JN0-1302 Online Practice Questions and Answers
Which two statements describe SDN? (Choose two.)
A. SDN can alleviate the need for manually configuring each network device.
B. SDN moves forwarding functions to a centralized management platform.
C. SDN combines the control plane and the forwarding plane into a single fabric.
D. SDN moves compute intensive functions to a centralized controller.
Which two Layer 2 Data Center Interconnect redundancy options support active/active forwarding? (Choose two.)
A. VPLS LAG
B. point-to-point LAG
C. EVPN multihoming
D. VPLS multihoming
Click the Exhibit button.
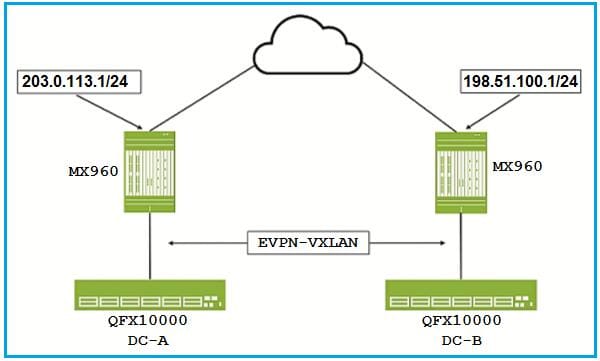
You are in discussions with the WAN team about implementing a Data Center interconnect between DC-A and DC-B, as shown in the exhibit.
What are two protocols that would support your Data Center Interconnect requirements? (Choose two.)
A. Layer 3 VPN
B. OVSDB
C. BGP
D. H-VPLS
Click the Exhibit button.
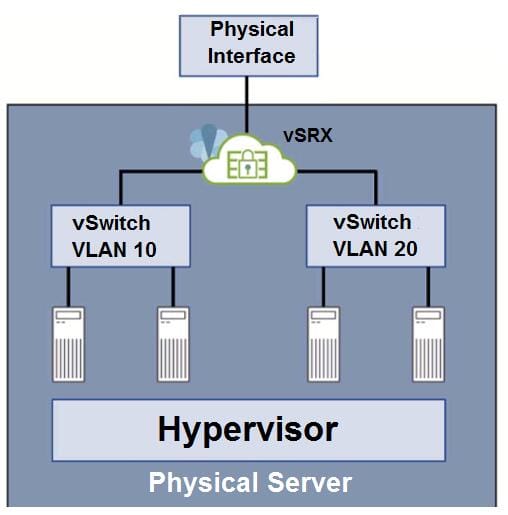
Referring to the exhibit, which two statements are true? (Choose two.)
A. The vSRX is not performing microsegmentation.
B. The vSRX is working in routed mode.
C. The vSRX is working in transparent mode.
D. The vSRX is performing microsegmentation.
When considering environmental conditions in a data center, which two statements are correct? (Choose two.)
A. The device air intake should face the cold aisle.
B. Relative humidity that is too low can cause water condensation.
C. Device exhaust fans should face the cold aisle.
D. The temperature should be measured at multiple heights.
You are designing an IP fabric underlay using IBGP with the spines serving as route reflectors. In this scenario, which BGP capability must be supported on the spines?
A. add-path
B. route-monitoring
C. rib-sharding
D. route-refresh-priority
You must design a data center (DC) connectivity solution for four data centers located in the US, Europe, Africa, and China.
Which three statements are correct in this scenario? (Choose three.)
A. VPLS can provide connectivity for four or more DC deployments.
B. LDP Layer 2 circuits learn MAC addresses in the data plane.
C. BGP Layer 2 VPNs are required due to latency requirements.
D. PE routers in an EVPN environment advertise MAC addresses using BGP.
E. EVPN can provide connectivity for four or more DC deployments.
You are asked by the data center architecture team to evaluate redundancy and management options for server racks that have two or more switches to reduce the management footprint while maintaining redundancy.
Which technology fulfills both requirements?
A. Virtual Chassis
B. ESI
C. Virtual Router Redundancy Protocol
D. MC-LAG
Contrail Networking performs which three functions? (Choose three.)
A. Configure physical network functions.
B. Deploy bare metal compute devices.
C. Perform service chain network functions.
D. Configure storage components.
E. Virtualize networks.
What are two types of data center network overlays supported by Juniper Networks? (Choose two.)
A. Generic Network Virtualization Encapsulation
B. centrally-routed bridging
C. edge-routed bridging
D. Stateless Transport Tunneling

