CEH-001 Online Practice Questions and Answers
Which of the following type of scanning utilizes automated process of proactively identifying vulnerabilities of the computing systems present on a network?
A. Port Scanning
B. Single Scanning
C. External Scanning
D. Vulnerability Scanning
Peter extracts the SID list from Windows 2008 Server machine using the hacking tool "SIDExtracter". Here is the output of the SIDs:
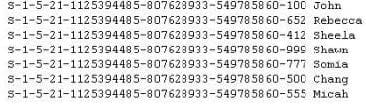
From the above list identify the user account with System Administrator privileges?
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah
Take a look at the following attack on a Web Server using obstructed URL:
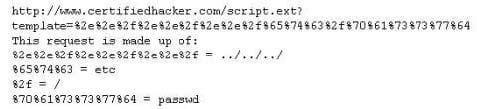
How would you protect from these attacks?
A. Configure the Web Server to deny requests involving "hex encoded" characters
B. Create rules in IDS to alert on strange Unicode requests
C. Use SSL authentication on Web Servers
D. Enable Active Scripts Detection at the firewall and routers
Which element of Public Key Infrastructure (PKI) verifies the applicant?
A. Certificate authority
B. Validation authority
C. Registration authority
D. Verification authority
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
A. Packet filtering firewall
B. Application-level firewall
C. Circuit-level gateway firewall
D. Stateful multilayer inspection firewall
User which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
A. 18 U.S.C 1029 Possession of Access Devices
B. 18 U.S.C 1030 Fraud and related activity in connection with computers
C. 18 U.S.C 1343 Fraud by wire, radio or television
D. 18 U.S.C 1361 Injury to Government Property
E. 18 U.S.C 1362 Government communication systems
F. 18 U.S.C 1831 Economic Espionage Act
G. 18 U.S.C 1832 Trade Secrets Act
Which Type of scan sends a packets with no flags set? Select the Answer
A. Open Scan
B. Null Scan
C. Xmas Scan
D. Half-Open Scan
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
A. Hardware, Software, and Sniffing.
B. Hardware and Software Keyloggers.
C. Passwords are always best obtained using Hardware key loggers.
D. Software only, they are the most effective.
After studying the following log entries, how many user IDs can you identify that the attacker has tampered with?
1.
mkdir -p /etc/X11/applnk/Internet/.etc
2.
mkdir -p /etc/X11/applnk/Internet/.etcpasswd
3.
touch -acmr /etc/passwd /etc/X11/applnk/Internet/.etcpasswd
4.
touch -acmr /etc /etc/X11/applnk/Internet/.etc
5.
passwd nobody -d
6.
/usr/sbin/adduser dns -d/bin -u 0 -g 0 -s/bin/bash
7.
passwd dns -d
8.
touch -acmr /etc/X11/applnk/Internet/.etcpasswd /etc/passwd
9.
touch -acmr /etc/X11/applnk/Internet/.etc /etc
A. IUSR_
B. acmr, dns
C. nobody, dns
D. nobody, IUSR_
What is Cygwin?
A. Cygwin is a free C++ compiler that runs on Windows
B. Cygwin is a free Unix subsystem that runs on top of Windows
C. Cygwin is a free Windows subsystem that runs on top of Linux
D. Cygwin is a X Windows GUI subsytem that runs on top of Linux GNOME environment

