CAS-005 Online Practice Questions and Answers
SIMULATION
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.


A. See the complete solution below in Explanation.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
SIMULATION
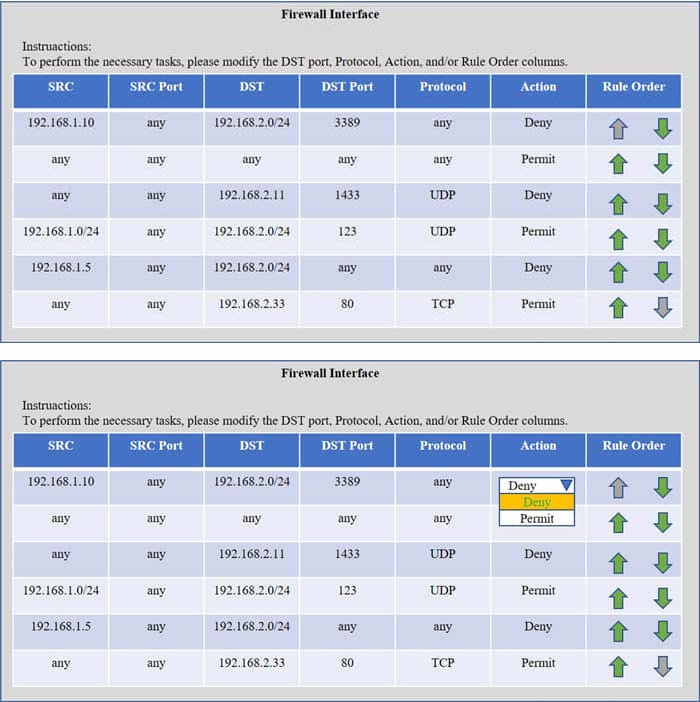
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more
restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24 Server Subnet: 192.168.2.0/24 Finance Subnet:192.168.3.0/24
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down
Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.
Check the solution below.
A. See the complete solution below in Explanation.
B. PlaceHoder
C. PlaceHoder
D. PlaceHoder
A cloud engineer needs to identify appropriate solutions to:
1.
Provide secure access to internal and external cloud resources.
2.
Eliminate split-tunnel traffic flows.
3.
Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).
A. Federation
B. Microsegmentation
C. CASB
D. PAM
E. SD-WAN
F. SASE
A systems engineer is configuring a system baseline for servers that will provide email services. As part of the architecture design, the engineer needs to improve performance of the systems by using an access vector cache, facilitating mandatory access control and protecting against:
1.
Unauthorized reading and modification of data and programs
2.
Bypassing application security mechanisms
3.
Privilege escalation
4.
interference with other processes
Which of the following is the most appropriate for the engineer to deploy?
A. SELinux
B. Privileged access management
C. Self-encrypting disks
D. NIPS
A company recently experienced an incident in which an advanced threat actor was able to shim malicious code against the hardware static of a domain controller The forensic team cryptographically validated that com the underlying firmware of the box and the operating system had not been compromised. However, the attacker was able to exfiltrate information from the server using a steganographic technique within LOAP
Which of the following is me best way to reduce the risk oi reoccurrence?
A. Enforcing allow lists for authorized network pons and protocols
B. Measuring and attesting to the entire boot chum
C. Rolling the cryptographic keys used for hardware security modules
D. Using code signing to verify the source of OS updates
A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks.
Which of the following most directly supports the administrator's objective'
A. improving security dashboard visualization on SIEM
B. Rotating API access and authorization keys every two months
C. Implementing application toad balancing and cross-region availability
D. Creating WAF policies for relevant programming languages
A security operations engineer needs to prevent inadvertent data disclosure when encrypted SSDs are reused within an enterprise.
Which of the following is the most secure way to achieve this goal?
A. Executing a script that deletes and overwrites all data on the SSD three times
B. Wiping the SSD through degaussing
C. Securely deleting the encryption keys used by the SSD
D. Writing non-zero, random data to all cells of the SSD
After investigating a recent security incident, a SOC analyst is charged with creating a reference guide for the entire team to use. Which of the following should the analyst create to address future incidents?
A. Root cause analysis
B. Communication plan
C. Runbook
D. Lessons learned
A security analyst is reviewing suspicious emails that were forwarded by users. Which of the following is the best method for the analyst to use when reviewing attachments that came with these emails?
A. Reverse engineering
B. Protocol analysis
C. Sandboxing
D. Fuzz testing
E. Steganography
A security architect is reviewing the following organizational specifications for a new application:
1.
Be sessionless and API-based
2.
Accept uploaded documents with PII, so all storage must be ephemeral
3.
Be able to scale on-demand across multiple nodes
4.
Restrict all network access except for the TLS port
Which of the following ways should the architect recommend the application be deployed in order to meet security and organizational infrastructure requirements?
A. Utilizing the cloud container service
B. On server instances with autoscaling groups
C. Using scripted delivery
D. With a content delivery network

