D-ISM-FN-23 Online Practice Questions and Answers
In a data archiving environment, which component scans primary storage to nd the les that are required to archive?
A. Archive stub le
B. Archive agent
C. Archive storage
D. Archive database server
Which is a characteristic of RAID 6?
A. Double parity
B. Single parity
C. All parity stored on a single disk
D. Parity not used
What is an accurate statement about data shredding?
A. A process to encrypt data
B. A process to decrypt data
C. A process to delete data
D. A process to reorganize data
What is an accurate statement about scale-out NAS?
A. Creates a different le system for each node in the cluster
B. Pools node resources in a cluster to work as multiple NAS devices
C. Increases performance and capacity by adding nodes to the cluster
D. Supports only data replication for protecting data across the nodes
Refer to the Exhibit:
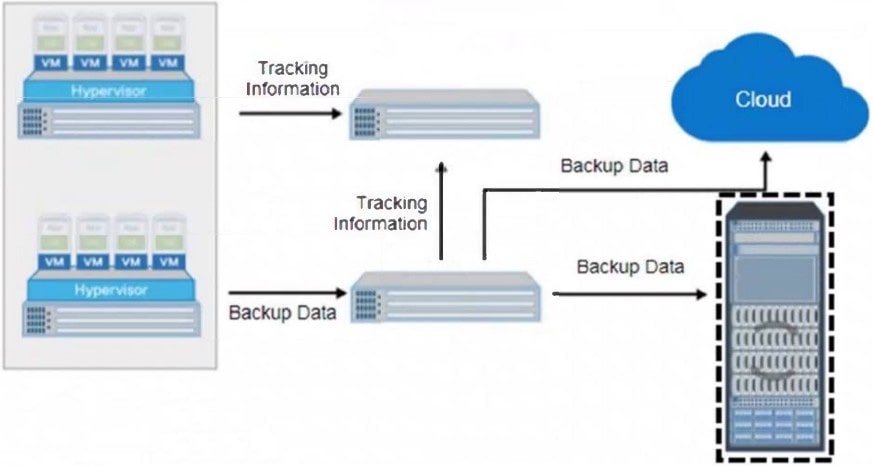
What is the name of the selected backup architecture component?
A. Backup Device
B. Storage Node
C. Backup Client
D. Backup Server
An organization has two data centers separated by a distance of 1600 km. They want to replicate between these data centers for disaster recovery purposes. They are concerned that this will impact application response time.
Which solution will address this concern?
A. Asynchronous remote replication
B. Storage-based COFW snapshot replication
C. Synchronous remote replication
D. Storage-based ROW snapshot replication
Which components comprise a Fibre Channel SAN?
A. TOE HBA Gateways CAT6 cables
B. FC HBA Switches Fiber optic cables
C. FC HBA Gateways Fiber optic cables
D. TOE HBA Switches CAT6 cables
Which performance feature does an intelligent storage system provide?
A. RAID 4 data protection
B. End-to-end SAS storage connectivity
C. Automated storage tiering
D. End-to-end NVMe/IB storage connectivity
An organization wants to replicate their data by extending the local network across a public network. Prior to implementing replication, they need to secure the network. Which security control mechanism is recommended?
A. Virtual storage area network
B. Demilitarized zone
C. Virtual local area network
D. Virtual private network
What method does FCIP use to transport Fibre Channel SAN data?
A. FCIP encapsulates and tunnels FC SAN data over Ethernet networks.
B. FCIP encapsulates and tunnels FC SAN data over IP networks.
C. FCIP splits LAN and FC SAN data and tunnels FC SAN data over Ethernet networks.
D. FCIP separates LAN and FC SAN data and tunnels FC SAN data over IP networks.

