DES-2T13 Online Practice Questions and Answers
DRAG DROP
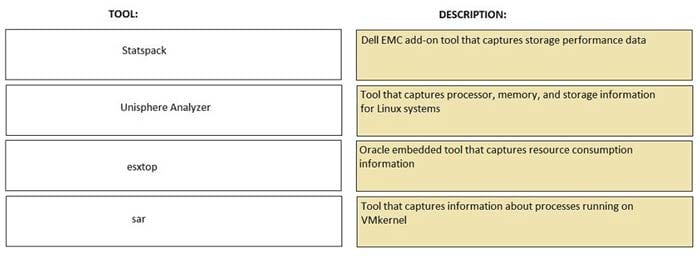
As part of the planning process, a cloud architect may use tools to gather data from customer systems. Match each tool with its associated description.
Select and Place:
DRAG DROP
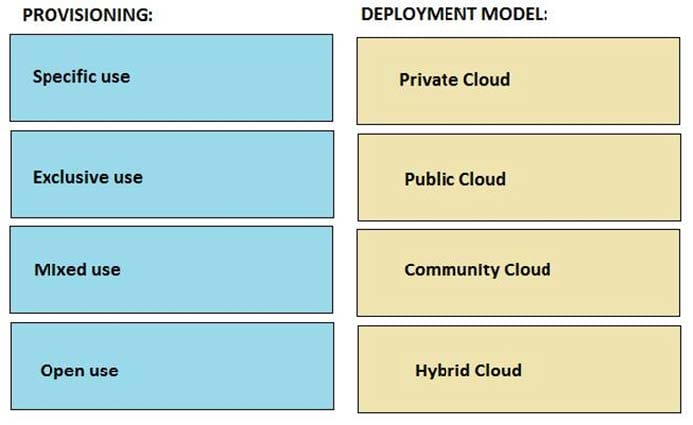
Match each cloud deployment model with what it is provisioned for:
Select and Place:
As a cloud architect, you are designing a CI solution to ensure that you isolate specific workloads for security. What should you design for?
A. High Availability
B. Fault Tolerance
C. Multi-tenancy
D. Redundancy
During an assessment for an organization's cloud design, a cloud architect discovers that developers will be creating applications for tenants. The applications will self-scale based on an internal trigger. The architect has included CMP components in the design that will support this requirement. What else should the cloud architect consider to meet this requirement?
A. CMP account with elevated privileges exists that can be shared with developers
B. Mechanisms exist for changing the type of consumer resources automatically
C. Mechanisms exist for re-installing CMP components for scaling
D. Sufficient consumer resources exist to support the application elasticity
A cloud architect is tasked with designing a backup using the Remote with Cloud Gateway Deployment Model. What is a design consideration?
A. Replication settings should be driven by organizational requirements around RPO
B. Backup servers are required to communicate with cloud storage interfaces
C. Larger initial backup sets may take long times to complete delivery
D. Gateways must contain backup software to offload backup server tasks
What is the key factor used in Business Value Analysis?
A. CAGR
B. TCO
C. CAPEX
D. NPV
SPECIAL INSTRUCTIONS REMINDER
The remaining questions are associated with two cases. Each case has an introductory, descriptive passage (case text) that describes background information and requirements for a specific cloud based design. And each case has a set of
six related, randomized questions. You will need to read the case text in order to answer the related questions correctly.
Given that there are two cases with six scored questions each, the total number of case-based scored questions is 12.
When you display each questions you can easily review the related case text in a pop-up window by clicking on the "Case" icon (shown below)
Case 4
Refer to the exhibit.
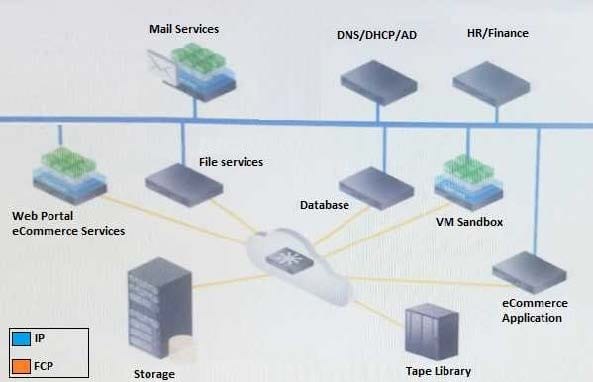
Your company is currently using a traditional SAN storage network. The server infrastructure is partially virtualized. There is a public cloud in place that is used to test development and application migration to cloud.
Business requirements:
Consolidate the network, storage, and compute resources Simplify network management and storage provisioning Maintain application performance
Need to share resources to reduce cost and improve efficiency Other considerations:
Monitoring of protection SLAs
All transactions must be logged for auditing review
Users are validated using internal credentials
Refer to Case 4.
You are designing a transformation from Platform 2.0 to cloud. You review the existing infrastructure and business requirements. You must detect events that can exploit vulnerabilities in the cloud. Which technology
should you select?
A. ISO
B. PCI DSS
C. Firewall
D. IDPS
Case 1
Refer to the exhibit.
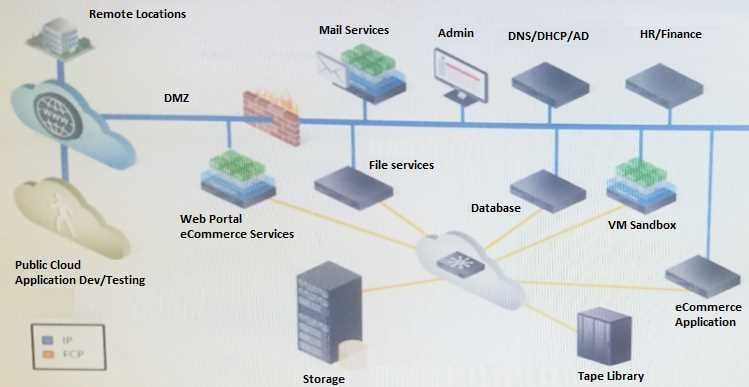
Your company recently negotiated several contracts with new customers to use its proprietary eCommerce system. As a result, the customer base has grown rapidly, which has introduced several challenges and requirements.
Business requirements:
Applications need to scale quickly
Metrics and reporting to anticipate business trends and efficient use of resources External customers are looking to license the eCommerce application Other considerations:
Applications need to be recorded for the public cloud
Address security vulnerabilities for customer data in the cloud Refer to Case 1.
You are designing a Do-It-Yourself private cloud solution. What is the recommended way to provide applications the ability to scale quickly?
A. Increase the overall resource capacity of the system
B. Restrict the component choices to within a single vendor
C. Validate new element compatibility against the SSM
D. Ensure the IT staff understands the configuration options
Which benefits might be realized by designing a separate infrastructure pool to host network functions?
A. Reduced public IP address consumption, reduced troubleshooting time, and reduced consumer infrastructure load
B. Reduced troubleshooting time, reduced consumer infrastructure load, and enhanced security
C. Reduced troubleshooting time, enhanced security, and reduced public IP address consumption
D. Reduced consumer infrastructure load, enhanced security, and reduced public IP address consumption
Which services are typically offered by cloud service providers?
A. Bundled storage, applications, operating systems
B. Operating environment, virtualization, applications
C. Software, platform, infrastructure
D. Compute, storage, connectivity