H12-721 Online Practice Questions and Answers
Which of the following is a drawback of an L2TP VPN?
A. It cannot be routed in two layers
B. You must use L2TP Over IPsec
C. No authentication
D. No encryption
In site to Site IPsec VPN negotiation process, what should be the order of checks? 1 network connectivity problems
2.
Establish conditions and configuration View IKE Phase 1 Safety Alliance
3.
Establish conditions and related configuration view IKE phase 2 security alliance 4 Check whether the ends of the Security ACL mirror each other
A. 1 -> 4 -> 2 -> 3
B. 4 -> 2 -> 3 -> 1
C. 2 -> 3 -> 1 -> 4
D. 4 -> 1 -> 2 -> 3
Which statement about IP-link features are correct? (Choose three answers)
A. IP-link is a link connectivity detection function
B. ARP detection methods only support direct link
C. Firewalls will send ICMP or ARP packets to determine if the destination address is reachable to the destination address of a probe
D. With IP-link and associated VGMP, when the IP-Link status becomes down, VGMP lowers the default priority management group by 3.
Which of the following description about SMURF attacks is correct?
A. Attacker sends ping requests to a subnet (broadcast), requesting that devices on that subnet send ping replies to a target system. Once the host or network is detected, it is then brought down.
B. Attacker sends SYN packets with source and destination addresses for the IP address where the attacker is. A SYN-ACK message is sent to their own address, so is the presence of an attacker hosts a large number of air connections.
C. An attacker can target where to send a UDP packet in the network. The source address of the packet is being attacked. Host address, destination address are in the subnet broadcast address where the attack host the subnet network address using destination port number 7 or 19.
D. An attacker using a network or host receives an ICMP unreachable packets, the packets destined for the follow-up of this destination address directly considered unreachable, thereby cutting off the connection to the host destination.
Which of the following are scanned snooping attack??
A. SIP Flood attacks
B. HTTP Flood Attack
C. IP address scanning attack
D. ICMP redirect packet attack
IPsec tunneling is used as a backup connection as shown below: Which of the following statements are true about the tunnel interface? (Choose two answers)
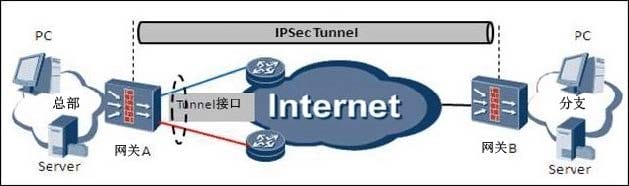
A. IPsec security policy should be applied to the tunnel interface
B. Protocol for the Tunnel Interface must be GRE.
C. Tunnel interface needs to be configured on the IP address and the IP address of the gateway. The external network IP address of the outgoing interface must be in the same network segment.
D. Tunnel interfaces can be added to any security zone, provided they have the appropriate inter-domain security policies.
The three abnormal flow cleaning solution include? (Choose three answers)
A. Cleaning Center
B. Testing Center
C. Management Center
D. Acquisition Center
In Defense gate FIN / RST Flood attack method, conversation is checked. The workflow is that when the door FIN / RST packet rate exceeds the threshold; it discards packets, and then starts the conversation check.
A. TRUE
B. FALSE
USG_A and USG_B are in a hot standby configuration as shown below. The current session table show 1,500+ sessions, and when a switchover occurs there is a period of traffic interruption. You want to ensure a seamless failover.
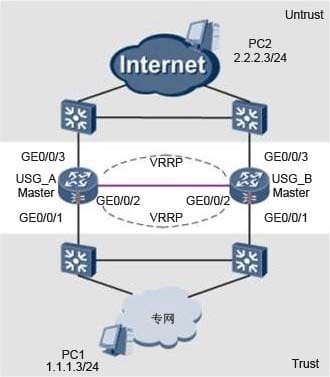
Which of the following are valid options that could be done to ensure a seamless failover?
A. Run the "hrp preempt delay 64" command to make the preemption delay time longer.
B. Check the connectivity between heartbeats.
C. Configure session fast backup.
D. Use the "no Hrp enable" command.
Refer to the following NIP firewall intrusion detection actions: 1 records the invasion process, alarm logging
2. NIP attack detection 3 reconfigure the firewall 4 Termination invasion Which of the following is the correct sequence of events?
A. 1 -> 2 -> 3 -> 4
B. 2 -> 1 -> 3 -> 4
C. 3 -> 1 -> 2 -> 4
D. 1 -> 2 -> 4 -> 3

