want to allow the clients to use smart cards for secure and convenient authentication. Which of the following authentication protocols should you select?
A. MS-CHAP
B. EAP-TLS
C. MD5 CHAP
D. MS-CHAP v2
You have configured an RRAS server on one Windows Server computer and an IAS server on another, and configured the RRAS server to use the IAS server for authentication. In RADIUS terminology, which computer(s) are referred to as network access servers?
A. The IAS server
B. The RRAS servers
C. The clients of the RRAS server
D. Both the IAS and RRAS servers
You want to use the RSoP tool in logging mode to build some reports on the existing policy settings of one of your client computers. You have used RSoP before in planning mode, but never in logging mode. You open the RSoP Wizard from the Active Directory Users and Computers console, as you’ve done before, but you notice that there is no mechanism for selecting the mode, and only planning mode seems to be available. What is the problem?
A. The RSoP Wizard runs only in planning mode.
B. You should open the RSoP Wizard from Active Directory Sites and Services instead.
C. You should open the RSoP Wizard from the RSoP MMC instead.
D. You can select logging mode when you open the RSoP in Active Directory Users and Computers. You must have overlooked the option.
You are implementing a new wireless network and need to change the default settings for the equipment on the WLAN. What information should you change? (Select all that apply.)
A. SSID password
B. SSID network name
C. Domain Administrator password
D. Domain Administrator account should be renamed
You are setting up a procedure to keep documents exchanged between members of the R and D department secret. They will be sending these documents across the Internet to each other. Which PKI process will you need to employ to achieve this?
A. Confidentiality
B. Non-repudiation
C. Authentication
D. Data Integrity
You work as the network administrator at ABC.com. The ABC.com network has a domain named ABC.com. The servers at the ABC.com network run Windows Server. ABC.com has a subsidiary named Test Labs, Inc. that has a domain
named testlabs.com.
The ABC.com network has a DNS server named ABC-SR05. ABC-SR05 acts as a secondary zone for testlabs.com
What actions must you take to track when the DNS server at Test Labs, Inc. sends notifications of modifications in the zone of testlabs.com to ABC-SR05?
A. You must run the gpresult command in verbose mode.
B. You must select debug logging and set the log to store Notification events on ABC- SR05.
C. You must run the secedit command in analysis mode.
D. You must configure a two-way initiated demand-dial connection.

