JN0-681 Online Practice Questions and Answers
You need to add perimeter security to the network shown in the exhibit. All traffic must be inspected for attacks. The edge routers are using all available ports. Your solution must maintain both port and device resiliency.
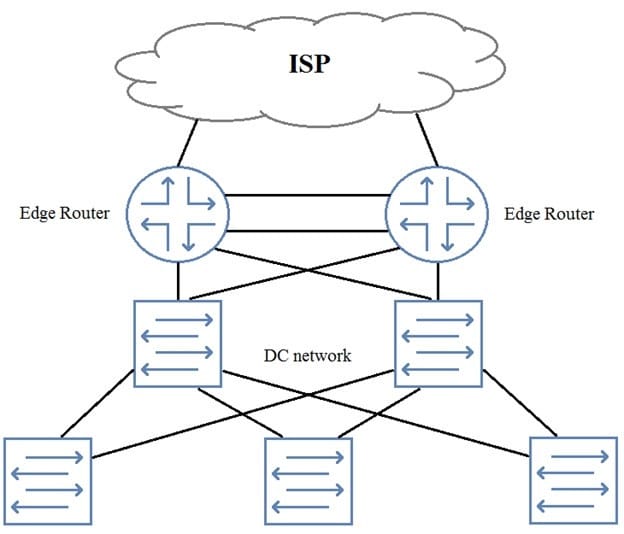
In this scenario, which design would satisfy these requirements?
A. one-arm SRX Series device using LAG
B. one-arm SRX Series chassis cluster
C. inline SRX Series chassis cluster
D. inline SPX Series device using LAG
You are designing an EBGP IP fabric for a multi-site data center. In this scenario, which two statements are true? (Choose two.)
A. Public AS numbers must be used.
B. Different AS numbers should be used on all devices.
C. The same AS number should be used on all devices across all data centers.
D. Private AS numbers can be used.
In the exhibit, VM1 is part of the same VXLAN segment as VM3.
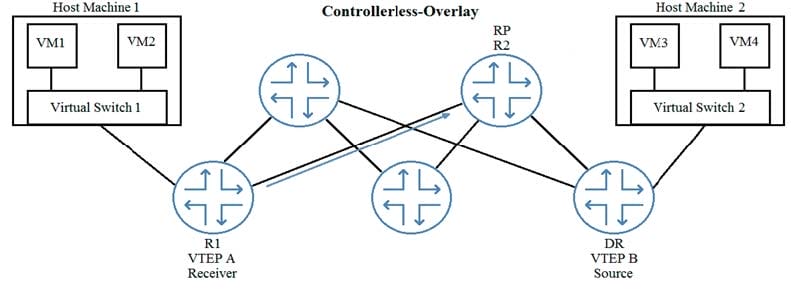
Which type of message will R1 initially send to R2 so that VM1 receives BUM traffic from VM3?
A. IGMP Join (S,G)
B. PIM Join
C. IGMP Join (*,G)
D. PIM Register message
When using EBGP as the underlay protocol for your IP fabric architecture, which two statements are true? (Choose two.)
A. Spine nodes only peer to leaf nodes.
B. Leaf nodes peer to both spine and leaf nodes.
C. Leaf nodes only peer to spine nodes.
D. Spine nodes peer to both leaf and spine nodes.
You have deployed two data centers that require a Layer 2 stretch between host1 and host2.
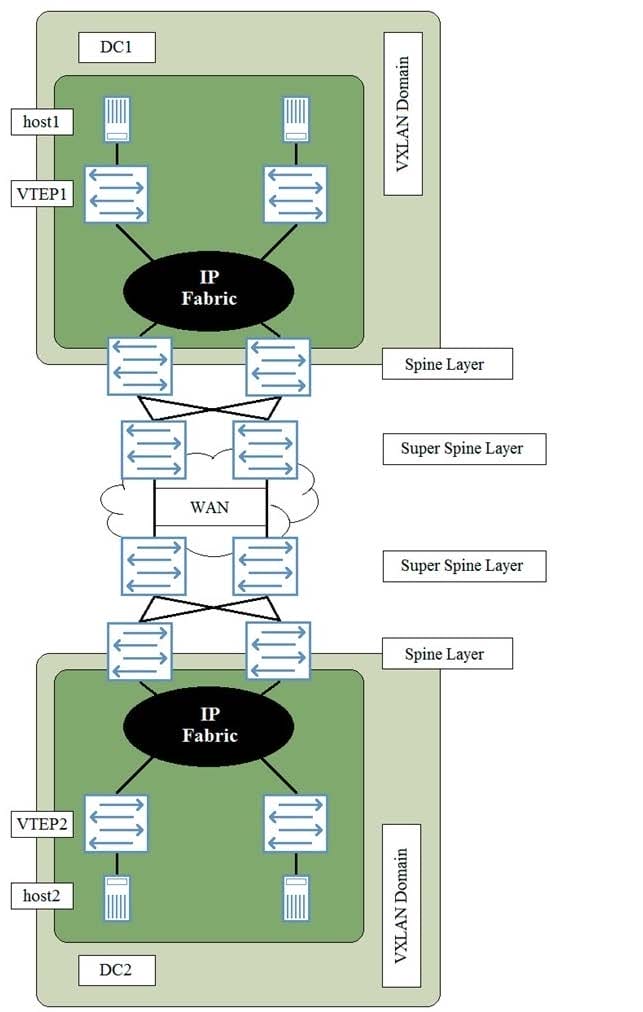
Referring to the exhibit, what does a Layer 2 stretch require?
A. a VXLAN tunnel originating on the Super Spine Layer in DC1 to the Super Spine Layer in DC2.
B. a VXLAN tunnel originating on VTEP1 to VTEP2.
C. a VXLAN tunnel originating on the Spine Layer in DC1 to the Spine Layer in DC2.
D. a VPLS WAN connection between data centers.
What are two methods used to scale an IBGP IP Fabric? (Choose two.)
A. spanning tree
B. redundant trunk groups
C. route reflection
D. confederations
You are creating a new EVPN and are asked to selectively accept certain MAC advertisement routes from your EVPN peers using VXLAN encapsulation.
Which statement is correct in this scenario?
A. You can use MAC filtering to filter out unwanted routes.
B. You can use VRF import policies and route distinguisher values to filter out unwanted routes.
C. You can use VRF import policies and community values to filter out unwanted routes.
D. You can use firewall filters to filter out unwanted routes.
You have configured MP-IBGP to support EVPN for your overlay network. However, you are not seeing the expected routes on your edge devices.
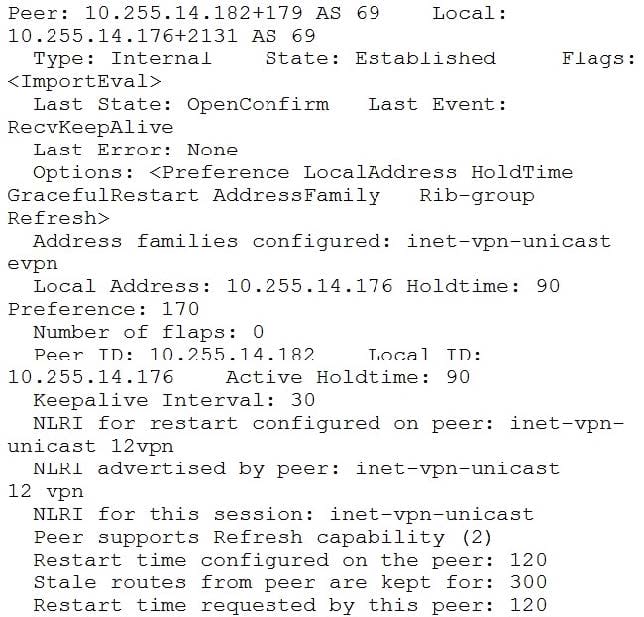
Referring to the exhibit, how would you solve this problem?
A. The family evpn signaling parameter must be configured on the remote peer.
B. Graceful restart must be disabled for this session.
C. The group types on both devices should be set to external.
D. The family 12vpn signaling must be configured on the local peer.
In the exhibit, VM1 is part of the same VXLAN segment as VM3.
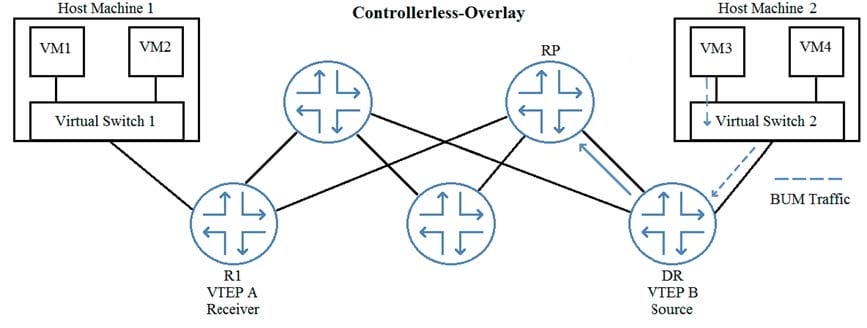
Which type of message will VTEP B initially send to the RP so that VM3 can communicate with VM1?
A. PIM join
B. PIM register message
C. IGMP Join (S,G)
D. IGMP Join (*,G)
You want to ensure high availability of the Junos devices in your data center.
In this scenario, which three features would accomplish this task? (Choose three.)
A. Virtual Router Redundancy Protocol
B. Multiple Spanning Tree Protocol
C. dual Routing Engines
D. virtual private LAN service
E. graceful Routing Engine switchover

