JN0-230 Online Practice Questions and Answers
Users should not have access to Facebook, however, a recent examination of the logs security show that
users are accessing Facebook.
Referring to the exhibit,
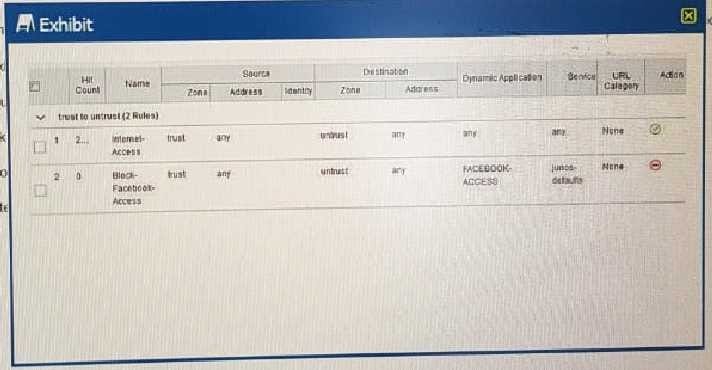
What should you do to solve this problem?
A. Change the source address for the Block-Facebook-Access rule to the prefix of the users
B. Move the Block-Facebook-Access rule before the Internet-Access rule
C. Move the Block-Facebook-Access rule from a zone policy to a global policy
D. Change the Internet-Access rule from a zone policy to a global policy
Which statement is correct about IKE?
A. IKE phase 1 is used to establish the data path
B. IKE phase 1 only support aggressive mode.
C. IKE phase 1 negotiates a secure channel between gateways.
D. IKE phase 1 establishes the tunnel between devices
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
A. With global-based policies, you do not need to specify a destination zone in the match criteria.
B. With global-based policies, you do not need to specify a source zone in the match criteria.
C. With global-based policies, you do not need to specify a destination address in the match criteria.
D. With global-based policies, you do not need to specify a source address in the match criteria.
You are concerned that unauthorized traffic is using non-standardized ports on your network. In this scenario, which type of security feature should you implement?
A. Application firewall
B. Sky ATP
C. Firewall filters
D. Zone-based policies
Which security object defines a source or destination IP address that is used for an employee Workstation?
A. Zone
B. Screen
C. Address book entry
D. scheduler
You configure and applied several global policies and some of the policies have overlapping match criteria.
A. In this scenario, how are these global policies applies?
B. The first matched policy is the only policy applied.
C. The most restrictive that matches is applied.
D. The least restrictive policy that matches is applied.
Your company has been assigned one public IP address. You want to enable internet traffic to reach multiple servers in your DMZ that are configured with private address. In this scenario, which type of NAT would be used to accomplish this tasks?
A. Static NAT
B. Destination NAT
C. Source NAT
D. NAT without PAT
Which two statements are correct about functional zones? (Choose two.)
A. A functional zone uses security policies to enforce rules for transit traffic.
B. Traffic received on the management interface in the functional zone cannot transit out other interface.
C. Functional zones separate groups of users based on their function.
D. A function is used for special purpose, such as management interface
Which Statement is correct about Sky ATP?
A. The local Sky ATP platform downloads the latest threat from managed site
B. Sky ATP can provide live threat feeds to SRX series devices
C. Sky ATP is a local hardware-based security threat analyzer that performs multiple tasks.
D. Sky ATP relies on the SRX series device to open and analyze suspect file attachments
Which two statements are correct about global security policies? (choose two)
A. Global based policies can reference the destination zone
B. Global based policies can reference the source zone
C. Global based policies must reference a dynamic application
D. Global based policies must reference the source and destination zones

