DEA-1TT4 Online Practice Questions and Answers
DRAG DROP
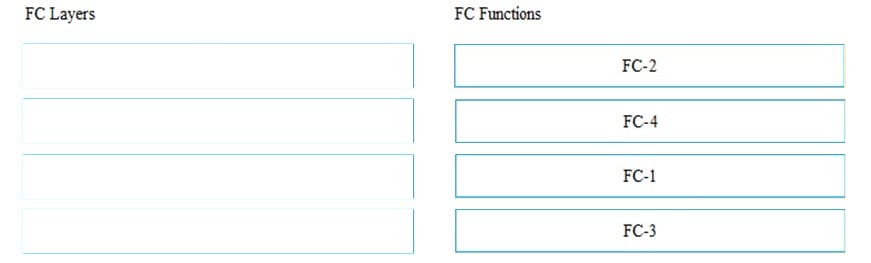
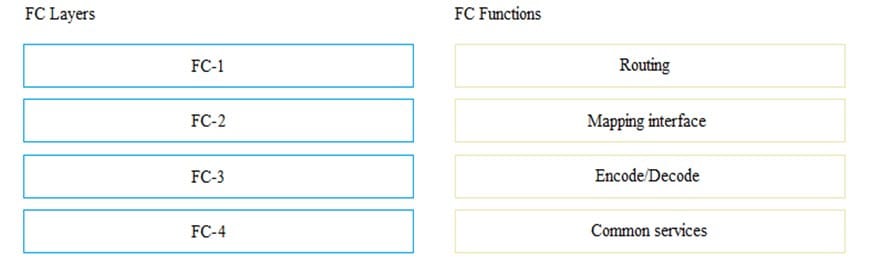
Match the Fibre Channel (FC) Layers with their respective functions.
Select and Place:
DRAG DROP
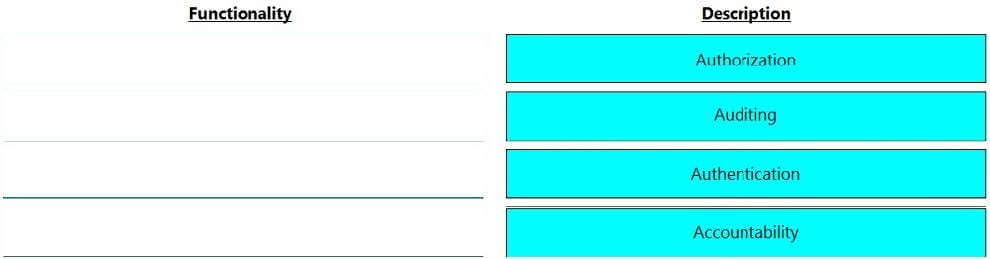
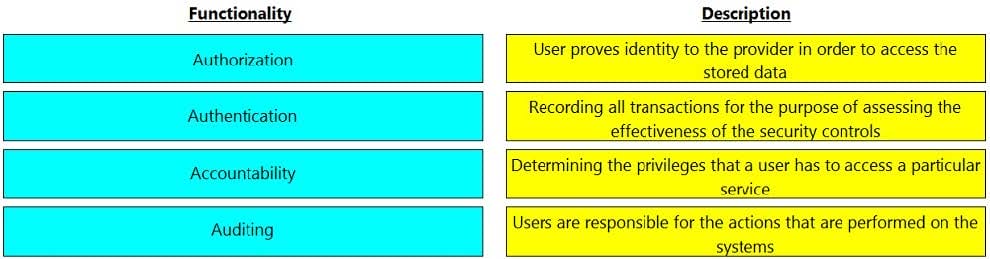
Match the functionality of a security goal with its description.
Select and Place:
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events. Which IDPS technique uses a database that contains known attack patterns?
A. Role-based
B. Profile-based
C. Signature-based
D. Anomaly-based
Which Dell EMC product is a hyper-scale storage infrastructure that provides universal accessibility with support for object and HDFS?
A. ViPR Controller
B. PowerMax
C. Isilon
D. Elastic Cloud Storage
Which functionality does a Control layer provide in a software-defined networking architecture?
A. Defining the network behavior through various policies.
B. Making decisions on how the packets should be forwarded.
C. Establishing communications between the Infrastructure and Interface layers.
D. Forwarding data packets based on the requirements from the Application layer.
When using a bridged iSCSI connection, which components facilitate communication between gateways?
A. Compute system with iSCSI ports and the storage system with Ethernet ports.
B. Compute system with iSCSI ports and the storage system with only FC ports.
C. Compute system with FC HBA ports and the storage system with only FC ports.
D. Compute system with FCoE ports and the storage system with iSCSI ports.
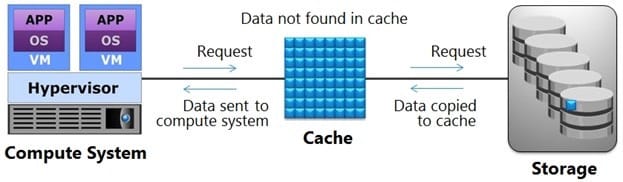
Which operation is represented in the exhibit?
A. Write-back Cache
B. Read Cache Miss
C. Write-through Cache
D. Read Cache Hit
Why is it important to deploy virtual machine (VM) storage migration in a data center environment?
A. Enable efficient management of storage capacity across storage systems
B. Improve the security of applications running inside VMs on the migrated storage system
C. Reduce a company's overall storage system capacity requirements
D. Enable VMs to continue functioning even if the source data is lost due to a failure
A company has virtualized their data center and wants to deploy a recovery-in-place backup approach. What is the advantage of this type of approach?
A. Acquires backup services through a self-service portal
B. Eliminates the backup impact on the application servers
C. Reduces the recovery point objective to restore the data to any previous point-in-time using backed up VMs
D. Eliminates the need to transfer the image from the backup device to the primary storage before it is restarted