E20-329 Online Practice Questions and Answers
An EMC NetWorker customer is considering using an EMC Disk Library as a target as shown in the exhibit. Two storage nodes need to access the same pool of virtual tapes. In addition, the customer wants to load balance the usage of virtual tape drives across the available connections. Based on EMC best practices, which satisfies these requirements?
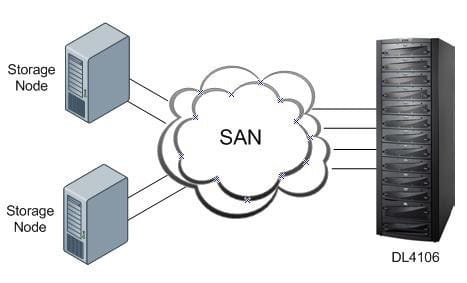
A. Assign each host initiator port a different set of virtual tape drives from the same virtual library
B. Configure each host initiator with a different virtual tape library, pointing to a common pool of virtual tapes
C. Assign all virtual drives to all host initiator ports and use Power Path
D. configure all virtual tape drives on all initiators and enable Active Engine Failover
A customer is planning a new database rollout using Oracle and wants to perform online backups. Initial tests with NetWorker have shown that the backups cannot be completed within the backup window of 6 hours.
You have analyzed your backup environment and there are adequate resources to meet this stringent backup window. What is one of the first things to check in NetWorker or RMAN to increase performance without adding cost and complexity?
A. Adjust the maximum number of files in a backup set to be less than the number of open files
B. Adjust RMAN channels to have multiple streams per tape device
C. Adjust RMAN multiplexing to be less than the tape multiplexing setting
D. Adjust RMAN multiplexing to be equal to or greater than the tape multiplexing setting
A single-engine EMC Disk Library (EDL) is being proposed with Remote Copy functionality replicate data
to a remote EDL. One of the EDLs will have four network connections while the other one will have two
network connections.
How many ports will be used in each EDL during a replication session?
A. 1
B. 2
C. 3
D. 4
A new EMC Avamar customer wants advice on setting up their groups and schedules. The customer has a mixed environment and is migrating from a traditional tape backup solution with a mixed retention policy.
Which follows EMC best practices for setting up groups and policies?
A. Minimize the number of groups, combine different OSs in datasets, and implement advanced retention.
B. Group clients by OS, make unique datasets for each OS, and create unique retention policies for Monthly, Daily, Weekly, and Yearly.
C. Enable the default group and use the group for all policies. Every client is added to this group upon activation.
D. Create a unique group for each dataset, schedule, and retention.
An EMC Data Domain customer has ordered three expansion shelves to increase the active tier storage capacity for backup. After successfully installing the new expansion shelves, the Data Domain GUI is partially showing the new extra capacity.
What is the reason for this issue?
A. One Active tier and one Archive tier licenses are needed
B. Data Domain needs to be reconfigured to recognize the new capacity
C. Only one Expansion Storage license was not installed
D. Only one Shelf Capacity license was installed
You are performing a Data Deduplication Assessment for a customer. Which tool is used to test and tune network connections?
A. iperf
B. DDA:A
C. DDA:B
D. DPA
While designing an EMC Data Domain solution for a customer, you want to determine the amount of storage capacity needed. You have discovered the following information:
2 TB full backup @ 5x compression 10% daily data change rate 4 incremental/week @ 10x compression 1x full per week @ 25x compression Retention period = 4 weeks with no data growth
What is the burn rate (in GB)?
A. 150
B. 160
C. 175
D. 200
A customer with 20,000 desktop/laptop (DT/LT) clients has expanded their custom set of includes/excludes for their Avamar DT/LT solution to cover all non- business files in their environment. Upon implementation of these datasets, they find that backups are not completing in the expected time frame. They need advice on managing their backups to fit the backup window.
Based on best practices, what should be recommended?
A. Minimize the number of includes/excludes and utilize the #USERDOCS# flag
B. Increase the hash cache on all clients for faster processing of includes/excludes
C. Move clients with the most includes/excludes into their own dataset and run this group first
D. Move the includes/excludes to an Avamar flag file on each client for faster processing
Scenario
A customer with a fully virtualized environment has four ESX 4.1 servers in a cluster with a SAN solution for storage. Each ESX server is hosting 40 virtual machines and all virtual machines have the same local disk configurations:
Disk1 = 50 GB Disk2 = 100 GB Disk3 = 256 GB In addition, the environment includes a NAS filer. The average time to fully backup all virtual machines on one ESX server using EMC DD Boost is three hours.
The customer is interested in implementing an EMC NetWorker solution with Data Domain as a backup device. The backup server, storage nodes, and proxies are SAN-attached.
Refer to Scenario .
Using a VADP proxy, EMC NetWorker is backing up 12 virtual machines concurrently in SAN transport mode. What is the total recommended RAM needed on the proxy?
A. 6 GB
B. 8 GB
C. 10 GB
D. 12 GB
A backup administrator has added a large database server with a low change rate to their Avamar server as a new backup client. The database server is located remotely and the network connection is not consistent. The server backup continuously runs into overtime and fails due to network issues. As a result, the initial backup has not completed. The backup administrator asks you for advice on how to ensure successful backups.
What should you tell the backup administrator?
A. Disable overtime for the client
B. Continue from partial backups
C. Perform incremental backups
D. Copy cache files from a similar database server

