JN0-635 Online Practice Questions and Answers
You have configured static NAT for a webserver in your DMZ. Both internal and external users can reach the webserver using the webserver's IP address. However, only internal users can reach the webserver using the webserver's DNS name. When external users attempt to reach the webserver using the webserver's DNS name, an error message is received.
Which action would solve this problem?
A. Disable Web filtering
B. Use DNS doctoring
C. Modify the security policy
D. Use destination NAT instead of static NAT
You must troubleshoot ongoing problems with IPsec tunnels and security policy processing. Your network consists of SRX340s and SRX5600s.
In this scenario, which two statements are true? (Choose two.)
A. IPsec logs are written to the kmd log file by default
B. IKE logs are written to the messages log file by default
C. You must enable data plane logging on the SRX340 devices to generate security policy logs
D. You must enable data plane logging on the SRX5600 devices to generate security policy logs
Click the Exhibit button.
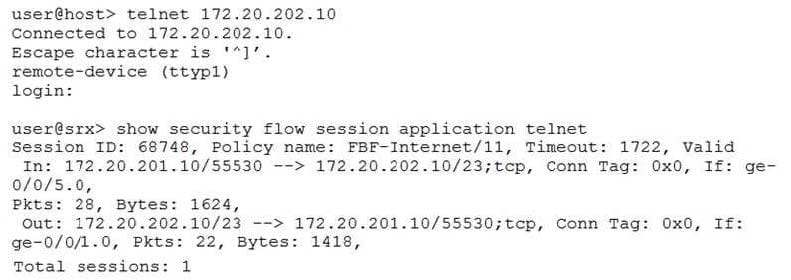
You are implementing a new branch site and want to ensure Internet traffic is sent directly to your ISP and other traffic is sent to your company headquarters. You have configured filter-based forwarding to accomplish this objective. You verify proper functionality using the outputs shown in the exhibit.
Which two statements are true in this scenario? (Choose two.)
A. The session utilizes one routing instance
B. The ge-0/0/5 and ge-0/0/1 interfaces must reside in a single security zone
C. The ge-0/0/5 and ge-0/0/1 interfaces can reside in different security zones
D. The session utilizes two routing instances
Click the Exhibit button.
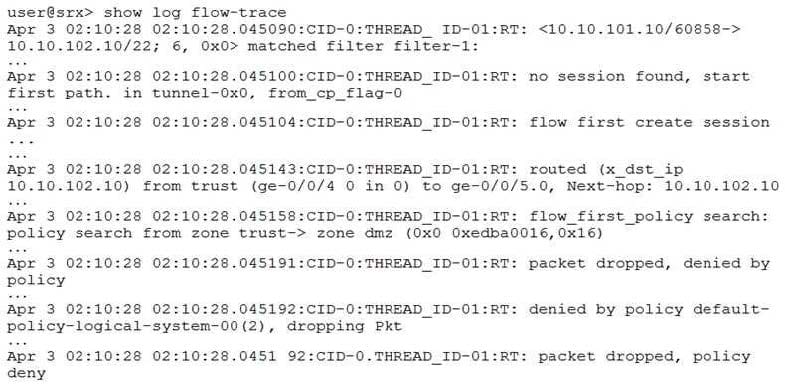
The exhibit shows a snippet of a security flow trace. A user cannot open an SSH session to a server. Which action will solve the problem?
A. Create a security policy that matches the traffic parameters
B. Edit the source NAT to correct the translated address
C. Create a route entry to direct traffic into the configured tunnel
D. Create a route to the desired server
You have a remote access VPN where the remote users are using the NCP client. The remote users can access the internal corporate resources as intended; however, traffic that is destined to all other Internet sites is going through the remote access VPN. You want to ensure that only traffic that is destined to the internal corporate resources use the remote access VPN.
Which two actions should you take to accomplish this task? (Choose two.)
A. Enable the split tunneling feature within the VPN configuration on the SRX Series device
B. Enable IKEv2 within the VPN configuration on the SRX Series device
C. Configure the necessary traffic selectors within the VPN configuration on the SRX Series device
D. Configure split tunneling on the NCP profile on the remote client
A user is unable to reach a necessary resource. You discover the path through the SRX Series device
includes several security features. The traffic is not being evaluated by any security policies.
In this scenario, which two components within the flow module would affect the traffic? (Choose two.)
A. services/ALG
B. destination NAT
C. source NAT
D. route lookup
Click the Exhibit button.

When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
A. The fxp0 IP address is not routable
B. The SRX Series device certificate does not match the JATP certificate
C. The SRX Series device does not have an IP address assigned to the interface that accesses JATP
D. A firewall is blocking HTTPS on fxp0
Click the Exhibit button.
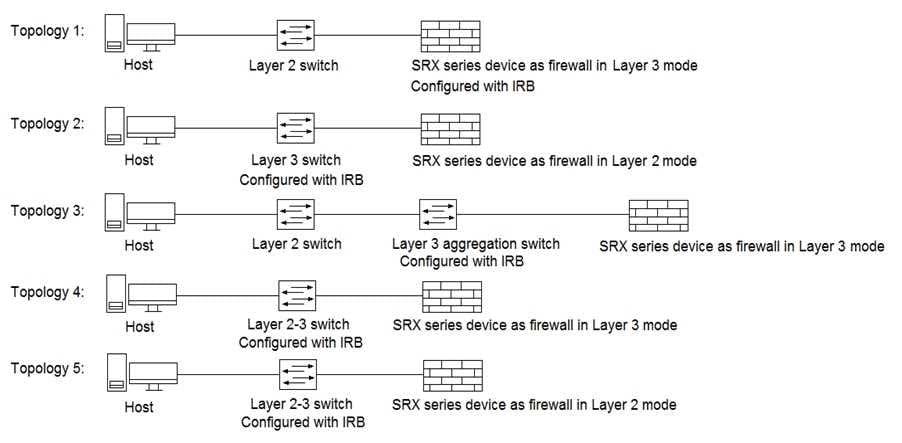
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
A. Topology 3
B. Topology 5
C. Topology 2
D. Topology 4
E. Topology 1
The monitor traffic interface command is being used to capture the packets destined to and the from the
SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
A. This feature does not capture transit traffic.
B. This feature captures ICMP traffic to and from the SRX Series device.
C. This feature is supported on high-end SRX Series devices only.
D. This feature is supported on both branch and high-end SRX Series devices.
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance. What would be a cause of this problem?
A. The collector must have a minimum of two interfaces.
B. The collector must have a minimum of three interfaces.
C. The collector must have a minimum of five interfaces.
D. The collector must have a minimum of four interfaces.

