CSQA Online Practice Questions and Answers
Which of the following is the correct definition of the Quality Attribute Maintainability?
A. Effort required to ensure that the system performs as its intended
B. Effort required to locate and fix an error in an operational system
C. Extent to which a program satisfies its specifications
D. Extent to which a program can be expected to perform its intended function
E. None of the above
Capability Maturity Model(s) (CMMs) are defined and managed by:
A. Software Engineering Institute
B. Malcolm Baldrige Organization
C. International Standards Organization
D. Quality Assurance Institute
Determining which risks are likely to affect the project and documenting the characteristics of each is called ________ .
A. Risk Assessment
B. Risk Management
C. Risk
D. Risk Identification
Measurement provides ____________ feedback to an organization about whether it is achieving its goals.
A. Qualitative
B. Subjective
C. Objective
D. Quantitative
Determining that the COTS software selected is compatible with the acquiring organization's computer environment addresses:
A. Compatibility with other COTS software packages
B. Compatibility with the acquiring organization's computer language
C. Compatibility with the SEI CMMI level of the organization that built the COTS software
D. Compatibility of the acquiring organization's acceptance test process
E. Compatibility with the acquiring organization's hardware and operating system
When auditors are engaged by the Board of Directors to audit an organization is an example of ____________.
A. Supervisor Monitoring
B. Peer Monitoring
C. Ongoing Monitoring
D. Independent Monitoring
The team for establishing a security baseline should consist of:
A. Individuals responsible for computer security
B. Auditors for internal control activities
C. Senior management
D. All employees
Which of the following three questions would NOT be answered by establishing a security baseline?
A. What are we doing about computer security?
B. How effective is our computer security program?
C. Who is responsible for software system security?
Cause-and-effect graphing is a tool used to:
A. Trace requirements
B. Help determine root causes of problems in processes
C. Determine what requirements have been covered
D. Graph defects uncovered by cause
E. Identifies the routines in which errors occur
-- Exhibit
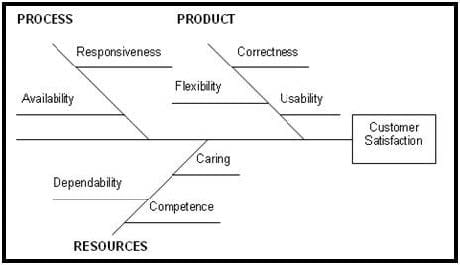
-- Exhibit -The diagram is an example of a(n):
A. Process Map Diagram
B. Affinity Diagram
C. Force Field Diagram
D. Flowchart
E. Cause-and-Effect Diagram

