EPM-DEF Online Practice Questions and Answers
What are valid policy options for JIT and elevation policies?
A. Grant temporary access for all users, Policy name, Restart administrative processes in admin approval mode, Collect audit information
B. Grant temporary access for, Policy name, Terminate administrative processes when the policy expires, Collect audit information
C. Grant administrative access, Policy name, Log off to apply policy, Collect policy violation information
D. Terminate administrative services, Grant policy access for, Policy name, Collect audit reports
What can you manage by using User Policies?
A. Just-In-Time endpoint access and elevation, access to removable drives, and Services access.
B. Access to Windows Services only.
C. Filesystem and registry access, access to removable drives, and Services access.
D. Just-In-Time endpoint access and elevation, access to removable drives, filesystem and registry access, Services access, and User account control monitoring.
CyberArk's Privilege Threat Protection policies are available for which Operating Systems? (Choose two.)
A. Windows Workstations
B. Windows Servers
C. MacOS
D. Linux
Which user or group will not be removed as part of CyberArk EPM's Remove Local Administrators feature?
A. Built-in Local Administrator
B. Domain Users
C. Admin Users
D. Power Users
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are CyberArk recommendations. (Choose two.)
A. Add any pre-existing security application to the Files to Be Ignored Always.
B. Add EPM agent to the other security tools exclusions.
C. EPM agent should never be run with any other security tools.
D. Create new advanced policies for each security tool.
When working with credential rotation at the EPM level, what is the minimum time period that can be set between connections?
A. 1 hour
B. 5 hours
C. 24 hours
D. 72 hours
When blocking applications, what is the recommended practice regarding the end-user UI?
A. Show a block prompt for blocked applications.
B. Show no prompts for blocked applications.
C. Hide the CyberArk EPM Agent icon in the system tray.
D. Enable the Default Deny policy.
Select the default threat intelligence source that requires additional licensing.
A. VirusTotal
B. Palo Alto WildFire
C. CyberArk Application Risk Analysis Service
D. NSRL
Where would an EPM admin configure an application policy that depends on a script returning true for an end user's machine being connected to an open (no password protection) Wi-Fi?
A. Advanced Policy - Application Control - Check Wi-Fi security
B. Advanced Policy - Options: Conditional enforcement - Apply Policy according to Script execution result
C. Default policies - Check if network access is secure
D. Advanced Policy - Access - Specify permissions to be set for Wi-Fi network security
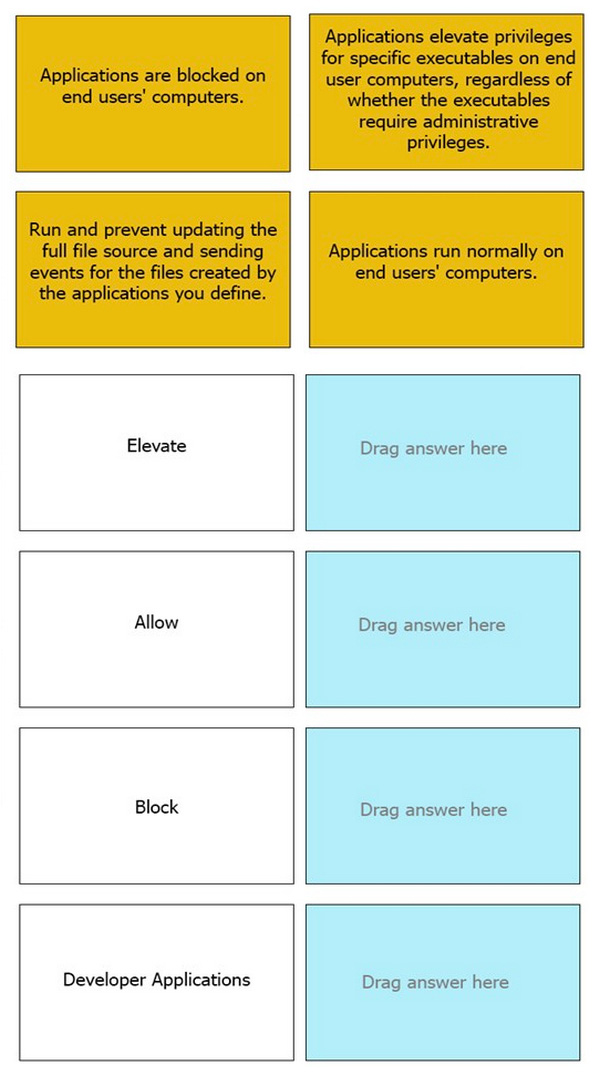
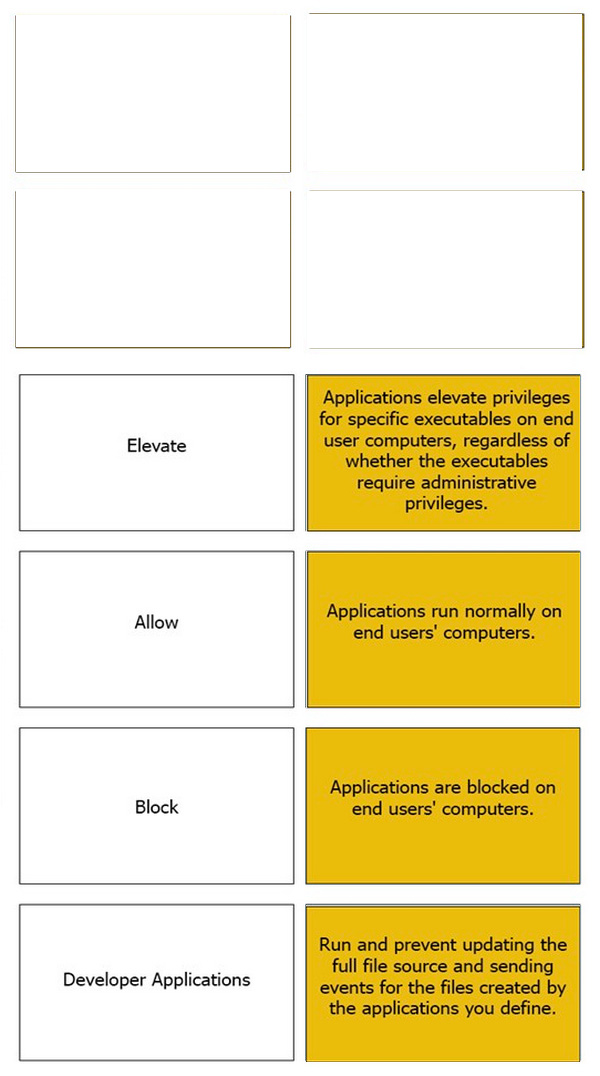
DRAG DROP
Match the Application Groups policy to their correct description.
Select and Place: