ECSAV10 Online Practice Questions and Answers
Sandra, a wireless network auditor, discovered her client is using WEP. To prove the point that the WEP
encryption is very weak, she wants to decrypt some WEP packets. She successfully captured the WEP
data packets, but could not reach the content as the data is encrypted.
Which of the following will help Sandra decrypt the data packets without knowing the key?
A. Fragmentation Attack
B. Chopchop Attack
C. ARP Poisoning Attack
D. Packet injection Attack
Tecty Motors Pvt. Ltd. has recently deployed RFID technology in the vehicles which allows the car owner to unlock the car with the exchange of a valid RFID signal between a reader and a tag. Jamie, on the other hand, is a hacker who decided to exploit this technology with the aim of stealing the target vehicle. To perform this attack on the target vehicle, he first used an automated tool to intercept the signals between the reader and the tag to capture a valid RFID signal and then later used the same signal to unlock and steal the victim's car. Which of the following RFID attacks Jamie has performed in the above scenario?
A. RFID cloning
B. Replay attack
C. DoS attack
D. Power analysis attack
The Rhythm Networks Pvt Ltd firm is a group of ethical hackers. Rhythm Networks was asked by their client Zombie to identify how the attacker penetrated their firewall. Rhythm discovered the attacker modified the addressing information of the IP packet header and the source address bits field to bypass the firewall. What type of firewall bypassing technique was used by the attacker?
A. Source routing
B. Proxy Server
C. HTTP Tunneling
D. Anonymous Website Surfing Sites
ABC Technologies, a large financial company, hired a penetration tester to do physical penetration testing.
On the first day of his assignment, the penetration tester goes to the company posing as a repairman and
starts checking trash bins to collect the sensitive information.
What is the penetration tester trying to do?
A. Trying to attempt social Engineering using phishing
B. Trying to attempt social engineering by shoulder surfing
C. Trying to attempt social engineering by eavesdropping
D. Trying to attempt social engineering by dumpster diving
Jeffry, a penetration tester in Repotes Solutions Pvt. Ltd., is facing a problem in testing the firewall. By consulting other penetration testers and considering other penetration testing approaches, he was able to take critical decisions on how to test the firewall; he was finally successful in testing the firewall for vulnerabilities. In which of the following sections of penetration testing report will Jeffry mention the above situation?
A. Timeline
B. Evaluation purpose
C. Assumptions
D. System description
Which of the following acts related to information security in the US establish that the management of an organization is responsible for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
A. USA Patriot Act 2001
B. Sarbanes-Oxley 2002
C. Gramm-Leach-Bliley Act (GLBA)
D. California SB 1386
Which of the following statements is true about the LM hash?
A. Disabled in Windows Vista and 7 OSs
B. Separated into two 8-character strings
C. Letters are converted to the lowercase
D. Padded with NULL to 16 characters
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
A. Phishing
B. Spoofing
C. Tapping
D. Vishing
Besides the policy implications of chat rooms, Internet Relay Chat (IRC) is frequented by attackers and used as a command and control mechanism. IRC normally uses which one of the following TCP ports?
A. 6566 TCP port
B. 6771 TCP port
C. 6667 TCP port
D. 6257 TCP port
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools. The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating wireless devices. Which of the following attacks can be detected with the help of wireless intrusion detection system (WIDS)?
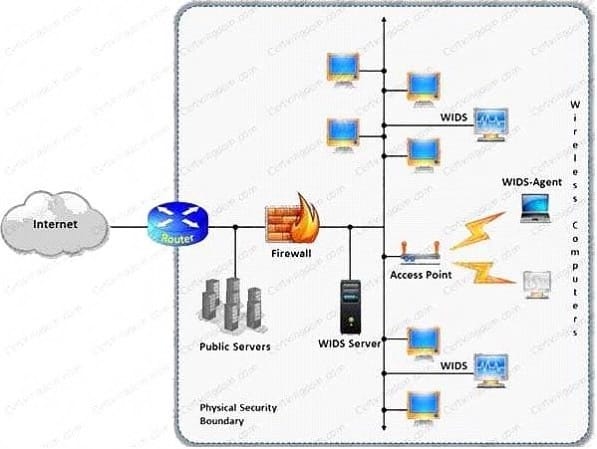
A. Social engineering
B. SQL injection
C. Parameter tampering
D. Man-in-the-middle attack

