HPE2-W05 Online Practice Questions and Answers
While troubleshooting integration between ClearPass and IntroSpect, you notice that there are no log events for either THROUGHPUT or ERROR in the ClearPass log source on the IntroSpect Analyzer. You are planning your troubleshooting actions.
Is this something you should check? (Check the authentication service being used in ClearPass for the Login - Logout enforcement policy.)
A. Yes
B. No
While looking at the conversation page you notice some strange network behavior, such as DNS requests coming inbound from external DNS servers. Could this be the reason why? (You have your network tap positioned wrong, and you are just getting outside data.)
A. Yes
B. No
Refer to the exhibit.
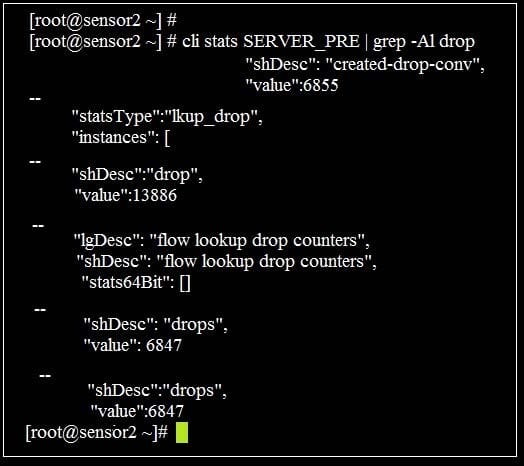
You are monitoring a new virtual packet processor with a network tap. You run the command "cli stats SERVER_PRE | gre-a1 drop" and then return an hour later and run the same command, but notice there is a significant increase in the number dropped packets.
Could this be a reason for the increase? (The Packet Processor may not be allocated the proper number of memory allocated on the VM server for the size of the TAP.)
A. Yes
B. No
You deploy IntroSpect Analyzer in your existing network. You want to monitor email for suspect malware activity. Would this action be supported by IntroSpect? (Deploy a supported DNP like Proofpoint Email Protection, and integrate with The IntroSpect Analyzer.)
A. Yes
B. No
While reviving the logs at a customer site you notice that one particular device is accessing multiple
servers in the environment, using a number of different user accounts. When you question the IT admin,
they tell you that the computer is a JumpBox and running software used to monitor all of the servers in the
environment.
Would this be a logical next step? (As a next step, you should audit all of the accounts that are being used
on the JumpBox to determine if the JumpBox is being accessed by unauthorized accounts.)
A. Yes
B. No
Refer to the exhibit.
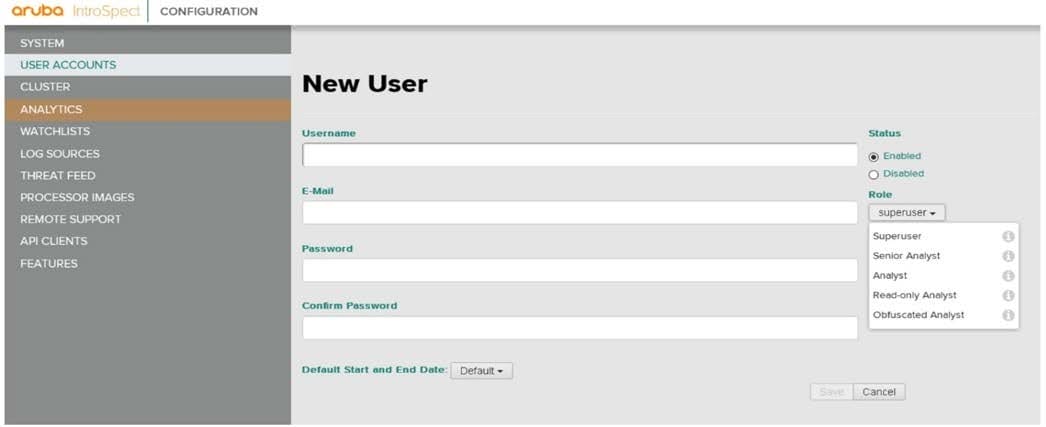
Would this be a correct option when configuring a user account for a ClearPass to use to communicate with IntroSpect? (The username and email address must match.)
A. Yes
B. No
Refer to the exhibit.
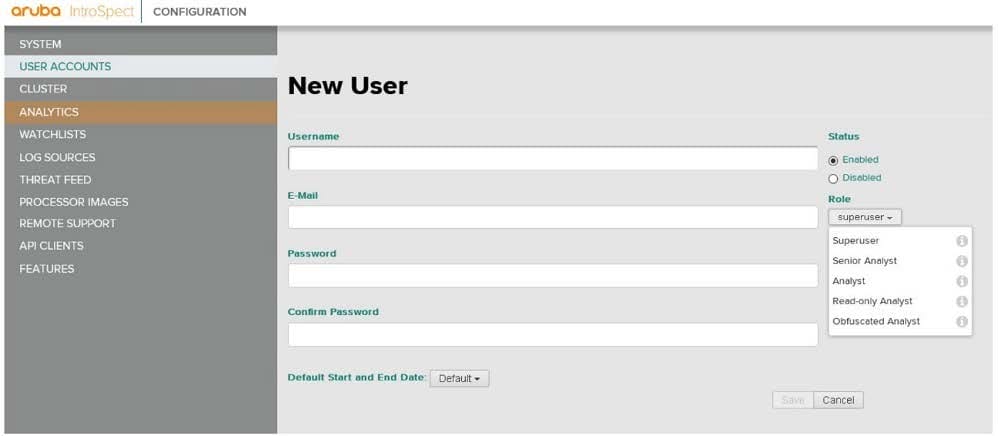
Would this be a correct option when configuring a user account for a ClearPass to use to communicate with IntroSpect? (The username must be the host name of the ClearPass server, and the email address needs to be the username on the ClearPass server.)
A. Yes
B. No
You are administering an IntroSpect Installation. While monitoring the load on the IntroSpect Packet Processors, you think that one Packet Processor is overloaded. Is this a correct statement about the possible overload? (As a general rule, the data rate should be below 9000 event/sec.)
A. Yes B. No
A network administrator is looking for an option to set the maximum data retention period to 180 days in the IntroSpect Analyzer. Is this a correct statement about data retention in IntroSpect? (The default data retention period is set at 30 days, and this cannot be changed.)
A. Yes
B. No
Refer to the exhibit.
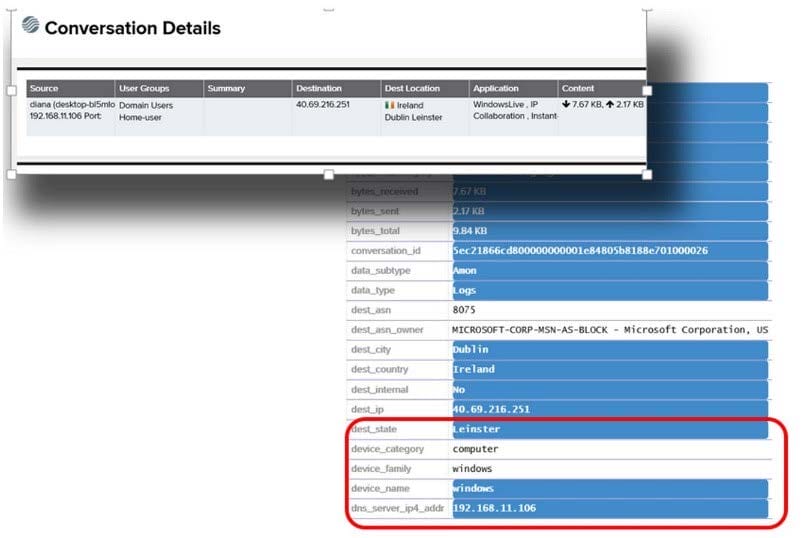
You are a security analyst for a company that has deployed an Aruba infrastructure, such as Mobility Controllers, ClearPass, and Airwave. Recently they have deployed Aruba IntroSpect for security analytics. You are looking at the conversation details of an entity. Is this statement correct about the details highlighted? (These details came from the ClearPass server and it has been integrated as a context server in the IntroSpect.)
A. Yes
B. No

