FCNSP.V5 Online Practice Questions and Answers
Which of the following statements are correct regarding Application Control?
A. Application Control is based on the IPS engine.
B. Application Control is based on the AV engine.
C. Application Control can be applied to SSL encrypted traffic.
D. Application Control cannot be applied to SSL encrypted traffic.
With FSSO, a domain user could authenticate either against the domain controller running the Collector Agent and Domain Controller Agent, or a domain controller running only the Domain Controller Agent.
If you attempt to authenticate with the Secondary Domain Controller running only the Domain Controller Agent, which of the following statements are correct? (Select all that apply.)
A. The login event is sent to the Collector Agent.
B. The FortiGate unit receives the user information from the Domain Controller Agent of the Secondary Controller.
C. The Collector Agent performs the DNS lookup for the authenticated client's IP address.
D. The user cannot be authenticated with the FortiGate device in this manner because each Domain Controller Agent requires a dedicated Collector Agent.
In the case of TCP traffic, which of the following correctly describes the routing table lookups performed by a FortiGate unit when searching for a suitable gateway?
A. A look-up is done only when the first packet coming from the client (SYN) arrives.
B. A look-up is done when the first packet coming from the client (SYN) arrives, and a second is performed when the first packet coming from the server (SYNC/ACK) arrives.
C. A look-up is done only during the TCP 3-way handshake (SYNC, SYNC/ACK, ACK).
D. A look-up is always done each time a packet arrives, from either the server or the client side.
In Transparent Mode, forward-domain is an attribute of ______________.
A. an interface
B. a firewall policy
C. a static route
D. a virtual domain
An administrator is examining the attack logs and notices the following entry:
device_id=FG100A3907508962 log_id=18432 subtype=anomaly type=ips timestamp=1270017358 pri=alert itime=1270017893 severity=critical src=192.168.1.52 dst=64.64.64.64 src_int=internal serial=0 status=clear_session proto=6 service=http vd=root count=1 src_port=35094 dst_port=80 attack_id=100663402 sensor=protect-servers ref=http://www.fortinet.com/ids/VID100663402 msg="anomaly: tcp_src_session, 2 > threshold 1" policyid=0 carrier_ep=N/A profile=N/A dst_int=N/A user=N/A group=N/A
Based solely upon this log message, which of the following statements is correct?
A. This attack was blocked by the HTTP protocol decoder.
B. This attack was caught by the DoS sensor "protect-servers".
C. This attack was launched against the FortiGate unit itself rather than a host behind the FortiGate unit.
D. The number of concurrent connections to destination IP address 64.64.64.64 has exceeded the configured threshold.
Which of the following statements is correct regarding the FortiGuard Services Web Filtering Override configuration as illustrated in the exhibit?
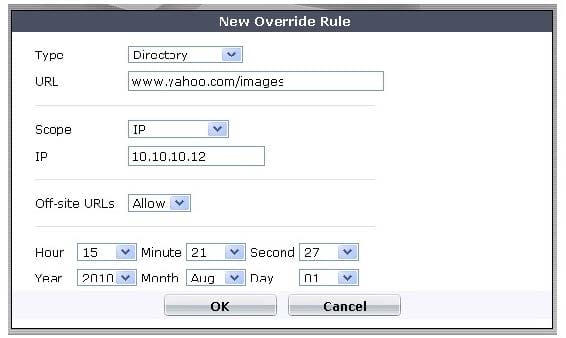
A. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/ .
B. A client with an IP of address 10.10.10.12 is allowed access to any subdirectory that is part of the www.yahoo.com web site.
C. A client with an IP address of 10.10.10.12 is allowed access to the www.yahoo.com/images/ web site and any of its offsite URLs.
D. A client with an IP address of 10.10.10.12 is allowed access to any URL under the www.yahoo.com web site, including any subdirectory URLs, until August 7, 2009.
E. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/ until August 7, 2009.
In order to load-share traffic using multiple static routes, the routes must be configured with ...
A. the same distance and same priority.
B. the same distance and the same weight.
C. the same distance but each of them must be assigned a unique priority.
D. a distance equal to its desired weight for ECMP but all must have the same priority.
In the Tunnel Mode widget of the web portal, the administrator has configured an IP Pool and enabled split tunneling.
Which of the following statements is true about the IP address used by the SSL VPN client?
A. The IP pool specified in the SSL-VPN Tunnel Mode Widget Options will override the IP address range defined in the SSL-VPN Settings.
B. Because split tunneling is enabled, no IP address needs to be assigned for the SSL VPN tunnel to be established.
C. The IP address range specified in SSL-VPN Settings will override the IP address range in the SSL-VPN Tunnel Mode Widget Options.
Which of the following Session TTL values will take precedence?
A. Session TTL specified at the system level for that port number
B. Session TTL specified in the matching firewall policy
C. Session TTL dictated by the application control list associated with the matching firewall policy
D. The default session TTL specified at the system level
Which of the following methods does the FortiGate unit use to determine the availability of a web cache using Web Cache Communication Protocol (WCCP)?
A. The FortiGate unit receives periodic "Here I am" messages from the web cache.
B. The FortiGate unit polls all globally-defined web cache servers at a regular intervals.
C. The FortiGate using uses the health check monitor to verify the availability of a web cache server.
D. The web cache sends an "I see you" message which is captured by the FortiGate unit.

