CAS-004 Online Practice Questions and Answers
SIMULATION
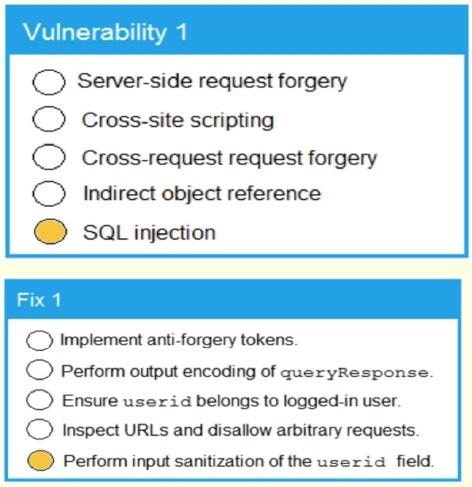
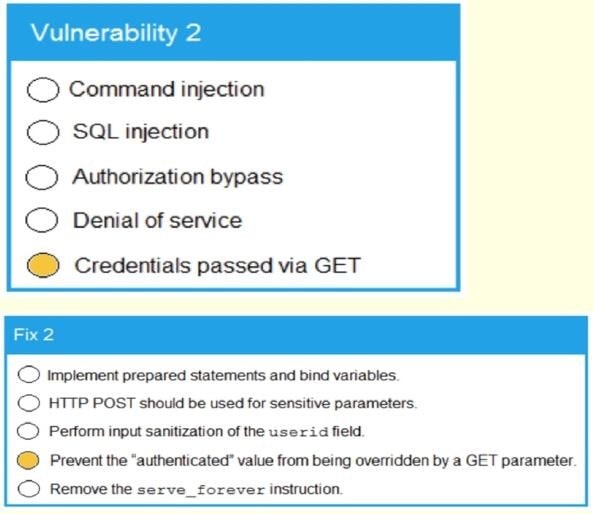
A product development team has submitted code snippets for review pnor to release INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
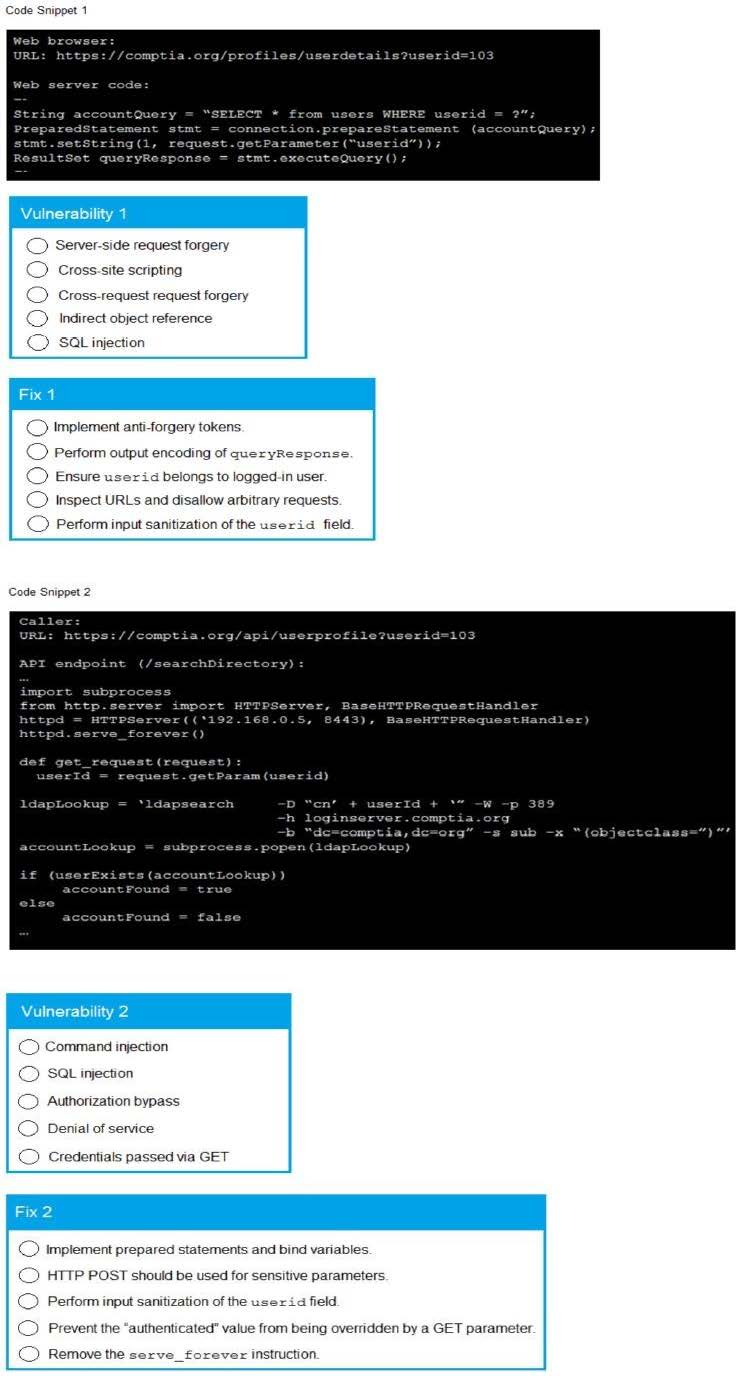
A. Check the answer in explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
A security architect is implementing a web application that uses a database back end. Prior to the production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks.
Which of the following sources could the architect consult to address this security concern?
A. SDLC
B. OVAL
C. IEEE
D. OWASP
A recent data breach revealed that a company has a number of files containing customer data across its storage environment. These files are individualized for each employee and are used in tracking various customer orders, inquiries, and issues. The files are not encrypted and can be accessed by anyone. The senior management team would like to address these issues without interrupting existing processes.
Which of the following should a security architect recommend?
A. A DLP program to identify which files have customer data and delete them
B. An ERP program to identify which processes need to be tracked
C. A CMDB to report on systems that are not configured to security baselines
D. A CRM application to consolidate the data and provision access based on the process and need
While traveling to another state, the Chief Financial (CFO) forgot to submit payroll for the company. The CFO quickly gained to the corporate through the high-speed wireless network provided by the hotel and completed the desk. Upon returning from the business trip, the CFO was told no one received their weekly pay due to a malware on attack on the system.
Which of the following is the MOST likely of the security breach?
A. The security manager did not enforce automate VPN connection.
B. The company's server did not have endpoint security enabled.
C. The hotel and did require a wireless password to authenticate.
D. The laptop did not have the host-based firewall properly configured.
A company has decided that only administrators are permitted to use PowerShell on their Windows computers. Which of the following is the BEST way for an administrator to implement this decision?
A. Monitor the Application and Services Logs group within Windows Event Log.
B. Uninstall PowerShell from all workstations.
C. Configure user settings In Group Policy.
D. Provide user education and training.
E. Block PowerShell via HIDS.
In a shared responsibility model for PaaS, which of the following is a customer's responsibility?
A. Network security
B. Physical security
C. OS security
D. Host infrastructure
When a remote employee traveled overseas, the employee's laptop and several mobile devices with proprietary tools were stolen. The security team requires technical controls be in place to ensure no electronic data is compromised or changed. Which of the following BEST meets this requirement?
A. Mobile device management with remote wipe capabilities
B. Passwordless smart card authorization with biometrics
C. Next-generation endpoint detection and response agent
D. Full disk encryption with centralized key management
A security team is concerned with attacks that are taking advantage of return-oriented programming against the company's public facing applications. Which of the following should the company implement on the public-facing servers?
A. WAF
B. ASLR
C. NX
D. HSM
After installing an unapproved application on a personal device, a Chief Executive Officer reported an incident to a security analyst. This device is not controlled by the MDM solution, as stated in the BVOD policy. However, the device contained critical confidential information. The cyber incident response team performed the analysis on the device and found the following log:
Wed 12 Dec 2020 10:00:03 Unknown sources is now enabled on this device.
Which of the following is the MOST likely reason for the successful attack?
A. Lack of MDM controls
B. Auto-join hotspots enabled
C. Sideloading
D. Lack of application segmentation
When implementing serverless computing, an organization must still account for:
A. the underlying computing network infrastructure.
B. hardware compatibility.
C. the security of its data.
D. patching the service.