E05-001 Online Practice Questions and Answers
What is an accurate statement about the Network File System (NFS) protocol?
A. Provides a set of remote procedure calls to access a remote file system
B. Uses the server message block protocol to provide file locking capability
C. Translates block I/O requests from a file system into object-level requests
D. Automatically scales the file systems on clients as the workload increases
Which EMC product provides a software-defined storage platform to create a compute-based storage area network?
A. ScaleIO
B. XtremIO
C. Isilon
D. Atmos
What accurately describes the flow control mechanism in an FC SAN?
A. Both transmitting and receiving ports agree on the number of buffers available during port login
B. Negotiation occurs between an E_Port and an F_Port, and between two N_Ports
C. Credit value is incremented when a frame is transmitted and decremented upon receiving a response
D. Receiver Ready (R_RDY) is sent from the receiving port if available credits reach zero
How does an iSCSI initiator discover its targets?
A. Initiator sends a query to an iSNS server for a list of available targets
B. Initiator receives the iSCSI names of its targets from the primary DNS server
C. Initiator uses the data center bridging exchange protocol for the discovery
D. Initiator sends SCSI commands and the target responds by sending its name
Which LUN expansion technique provides both capacity expansion and performance improvement?
A. Striped metaLUN
B. Partitioned metaLUN
C. Virtual metaLUN
D. Concatenated metaLUN
Which lossless Ethernet functionality helps Converged Enhanced Ethernet (CEE) devices to convey and configure their features with the other CEE devices in the network?
A. Data center bridging exchange protocol
B. Enhanced transmission selection
C. Priority-based flow control
D. Congestion notification
Which type of LUN provides full control for precise data placement and allows an administrator to create LUNs on different RAID sets if there is workload contention?
A. Traditional
B. Thin
C. Journal
D. Bitmap
The exhibit illustrates a software-defined storage environment. What do the labels "X" and "Y" represent in the exhibit?
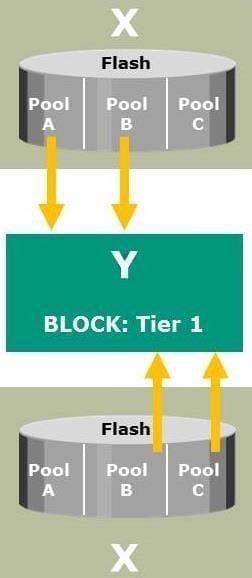
A. X is a virtual storage system and Y is a virtual storage pool
B. X is a virtual storage pool and Y is a virtual storage system
C. X is a physical storage pool and Y is a virtual storage system
D. X is a virtual storage pool and Y is a physical storage system
What enables an administrator to create device groups in an IP-SAN for restricting device communications to a group?
A. iSNS discovery domain
B. NIC teaming
C. Demilitarized zone
D. Security identifier
What is a characteristic of an FC-AL implementation?
A. Reserves one address for connecting an FC-SW port
B. Supports connectivity up to 15 million nodes
C. Devices can be added and removed dynamically without any impact
D. Requires at least one connectivity device

