CV0-003 Online Practice Questions and Answers
A company wants to check its infrastructure and application for security issues regularly. Which of the following should the company implement?
A. Performance testing
B. Penetration testing
C. Vulnerability testing
D. Regression testing
A company recently experienced a power outage that lasted 30 minutes. During this time, a whole rack of servers was inaccessible, even though the servers did not lose power. Which of the following should be investigated FIRST?
A. Server power
B. Rack power
C. Switch power
D. SAN power
A new private cloud platform is being deployed by an engineer. SLA requirements state that any clusters should have a baseline redundancy sufficient to handle the failure of at least two hosts. The engineer records the following metrics after the deployment:
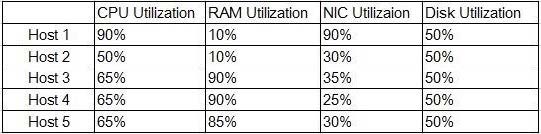
Which of the following metrics is MOST likely to represent a violation of SLA?
A. RAM utilization
B. NIC utilization
C. CPU utilization
D. Disk utilization
The CASB report indicates several unsanctioned SaaS applications are being used in an organization. Which of the following is the MOST likely cause?
A. VPN bypass
B. Shadow IT
C. Web proxy bypass
D. CAB approval
A systems administrator adds servers to a round-robin, load-balanced pool, and then starts receiving reports of the website being intermittently unavailable. Which of the following is the MOST likely cause of the issue?
A. The network is being saturated.
B. The load balancer is being overwhelmed.
C. New web nodes are not operational.
D. The API version is incompatible.
E. There are time synchronization issues.
A company would like to migrate its current on-premises workloads to the public cloud. The current platform requires at least 80 instances running at all times to work properly. The company wants the workload to be highly available, even if the cloud provider loses one region due to a catastrophe, and the costs to be kept to a minimum. Which of the following strategies should the company implement?
A. Create /25 subnets in two regions and run 80 instances on each one.
B. Create /26 subnets in two regions and run 40 instances on each one.
C. Create /26 subnets in three regions and run 40 instances on each one
D. Create /26 subnets in three regions and run 80 instances on each one.
A systems administrator has verified that a physical switchport that is connected to a virtualization host is using all available bandwidth. Which of the following would BEST address this issue?
A. Port mirroring
B. Link aggregation
C. Spanning tree
D. Microsegmentation
A cloud administrator is reviewing the current private cloud and public law environment, and is building an optimization plan. Portability is of great concern for the administrator so resources can be easily moved from one environment to another. Which of the following should the administrator implement?
A. Serverless
B. CDN
C. Containers
D. Deduplication
A systems administrator is responsible for upgrading operating systems on VMs that are hosted in a cloud environment. The systems administrator wants to ensure the VMs receive updates for as long as possible. Which of the following should the systems administrator choose?
A. Stable
B. Nightly
C. LTS
D. Canary
E. EDR
A company that performs passive vulnerability scanning at its transit VPC has detected a vulnerability related to outdated web-server software on one of its public subnets. Which of the following can the company use to verify if this is a true positive with the least effort and cost? (Select two).
A. A network-based scan
B. An agent-based scan
C. A port scan
D. A red-team exercise
E. A credentialed scan
F. A blue-team exercise
G. Unknown environment penetration testing

