JN0-333 Online Practice Questions and Answers
What are two supported hypervisors for hosting a vSRX? (Choose two.)
A. VMware ESXi
B. Solaris Zones
C. KVM
D. Docker
Which two statements are true about global security policies? (Choose two.)
A. Global security policies are evaluated before regular security policies.
B. Global security policies can be configured to match addresses across multiple zones.
C. Global security policies can match traffic regardless of security zones.
D. Global security policies do not support IPv6 traffic.
You want to protect your SRX Series device from the ping-of-death attack coming from the untrust security zone.
How would you accomplish this task?
A. Configure the host-inbound-traffic system-services ping except parameter in the untrust security zone.
B. Configure the application tracking parameter in the untrust security zone.
C. Configure a from-zone untrust to-zone trust security policy that blocks ICMP traffic.
D. Configure the appropriate screen and apply it to the [edit security zone security-zone untrust] hierarchy.
Which interface is used exclusively to forward Ethernet-switching traffic between two chassis cluster nodes?
A. swfab0
B. fxp0
C. fab0
D. me0
Click the Exhibit button.

The inside server must communicate with the external DNS server. The internal DNS server address is
10.100.75.75. The external DNS server address is 75.75.76.76. Traffic from the inside server to the DNS server fails.
Referring to the exhibit, what is causing the problem?
A. The security policy must match the translated destination address.
B. Source and static NAT cannot be configured at the same time.
C. The static NAT rule must use the global address book entry name for the DNS server.
D. The security policy must match the translated source and translated destination address.
Which statement is true about high availability (HA) chassis clusters for the SRX Series device?
A. Cluster nodes require an upgrade to HA compliant Routing Engines.
B. Cluster nodes must be connected through a Layer 2 switch.
C. There can be active/passive or active/active clusters.
D. HA clusters must use NAT to prevent overlapping subnets between the nodes.
Which process describes the implementation of screen options on an SRX Series device?
A. Configured screen options are only applied when traffic does not match a valid route.
B. Configured screen options are applied only to the first packet that is processed in a stateful session.
C. Configured screen options are applied to all packets that are processed by the stateful session firewall processor.
D. Configured screen options are only applied when traffic does not match a valid policy.
A session token on an SRX Series device is derived from what information? (Choose two.)
A. routing instance
B. zone
C. screen
D. MAC address
Your internal webserver uses port 8088 for inbound connections. You want to allow external HTTP traffic to connect to the webserver.
Which two actions would accomplish this task? (Choose two.)
A. Create a custom application for port 8088 and create a security policy that permits the custom-http application.
B. Remap port 80 to port 8088 in the junos-http application and create a security policy that permits the junos-http application.
C. Use destination NAT to remap incoming traffic from port 80 to port 8088.
D. Create an Application Layer Gateway to permit HTTP traffic on port 8088.
Click the Exhibit button.
You are configuring an OSPF session between two SRX Series devices. The session will not come up.
Referring to the exhibit, which configuration change will solve this problem?
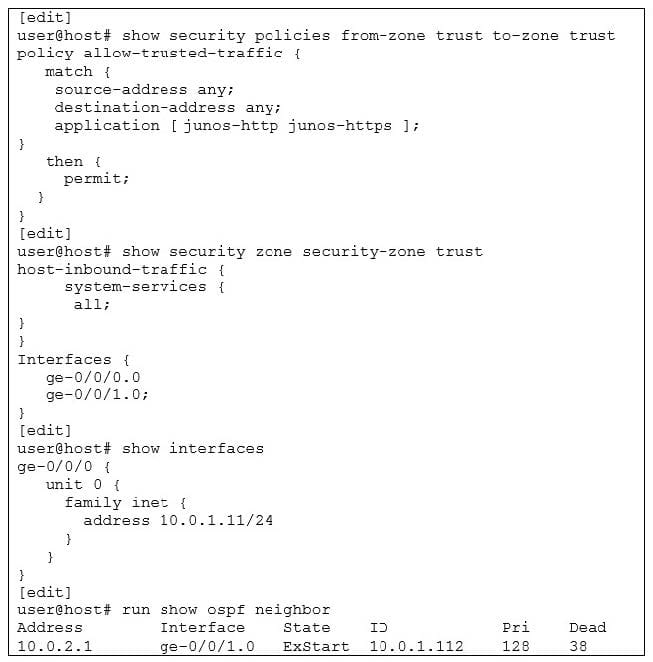
A. Configure a loopback interface and add it to the trust zone.
B. Configure the host-inbound-traffic protocols ospf parameter in the trust security zone.
C. Configure the application junos-ospf parameter in the allow-trusted-traffic security policy.
D. Configure the host-inbound-traffic system-services any-service parameter in the trust security zone.

