GCFR Online Practice Questions and Answers
A cloud administrator needs to determine which user account allowed SSH Inbound from the internet on an Azure Network security group. Which type of log does the administrator need to examine?
A. Tenant
B. Subscription
C. Operating System
D. Resource
What is shown in the screenshot?
A. Google threat types
B. Windows event channels
C. Mitre ATTandCK tactics
D. CIS critical controls
What can bedetermine about the AVVS Access Key below?
AKIAVNKBKCM4I3VNZIS3
A. The key belongs to a user account
B. The key will only work internally
C. It is a service STS token
D. It is only in use for a single session
Sensitive company data is found leaked on the internet, and the security team didn't get any alert and is unsure of how the breach occurred.
Which logs would be a preferable starting point for an investigation?
A. Identity and Access Management
B. Application
C. Resource Management
D. Endpoint
Communication between the VPN client and Azure VNet1via VPN Tunnel #1 is using which of the following connections?
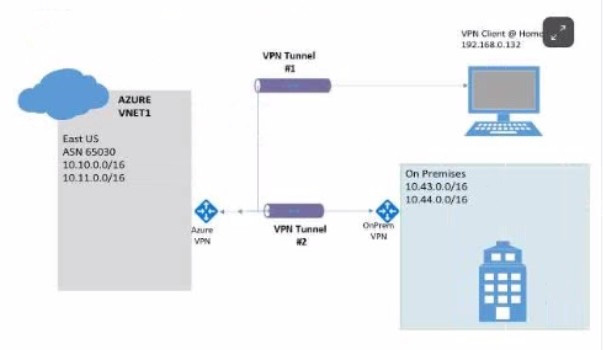
A. Point-to-site VPN
B. IPSec
AWS VPC Flow logs are enabled. What do these logs capture?
A. TCP Checksums
B. Packet Metadata
C. TLS Handshakes
D. Payload Bytes
What can be inferred about the ARN below?
arn:aws:!am::457787814323:user/giac
A. giac's is a user In the AWS account 457787814323
B. giac's access Is testf kted to resources owned by AWS tenant 457787814323
C. giac's Is limited to roles defined under a single AWS organization
D. giac's user's access key 10 is 457787814323
In Azure, which of the following describes a "Contributor"?
A. A collection of permissions such as read, write, and delete
B. A designation on a PKI certificate
C. A specification of who can access a resource group
D. An object representing an entity
A company using PaaS to host and develop their software application is experiencing a DOS attack. What challenge will a DFIR analyst experience when investigating this attack?
A. Restricted access to their application logs
B. Resource scaling will affect access to logs
C. Network logs are unavailable for review
D. Network monitoring disabled by the company
Which of the following Windows agents would need to be configured on an Azure VM for an investigator to query Its operating system logs sent to Azure Storage?
A. Azure Monitor
B. Diagnostic Extension
C. Dependency
D. Log Analytics

