DEA-41T1 Online Practice Questions and Answers
DRAG DROP
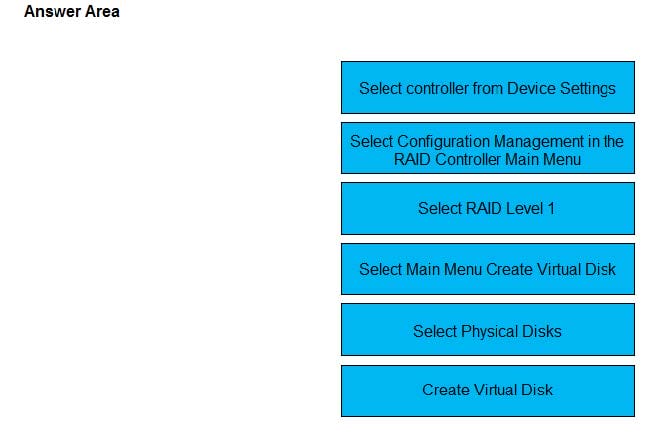
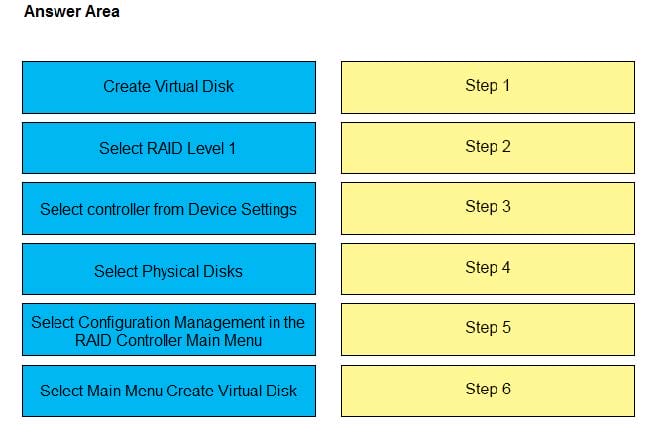
An administrator needs to configure RAID 1 in System Setup.
Place the sequence in the correct order.
Select and Place:
What is the Dell EMC iSM?
A. Agent that expands iDRAC management functionality into the host operating system
B. Program that is installed and provides one-to-one systems management functionality
C. Systems management console that simplifies monitoring of multiple Dell EMC servers
D. Out-of-band management platform on Dell EMC servers
For which use case is Dell EMC OpenManage Essentials recommended for installation?
A. Comprehensive, one-to-one systems management solution for remote or local servers
B. Management console for one-to-many monitoring of Dell EMC infrastructure
C. Operation of hardware while iDRAC is non-functional
D. Management and integration of operating system updates across an entire environment
What is the purpose of the DNS role?
A. Send out emails from a server to a client
B. Translate domain names into IP address
C. transfer computer files between a client and a server
D. Distribute and update dynamic IP address
Which solution is recommended for installing a hypervisor in a Dell EMC PowerEdge rack server or in a hyper-converged infrastructure (HCI) host?
A. FC HBA
B. BOSS
C. CPU
D. NVDIMM
What benefit is offered by modular servers over rack servers?
A. Lower power requirements result in lower datacenter operating costs.
B. Higher density is achieved by reducing the amount of consumed rack space
C. Hot replacement of any server in the enclosure is possible
D. All hardware technology is integrated into a single circuit board
An administrator wishes to create a complex RAID set for a high-performance database, where the value of the data far exceeds the cost of the drives. Which complex RAID level should be used?
A. RAID 1
B. RAID 10
C. RAID 50
D. RAID 60
An administrator needs to set up a RAID which requires high performance but no data protection. Which RAID level fulfills these requirements?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 6
An administrator wants to enable Lifecycle Controller log replication into the operating system. Which tool can accomplish this?
A. SAE
B. OME
C. PERC CLI
D. iSM
An administrative user sends a Word document as an attachment to their coworker using the email client. Which protocol is used to complete this transaction?
A. SMTP
B. SNMP
C. SFTP
D. SCTP