CV0-004 Online Practice Questions and Answers
SIMULATION
You are a cloud engineer working for a cloud service provider that is responsible for an IaaS offering.
Your customer, who creates VMs and manages virtual storage, has noticed I/O bandwidth issues and low IOPS (under 9000).
Your manager wants you to verify the proper storage configuration as dictated by your service level agreement (SLA).
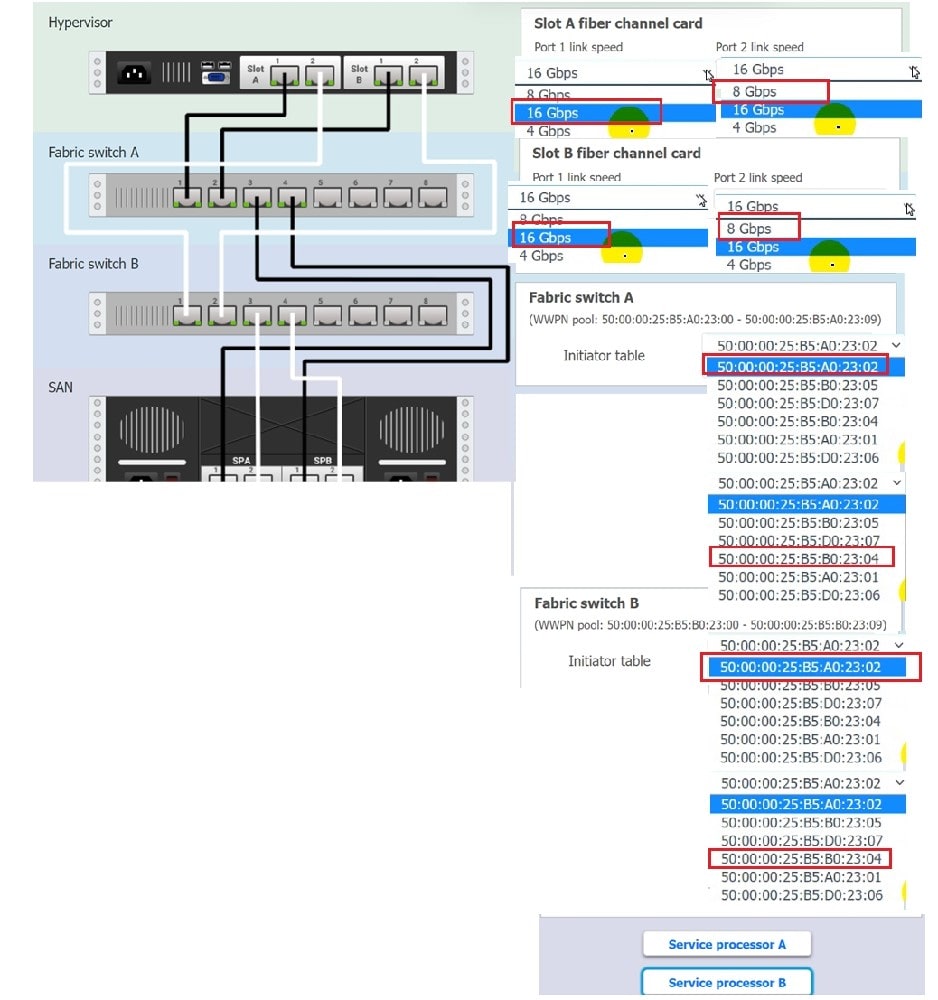
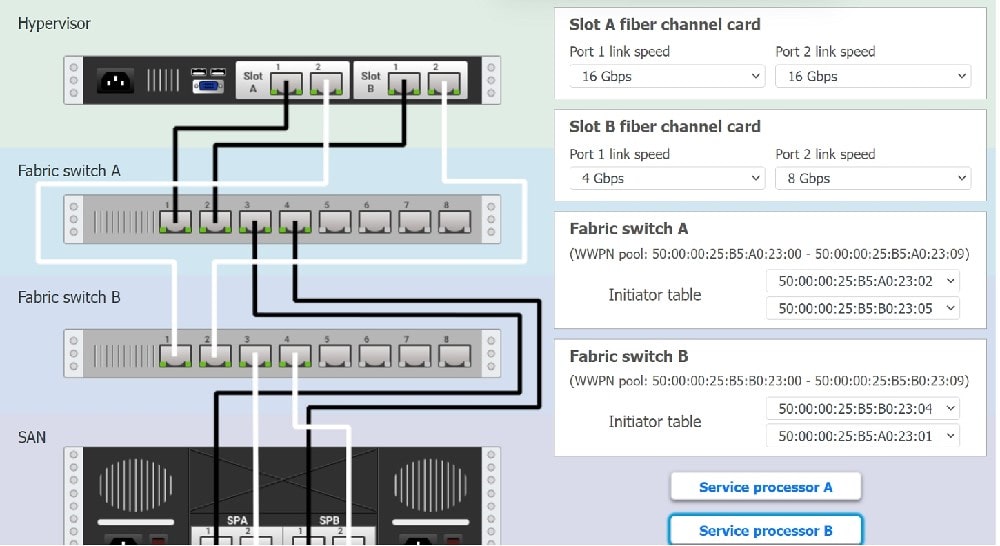
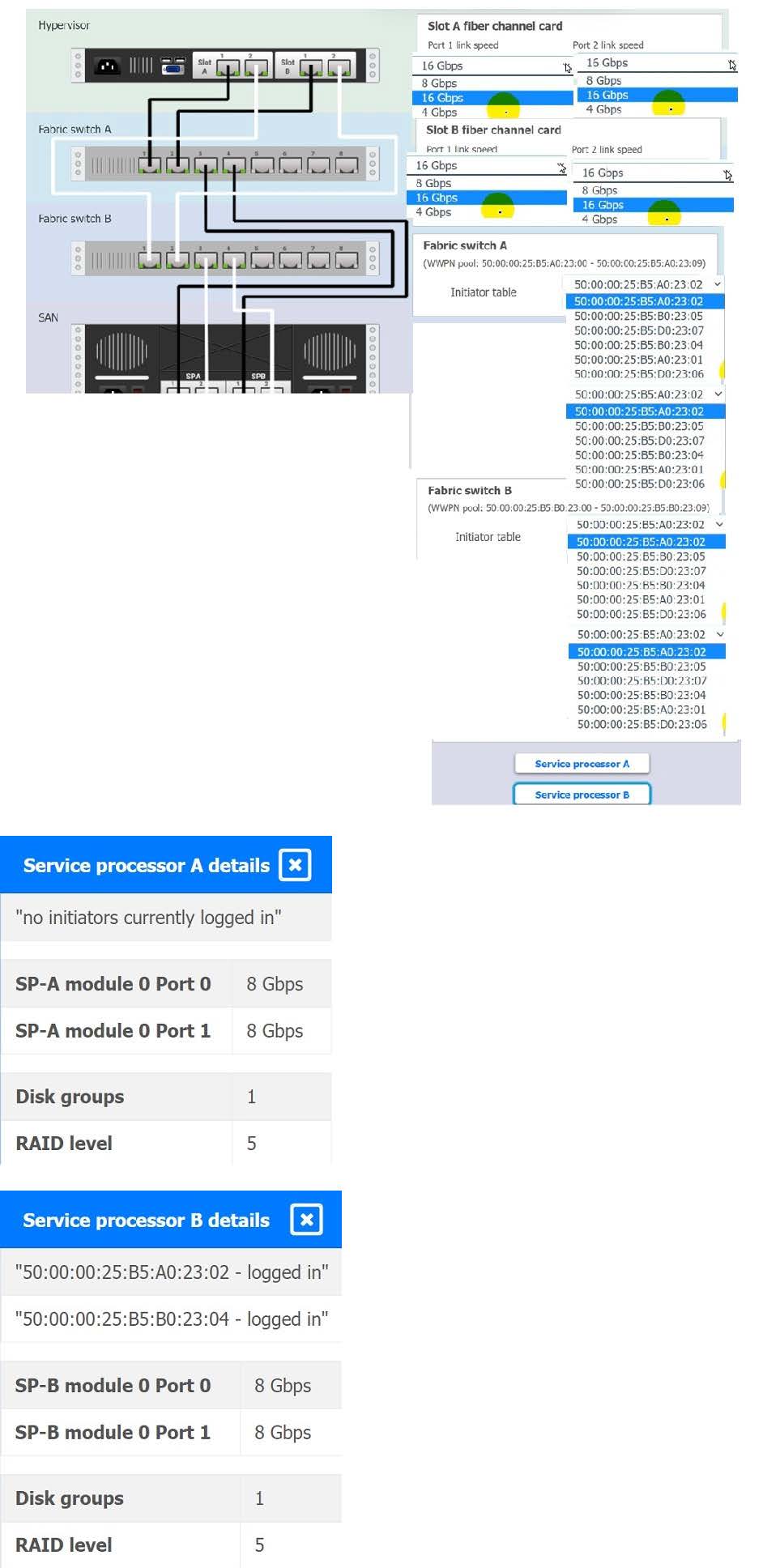
The SLA specifies:
1.
Each SFP on the hypervisor host must be set to the maximum link speed allowed by the SAN array. . All SAN array disk groups must be configured in a RAID 5.
2.
The SAN array must be fully configured for redundant fabric paths. . IOPS should not fall below 14000 INSTRUCTIONS Click on each service processor to review the displayed information. Then click on the drop-down menus to change the settings of each device as necessary to conform to the SLA requirements.
A. See the explanation for complete solution.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
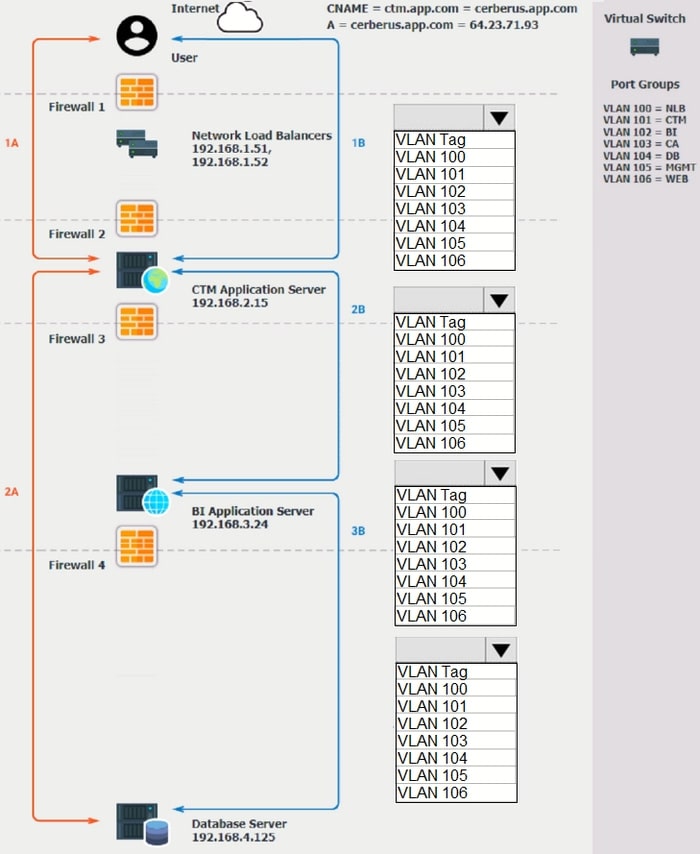
HOTSPOT
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
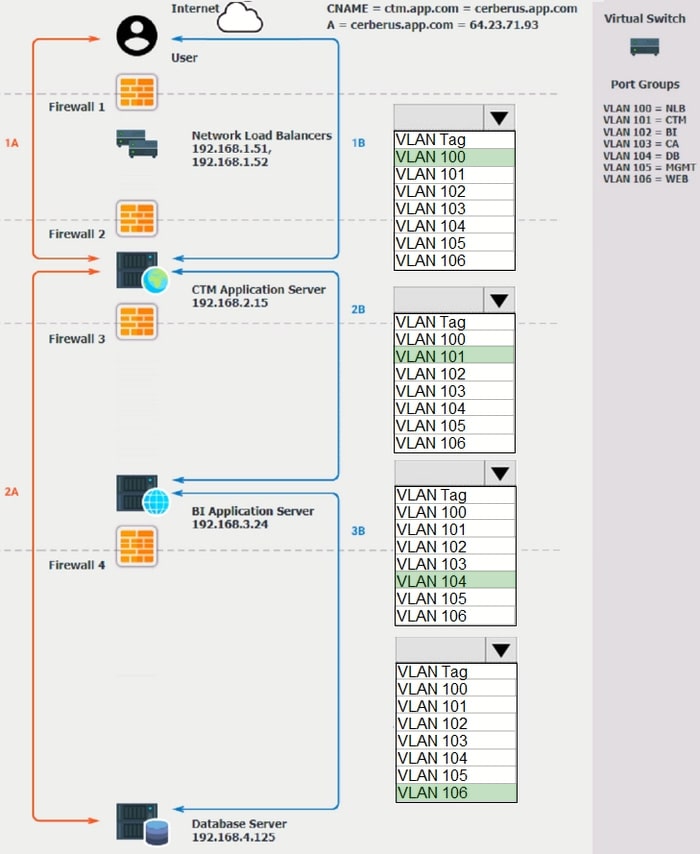
Refer to the application dataflow:
1.
1A -The end user accesses the application through a web browser to enter and view clinical data.
2.
2A -The CTM application server reads/writes data to/from the database server.
3.
1B -The end user accesses the application through a web browser to run reports on clinical data.
4.
2B -The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
5.
3B -The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: "Browser cannot display the webpage." The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
Which of the following are best practices when working with a source control system? (Select two).
A. Merging code often
B. Pushing code directly to production
C. Performing code deployment
D. Maintaining one branch for all features
E. Committing code often
F. Initiating a pull request
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage.
Which of the following best describes the nature of the local storage?
A. Persistent
B. Ephemeral
C. Differential
D. Incremental
A bank informs an administrator that changes must be made to backups for long-term reporting purposes.
Which of the following is the most important change the administrator should make to satisfy these requirements?
A. Location of the backups
B. Type of the backups
C. Retention of the backups
D. Schedule of the backups
Users report being unable to access an application that uses TLS 1.1. The users are able to access other applications on the internet.
Which of the following is the most likely reason for this issue?
A. The security team modified user permissions.
B. Changes were made on the web server to address vulnerabilities.
C. Privileged access was implemented.
D. The firewall was modified.
A company's content management system (CMS) service runs on an laaS cluster on a public cloud. The CMS service is frequently targeted by a malicious threat actor using DDoS.
Which of the following should a cloud engineer monitor to identify attacks?
A. Network flow logs
B. Endpoint detection and response logs
C. Cloud provider event logs
D. Instance syslog
A cloud administrator needs to implement a mechanism to monitor the expense of the company's cloud resources.
Which of the following is the BEST option to execute this task with minimal effort?
A. Ask the cloud provider to send a daily expense report
B. Set custom notifications for exceeding budget thresholds
C. Use the API to collect expense information from cloud resources
D. Implement a financial tool to monitor cloud resource expenses
Which of the following enables CSPs to offer unlimited capacity to customers?
A. Adequate budget
B. Global data center distribution
C. Economies of scale
D. Agile project management
A cloud administrator who is troubleshooting DNS issues discovers zone transfers are not occurring between the primary and secondary name servers due to an error in the serial numbers.
Which of the following records should the administrator query for the serial number?
A. PTR
B. TXT
C. SOA
D. SRV